Revision of J3Gen and Validity of the Attacks by Peinado et al.
Abstract
:1. Introduction
2. Concerning the Probabilistic Attack
3. Concerning the Deterministic Attack
- “The list of polynomials (no matter the value of l) would never be applied as suggested in [2]”.
- “The value l = 1 is not feasible in practice”.
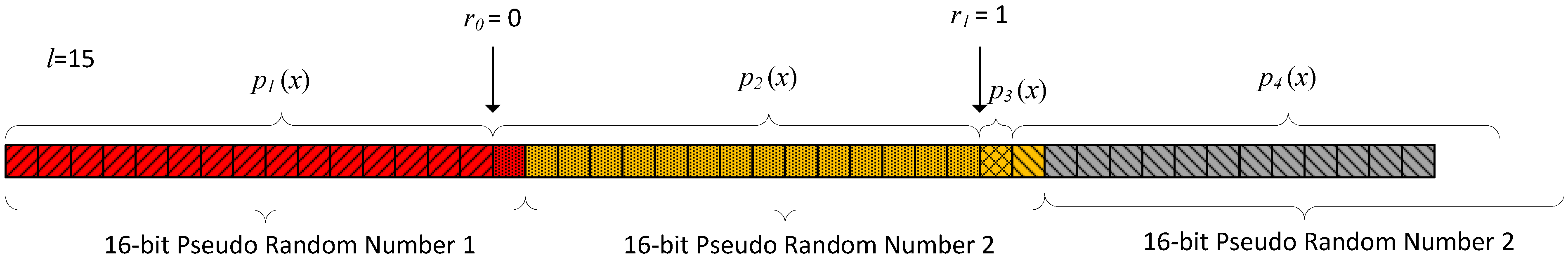
- Section 3 of [3] provides, according to the authors, a detailed step by step sample execution of the scheme for the generation of 32 output bits with n = 16, m = 8 and l = 15. It explains (sic): “The system starts with p(x)1 and outputs l = 15 bits until the TRNG module transfers a bit with value r0 = 0 to the Decoding Logic module. Then, a consecutive (but different) feedback polynomial is selected in the Polynomial Selector module, that is, p2(x). This generates the next l = 15 LFSR shifts with p2(x) until the next trn is obtained. The trn value for this PRNG update is r1 = 1, hence, the Decoding Logic rotates the Polynomial Selector one position at shift 31, and another position at shift 32. Then, p2(x) is used 14 cycles, p3(x) is used one cycle, and p4(x) is used one cycle in this PRNG update and 14 cycles in the next PRNG update”.
| l=15 | l=1 | ||||
| trn | Polynomial | Action | trn | Polynomial | Action |
| p1(x) | Generate 15 (=l) bits | p1(x) | Generate 1 (=l) bits | ||
| 0 | 0 | ||||
| p2(x) | Generate 15 (=l) bits | p2(x) | Generate 1 (=l) bits | ||
| 1 | 1 | ||||
| p3(x) | Generate 1 bit | p3(x) | Generate 1 bit | ||
| p4(x) | Generate 15 (=l) bit | p4(x) | Generate 1 (=l) bit | ||
- Melià-Seguí et al. [1] claim that “the clock signals controlling J3Gen (i.e., the LFSR clock, as well as the clock of the physical source of randomness, and the one controlling the selection of polynomials) are not synchronized”. We can understand that activation and deactivation timings can be different but all of them should be controlled by the same single master clock. EPCGen2 tags do not have on-board clocks and they recover the clock signal from the reader’s carrier. The presence therefore of three independent clock signals requires further explanations.
- In their letter [1], the deterministic attack is said not to be feasible in practice because the value l = 1 is only given as a boundary and in this case J3Gen could simply output the true random sequences from the thermal-noise generator. We cannot say that the authors did not have this in mind when they described J3Gen, but at leat, it does not seem to coincide with that written in the original papers where the value l = 1 is not only included in the analysis, but also suggested to increase the security of the system. In particular, it says “Depending on the level of desired security, l can be bounded by 1 ≤ l < n”, and follows “Here, the attacker has to face with the uncertainty added by the feedback update rate (l). For example, using the selected parameters n = 32 and m = 16, if l = 31 it means there would be up to 4 possible solutions for each system of equations. If l = 25 then the possible solutions are up to 16,384, for l = 21 the possible solutions increase to 4,194,304, etc. The extreme case would be l = 1 where all 67 million primitive feedback polynomials would be equally probable". Thus, if the authors thought that the value l = 1 could not be applied by practical reasons, they should have clarified the complete range of values that should be excluded by practical reasons (in the letter the authors say that it is explained in previous papers but we have not found any reference to this).
4. Additional Remarks
5. Conclusions
- clarify the aspects above mentioned,
- describe new examples of generation of random numbers that justify their arguments,
- provide clear secure ranges for the parameters of the protocol since low values of l are not practical,
- review all the security claims.
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Garcia-Alfaro, J.; Herrera-Joancomartí, J.; Melià-Seguí, J. Remarks on Peinado et al.’s Analysis of J3Gen. Sensors 2015, 15, 6217–6220. [Google Scholar] [CrossRef] [PubMed]
- Peinado, A.; Munilla, J.; Fúster-Sabater, A. EPCGen2 Pseudorandom Number Generators: Analysis of J3Gen. Sensors 2014, 14, 6500–6515. [Google Scholar] [CrossRef] [PubMed]
- Melià-Seguí, J.; Garcia-Alfaro, J.; Herrera-Joancomartí, J. Multiple-polynomial LFSR based pseudorandom number generator for EPC Gen2 RFID tags. In Proceedings of 37th Annual Conference on IEEE Industrial Electronics Society (IECON 2011), Melbourne, Australia, 7–10 November 2011; pp. 3820–3825.
- Melià-Seguí, J.; Garcia-Alfaro, J.; Herrera-Joancomartí, J. J3Gen: A PRNG for Low-Cost Passive RFID. Sensors 2013, 13, 3816–3830. [Google Scholar] [CrossRef] [PubMed]
- Massey, J. Shift-register synthesis and BCH decoding. IEEE Trans. Inf. Theory 1969, 15, 122–127. [Google Scholar] [CrossRef]
- Menezes, A.; van Oorschot, P.; Vanstone, S. Handbook of Applied Cryptography; CRC Press: Boca Raton, FL, USA, 1996. [Google Scholar]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Peinado, A.; Munilla, J.; Fúster-Sabater, A. Revision of J3Gen and Validity of the Attacks by Peinado et al. Sensors 2015, 15, 11988-11992. https://doi.org/10.3390/s150511988
Peinado A, Munilla J, Fúster-Sabater A. Revision of J3Gen and Validity of the Attacks by Peinado et al. Sensors. 2015; 15(5):11988-11992. https://doi.org/10.3390/s150511988
Chicago/Turabian StylePeinado, Alberto, Jorge Munilla, and Amparo Fúster-Sabater. 2015. "Revision of J3Gen and Validity of the Attacks by Peinado et al." Sensors 15, no. 5: 11988-11992. https://doi.org/10.3390/s150511988






