A Network Topology Control and Identity Authentication Protocol with Support for Movable Sensor Nodes
Abstract
:1. Introduction
2. Related Work
3. TCM Protocol
3.1. Network Model and Hypothesis
- The physical properties for all the nodes like the configurations of energy and hardware are the same.
- All the nodes are on the same plane and their original positions are random.
- All the nodes can move in the monitoring area with a random speed and direction.
- The sink nodes have more abundant resources than the ordinary sensor nodes, such as communication range and storage space.

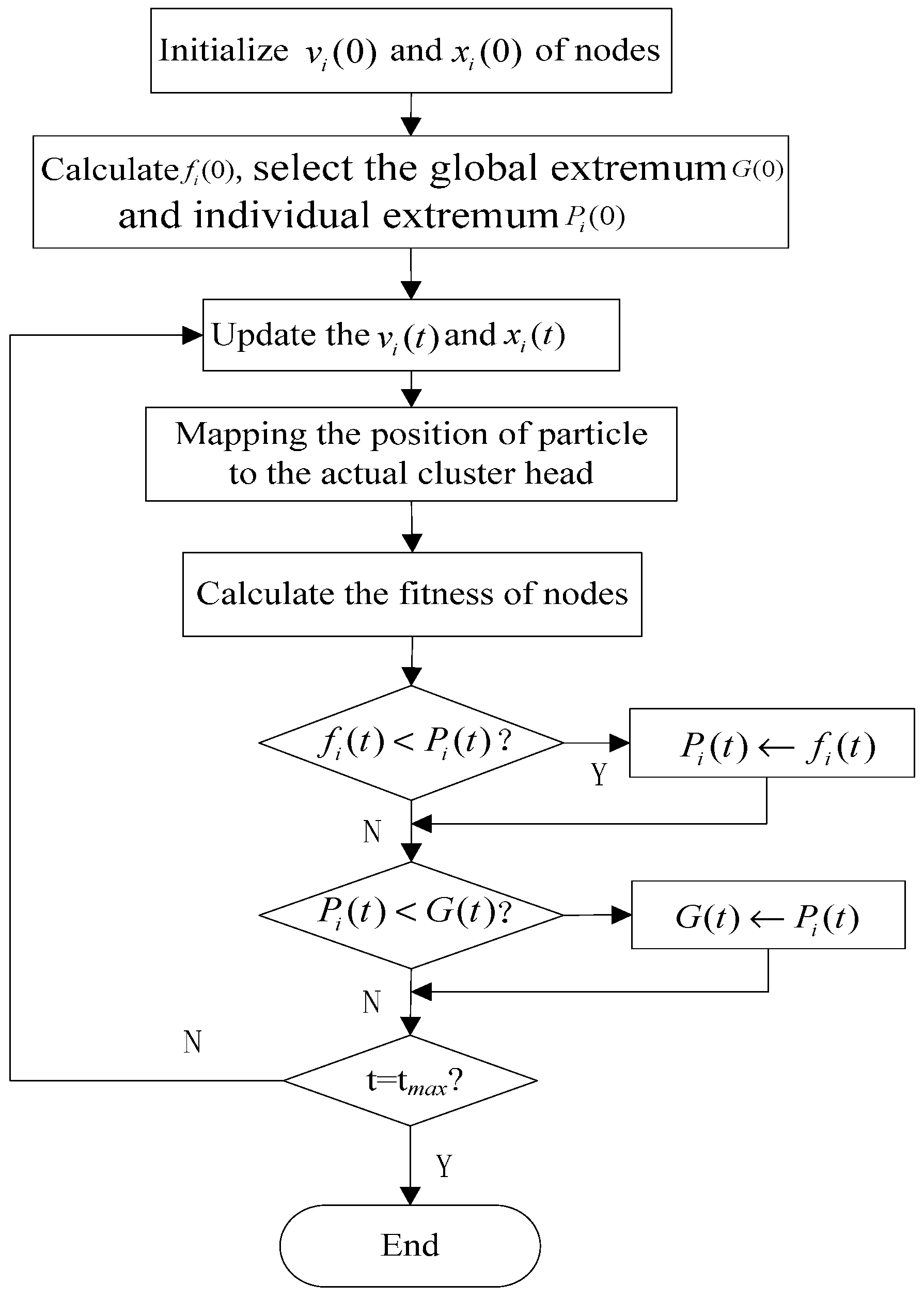
3.2. The Topology Establishment Phase
- (1)
- Initialize the position and velocity of particle Each has K candidate cluster heads.
- (2)
- Assign node ni to the closest cluster head, calculate the fitness values of each particle using Equations (1)–(4).
- (3)
- Select the global optimal extremum G(t) of the population and the individual optimal extremum Pi(t) of each particle.
- (4)
- Update the position and velocity of particles.
- (5)
- Mapping the position of particle to the actual cluster head.
- (6)
- Repeat steps (1) to (5) until the maximum iteration is reached or the required coverage rate is satisfied.
3.3. The Topology Maintenance Phase
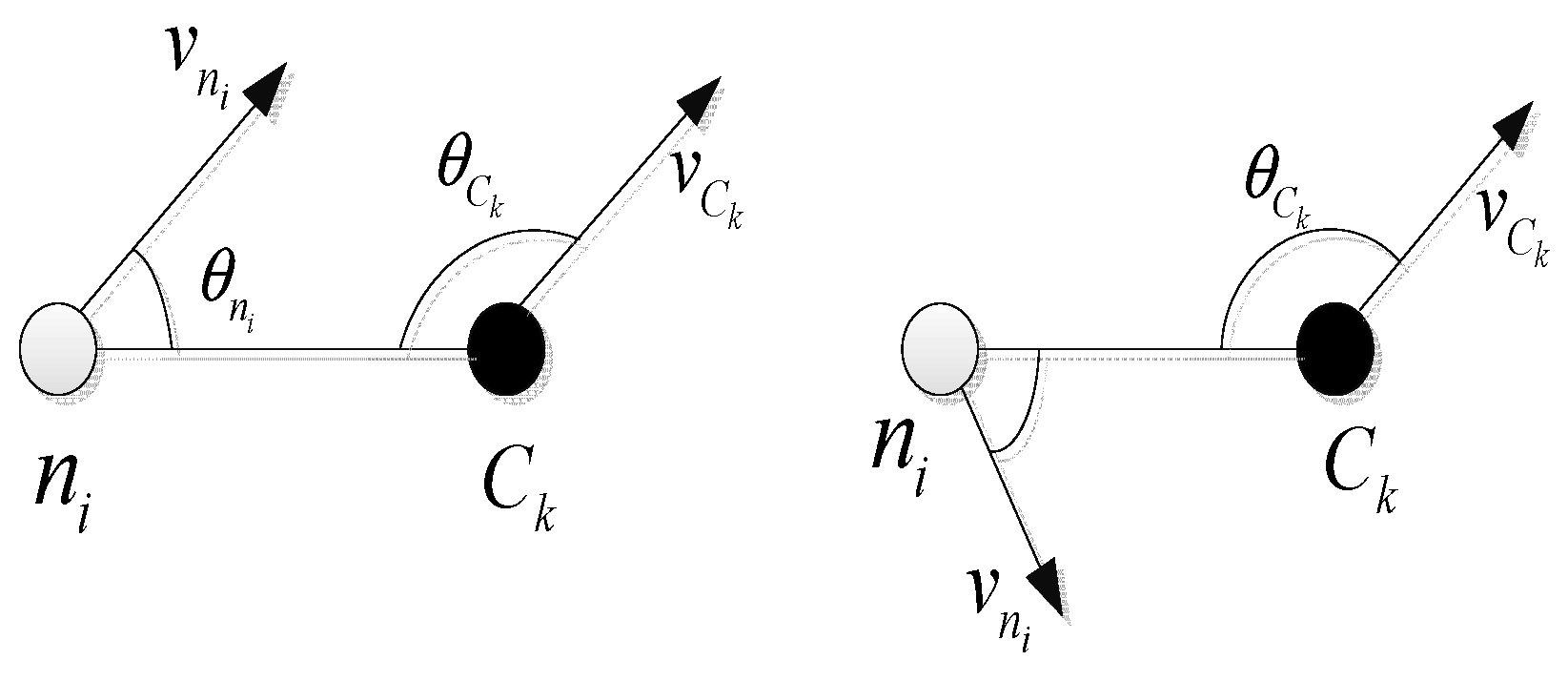
3.3.1. Movement of the Nodes within a Cluster
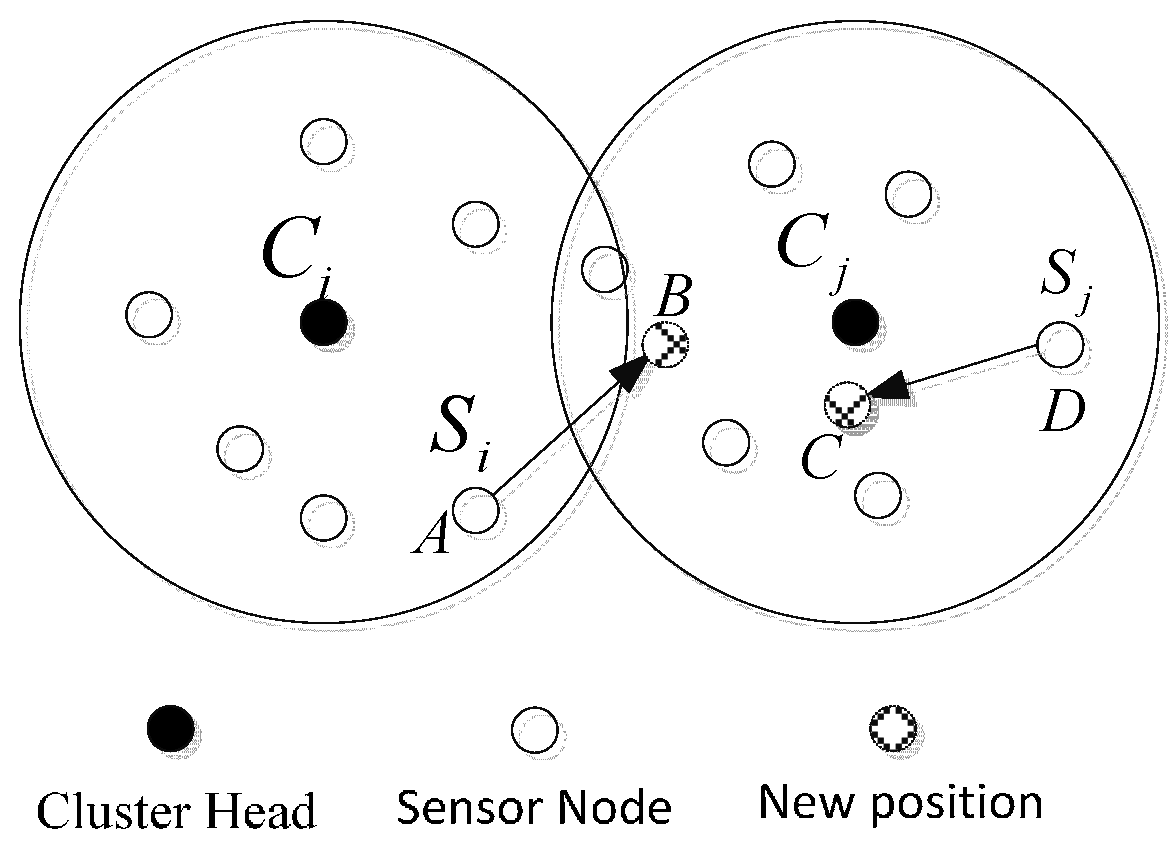
3.3.2. Nodes Moving between Clusters
3.3.3. New Nodes Join in or Node Death
4. Simulation and Evaluation
4.1. Network Stabilization
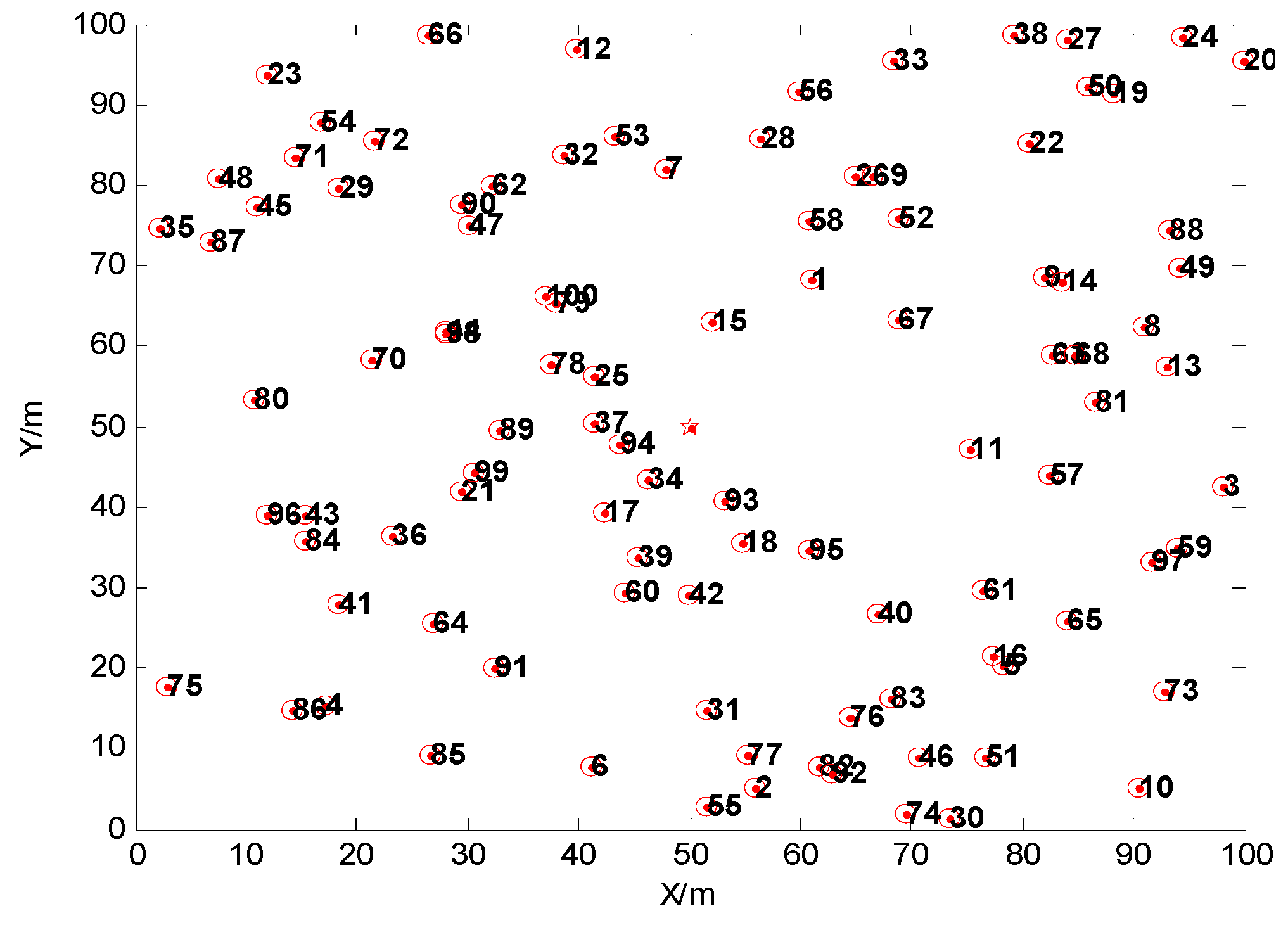
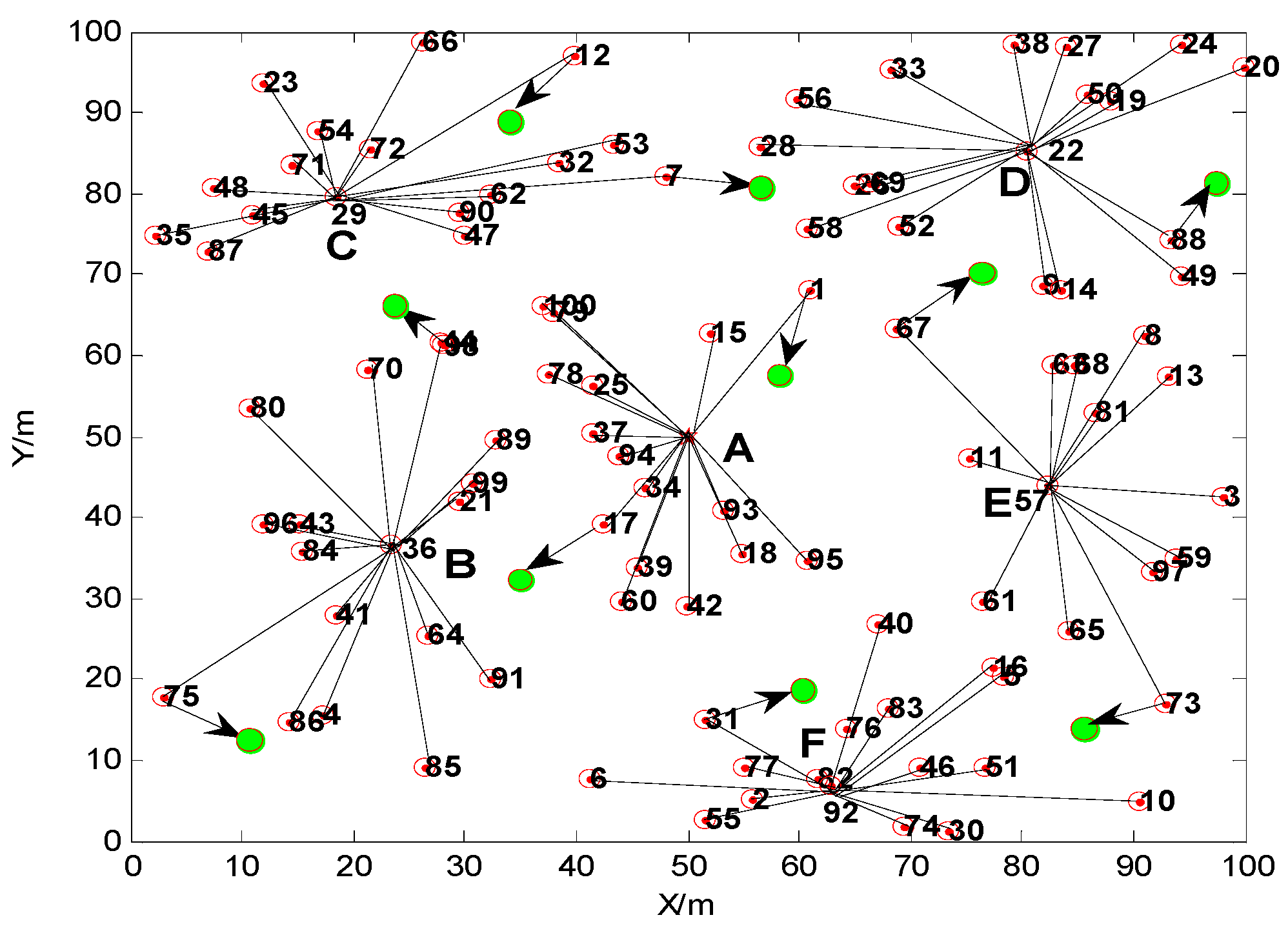
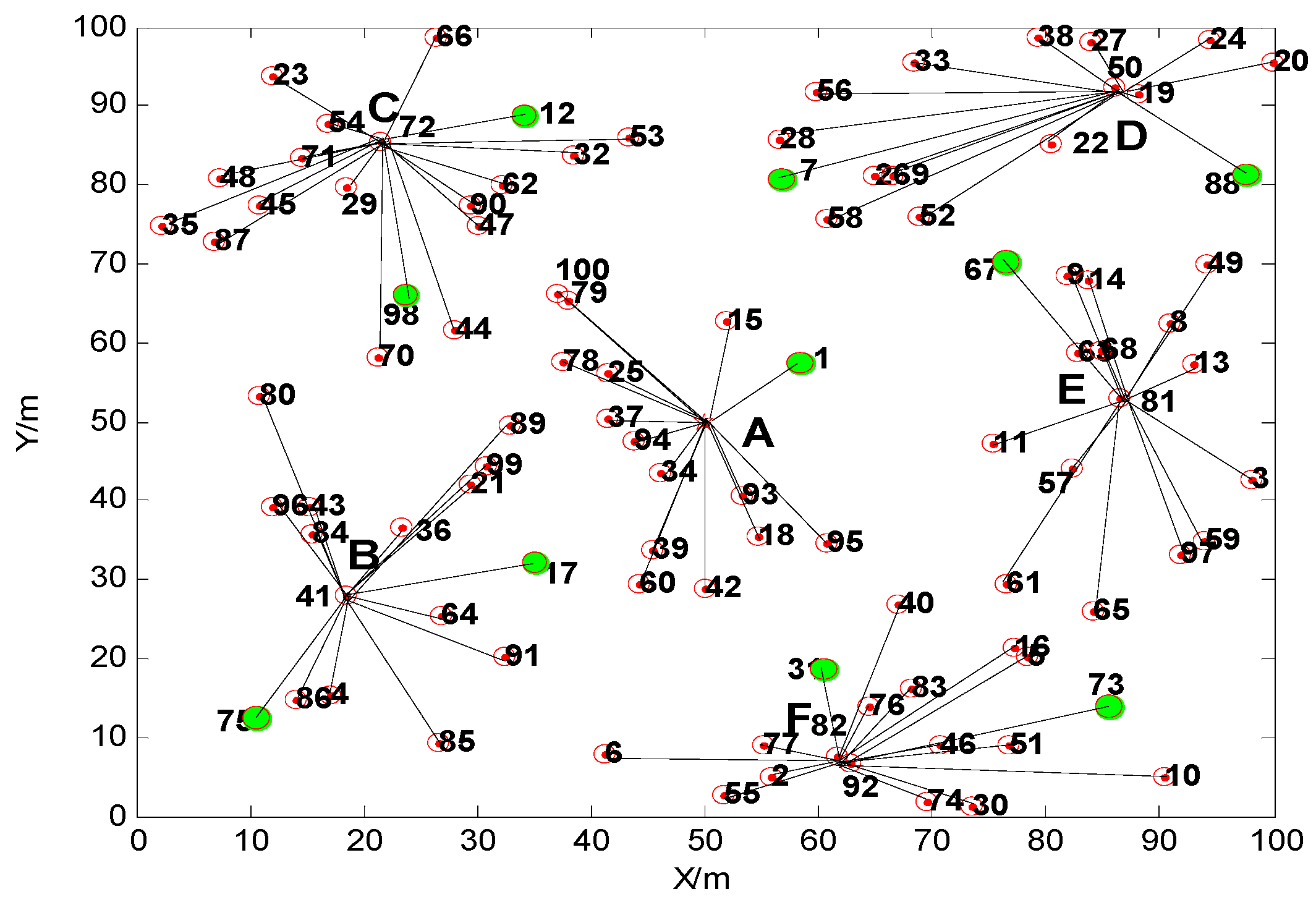
| A | B | C | D | E | F | ||
|---|---|---|---|---|---|---|---|
| Topology without movement | No. of cluster head | Base Station | 36 | 29 | 22 | 57 | 92 |
| Number of nodes | 16 | 17 | 16 | 17 | 13 | 16 | |
| Topology after movement | No. of cluster head | Base Station | 41 | 72 | 50 | 81 | 82 |
| Number of nodes | 15 | 15 | 18 | 15 | 15 | 17 | |
4.2. Amount of Data Transmitted
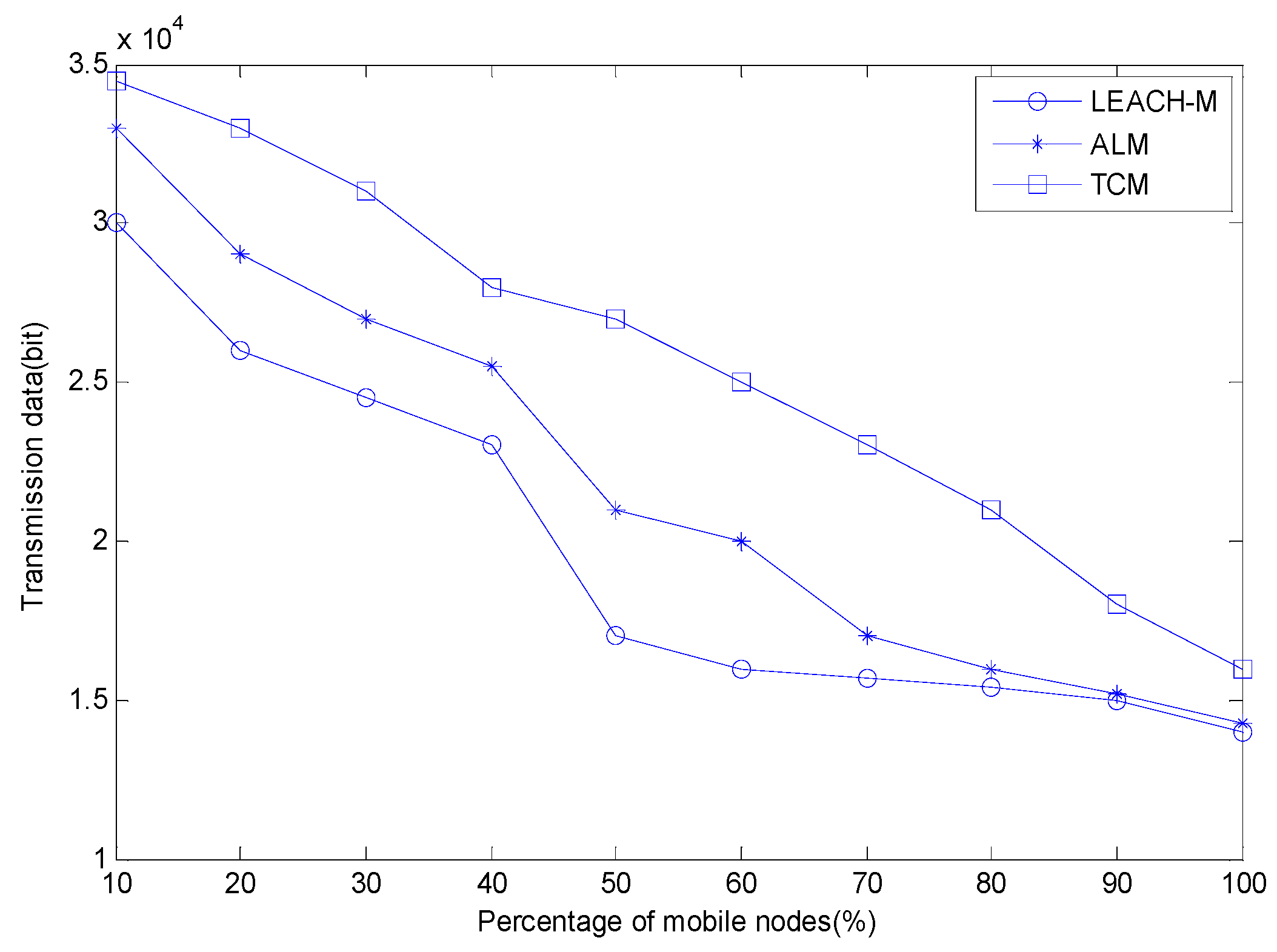
4.3. Network Energy Consumption and Security

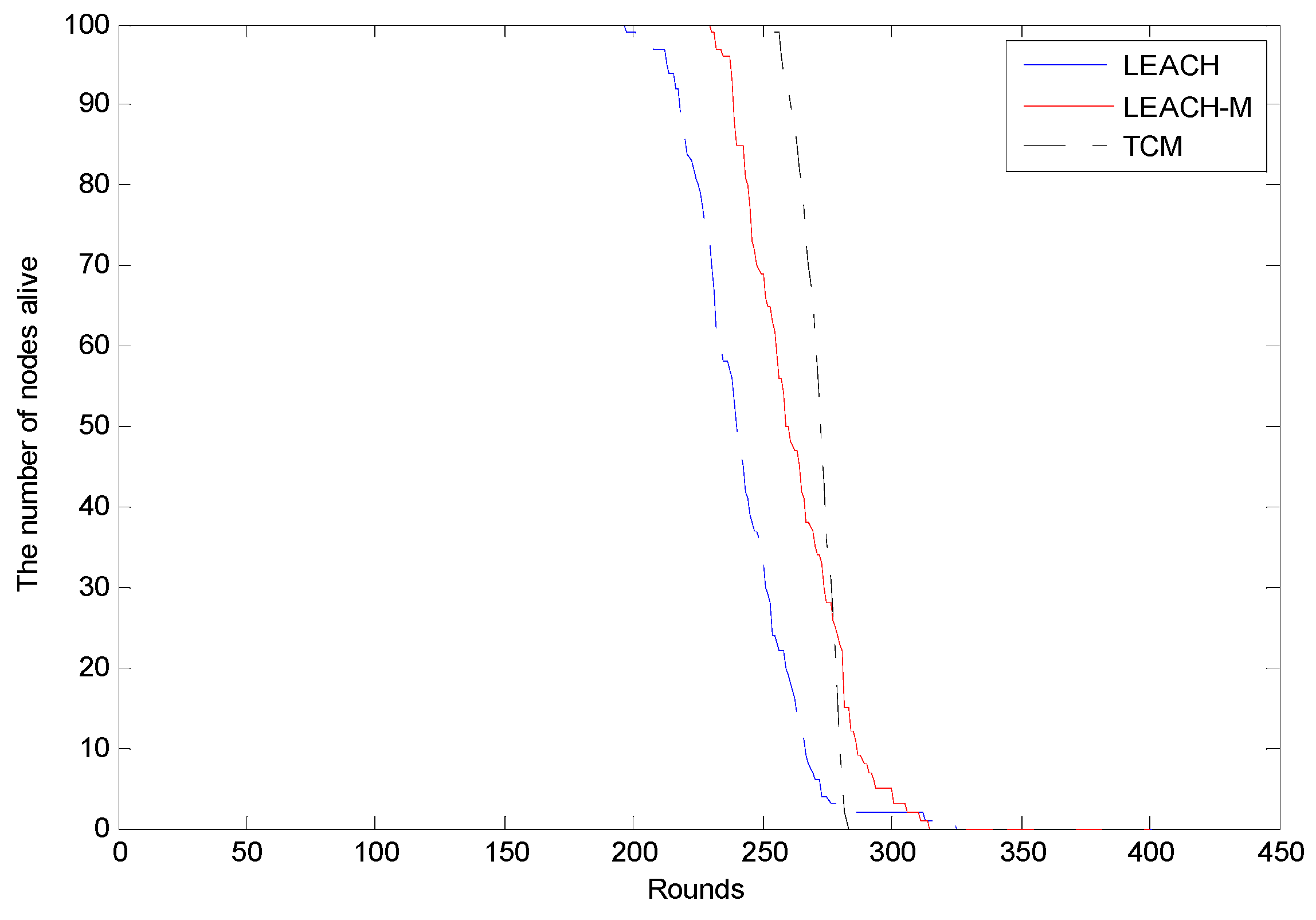
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Taneja, S.; Kush, A.; Makkar, A. Experimental Analysis of DSR, AODV using Speed and Pause time. Int. J. Innov. Manag. Technol. 2010, 1, 453–458. [Google Scholar]
- Umar, A.; Javaid, N.; Ahmad, A.; Khan, Z.A.; Qasim, U.; Alrajeh, N.; Hayat, A. DEADS: Depth and Energy Aware Dominating Set Based Algorithm for Cooperative Routing along with Sink Mobility in Underwater WSNs. Sensors 2015, 15, 14458–14486. [Google Scholar] [CrossRef] [PubMed]
- Anitha, R.U.; Kamalakkannan, P. Enhanced cluster based routing protocol for mobile nodes in wireless sensor network. In Proceedings of the 2013 International Conference on Pattern Recognition, Informatics and Mobile Engineering (PRIME), Salem, MA, USA, 21–22 February 2013; pp. 187–193.
- Bhattacharyya, D.; Kim, T.H.; Pal, S.A. Comparative Study of Wireless Sensor Networks and Their Routing Protocols. Sensors 2010, 10, 10506–10523. [Google Scholar] [CrossRef] [PubMed]
- Chu, X.; Sethu, H. A new power-aware distributed topology control algorithm for wireless Ad hoc networks. In Proceedings of the 2011 IEEE Global Telecommunications Conference (GLOBECOM), Houston, TX, USA, 5–9 December 2011; pp. 1–5.
- Lu, L.; Liu, Z. Energy and time efficient topology control algorithm for underwater acoustic ad hoc networks. In Proceedings of the 2nd International Conference on Computer Engineering and Technology (ICCET2010), Chengdu, China, 16–18 April 2010; pp. 483–486.
- Thanigaivelu, K.; Murugan, K. Grid-based Clustering with Predefined Path Mobility for Mobile Sink Data Collection to extend Network Lifetime in Wireless Sensor Networks. IETE Tech. Rev. 2012, 29, 133–147. [Google Scholar] [CrossRef]
- Heinzelman, W.R.; Chandrakasan, A.; Balakrishnan, H. Energy-efficient communication protocol for wireless microsensor networks. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Maui, HI, USA, 4–7 January 2000; pp. 1–10.
- Kim, D.S.; Chung, Y.J. Self-organization routing protocol supporting mobile nodes for wireless sensor network. In Proceedings of the IMSCCS’06, First International Multi-Symposiums on Computer and Computational Sciences, Hangzhou, China, 20–24 June 2006; pp. 622–626.
- Wang, C.; Luo, J.; Zhang, D.; Li, W. A mobility-based cluster routing protocol for mobile wireless sensor networks [J]. Comput. Eng. Sci. 2012, 34, 6–12. [Google Scholar]
- Yan, X.; Li, B.; Ye, X. A key management scheme for mobile heterogeneous sensor networks. J. Naval Univ. Eng. 2014, 29, 48–52. [Google Scholar]
- Zhu, S.; Setia, S.; Jajodia, S. LEAP+: Efficient security mechanisms for large-scale distributed sensor networks. ACM Trans. Sens. Netw. (TOSN) 2006, 2, 500–528. [Google Scholar] [CrossRef]
- Deng, J.; Hartung, C.; Han, R.; Mishra, S. A practical study of transitory master key establishment for wireless sensor networks. In Proceedings of the SecureComm 2005, First International Conference on Security and Privacy for Emerging Areas in Communications Networks, Athens, Greece, 5–9 September 2005; pp. 289–302.
- Zhang, X.; He, J.; Wei, Q. Key managing for node mobility scenarios in wireless sensor networks. J. Southeast Univ. 2011, 41, 227–232. [Google Scholar]
- Koblitz, N. Elliptic Curve Cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Miller, V. Use of Elliptic Curves in Cryptography. In Advances in Cryptology—CRYPTO’85; Springer: Berlin, Germany, 1986; pp. 417–426. [Google Scholar]
- Lee, Y.S.; Alasaarela, E.; Lee, H.J. Secure key management scheme based on ECC algorithm for patient’s medical information in healthcare system. In Proceedings of the 2014 International Conference on Information Networking (ICOIN), Phuket, Thailand, 10–12 February 2014; pp. 453–457.
- Modi, C.; Patel, D.; Borisaniya, B.; Patel, A.; Rajarajan, M. A survey on security issues and solutions at different layers of Cloud computing. J. Supercomput. 2013, 63, 561–592. [Google Scholar] [CrossRef]
- Latiff, N.M.A.; Tsimenidis, C.C.; Sharif, B.S. Energy-aware clustering for wireless sensor networks using particle swarm optimization. In Proceedings of the PIMRC 2007: International Symposium on Personal, Indoor and Mobile Radio Communications, Athens, Greece, 3–7 September 2007; pp. 1–5.
- Heinzelman, W.B.; Chandrakasan, A.P.; Balakrishnan, H. An application-specific protocol architecture for wireless microsensor networks. IEEE Trans. Wirel. Commun. 2002, 1, 660–670. [Google Scholar] [CrossRef]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, Y.; Chen, W.; Liang, J.; Zheng, B.; Jiang, S. A Network Topology Control and Identity Authentication Protocol with Support for Movable Sensor Nodes. Sensors 2015, 15, 29958-29969. https://doi.org/10.3390/s151229782
Zhang Y, Chen W, Liang J, Zheng B, Jiang S. A Network Topology Control and Identity Authentication Protocol with Support for Movable Sensor Nodes. Sensors. 2015; 15(12):29958-29969. https://doi.org/10.3390/s151229782
Chicago/Turabian StyleZhang, Ying, Wei Chen, Jixing Liang, Bingxin Zheng, and Shengming Jiang. 2015. "A Network Topology Control and Identity Authentication Protocol with Support for Movable Sensor Nodes" Sensors 15, no. 12: 29958-29969. https://doi.org/10.3390/s151229782