1. Introduction
Wireless sensor networks are an emerging networking technology, which is widely used in environmental monitoring, emergency and rescue communication, military applications,
etc. The unique feature of such networks is formed by the huge number of sensor nodes. Each node communicates over a wireless channel without any centralized control [
1]. One of the problems in wireless sensor network is efficient data transmission and lifetime. The low-energy adaptive clustering hierarchy (LEACH) protocol presented by Heinzelman
et al. [
2] was a widely known and effective one to reduce and balance the total energy consumption. Later, Tan
et al. [
3] proposed an energy-efficient hybrid cluster-based protocol (HCEP) to prolong the lifetime of the network. To reduce the consumption of energy, Wu
et al. [
4] developed a structure fidelity data collection (SFDC) framework to reduce the number of active sensor nodes, which can not only save energy, but also reserve the data fidelity. Another problem is the throughput capacity, meaning how much traffic the wireless networks can carry. In their groundbreaking work, Gupta and Kumar [
5] had shown that, for a static wireless networks consisting of
n nodes randomly and uniformly distributed, each node can achieve a rate of order
. Given two functions
and
:
means
;
means
; if
,
w.h.p.; if both
and
,
;
means
when logarithmic terms are ignored. They also derived an upper bound on the capacity that scaled on the order
. This capacity gap was closed by Franceschetti
et al. [
6]. Inspired by percolation theory, they constructed a series of paths spanning the network both horizontally and vertically. Then, by exploiting the time division multiple access (TDMA) strategy, each node transmitted its information to the nearest horizontal highway. After that, the information was transported in a multi-hop manner toward the vertical paths, which was near the receiver. Finally, the information was sent to the receiver from the existing node on the vertical highway. Based on the “highways scheme”, a rate of
was achieved for each node. Since then, capacity scaling has drawn considerable attention. Hu
et al. [
7] investigated the impact of geometry on the capacity of a wireless network. They constructed highways in a strip network, triangle network and three-dimensional network. Since the infrastructure was an effective way to ease hop-by-hop transmission, Liu
et al. [
8] allocated some infrastructure into the network and proved that the capacity could increase linearly with the number of infrastructures. Tan
et al. [
9] proposed a framework to maximize the total utility of bandwidth allocation for the three traffic types in infrastructure-based wireless networks. Multicast was often used in realistic networks; Li [
10] derived the multicast capacity of large-scale wireless networks using a tree-based routing scheme. Later on, Alfano
et al. [
11,
12] firstly investigated the capacity of topology inhomogeneous wireless networks. Liu
et al. [
13] constructed a “highway system” in inhomogeneous Poisson networks. Based on the highway system, the lower bound of capacity was obtained, and they found that the bottleneckof the rate was caused by the place of the lowest node density. After that, the scenario of traffic heterogeneity was studied. Kim
et al. [
14] proposed a differentiated channel access scheme to resolve the throughput fairness problem in heterogeneous wireless networks. Recently, Lu and Shen [
15] gave a comprehensive overview of the development of capacity and delay in
ad hoc networks. They also presented the fundamental tradeoffs between capacity and delay under a variety of mobility models.
However, due to the wireless channel being broadcast, it is easily attacked by eavesdroppers and malicious nodes. This motivates considering the secrecy constraint in capacity analysis. With some exceptions, the secrecy capacity under the protection of an RSApublic key cryptosystem was used in [
16,
17]. They got a pessimistic result that, for a network consisting of
n legitimate nodes, a rate of
was obtained, where
was the probability that a node shared a primary secure association (SA) with any other node. To avoid the capacity degradation caused by
decreasing, an information theoretic security was proposed, which was achieved by using the channel difference between legitimate nodes and eavesdroppers, which required the intended receiver to have a stronger channel than eavesdroppers. To degrade the signal of eavesdropper, Vasudevan
et al. [
18] used other nodes around the transmitters to generate artificial noise. They found that, when a per-node throughput of
was desired, the network can tolerate up to
independent eavesdroppers or a single eavesdropper with
antennas, where
c and
ϵ were constants. After that, Capar
et al. [
19] investigated the impact of network dimension on the secrecy capacity. They found that the per-node secure throughput was
in one-dimensional and
in two-dimensional networks, respectively. More recently, Zhang
et al. [
20] considered a homogeneous network with an independent eavesdropper and colluding eavesdroppers. Each node was installed with three antennas, where two of them were used for transmitting and receiving, and the other one was employed to generate artificial noise to degrade the signal of the eavesdropper. By constructing a set of highways in the networks, they derived that the secrecy capacity was
for the scenario of an independent and colluding eavesdropper. Later on, Cao
et al. [
21] investigated the tradeoff between secrecy capacity and delay in large-scale mobile
ad hoc networks. They found that, for a given delay constraint
D, the optimal secrecy throughput capacity was
. In addition to the method of generating artificial noise to suppress the eavesdroppers’ receiving signal, an alternative idea of the secrecy zone was proposed in [
22,
23], which required neither the channel state information of eavesdroppers, nor extra power to generate artificial noise. Under the protection of the secrecy zone, Koyluoglu
et al. [
22] obtained that, as long as the density of the eavesdropper was
, each node can achieve a secure rate of
. Besides the information security issue in wireless networks, privacy security is also concerned. To avoid disclosing the users’ interest to others, Luan and Lu
et al. [
24] employed a privacy-preserving mechanism to protect sensitive user information during social communications. Although there existed many works on security issues, all of them focused on homogeneous networks. Therefore, a fundamental question arises: what is the impact of the capacity if both the security constraint and heterogeneity topology are taken into consideration?
In this paper, we focus on static cluster sparse networks. Our main purpose is solving the secrecy transmission in heterogeneity networks. The transmission is divided into intra-cluster and inter-cluster traffic. For the former transmission, we propose a heterogeneous percolation model. Based on the heterogeneous percolation, we construct a series of “paths” in the radial direction and around the cluster. The information is transported in a multi-hop manner on the paths. While for the latter traffic, some information pipelines have been built among clusters. On the basis of the “highway system” and information pipelines, we employ the secrecy zone to protect the transmission. This is different from the artificial noise generation fashion, where their strategy needs additional power to generate noise.
The main contributions can be concluded as follows:
We prove the existence of highways in heterogeneous networks. More importantly, it is shown that the networks still percolate in the secrecy constraint model, and many secrecy highway paths can be constructed.
We first exploit the secrecy zone to protect the transmission in heterogeneous networks. The relationship between the secrecy capacity and the tolerable density of the eavesdropper was established.
Due to the impact of heterogeneity, we observe that the secrecy throughput of intra-cluster transmission is higher than that in a homogeneous one, and the bottleneck of secrecy throughput is located at the area with the minimum node density.
The rest of this paper is organized as follows. In
Section 2, we give the network model. We give the transmission model in
Section 3. The construction of the circular percolation model is described in
Section 4.
Section 5 derives the secrecy throughput in intra-cluster transmission. In
Section 6, we investigate the secrecy throughput of inter-cluster transmission. We present the conclusion of this paper in
Section 7.
2. Network Model
We consider an extended network
with
n legitimate nodes randomly distributed, where the distribution of legitimate nodes follows the shot noise Cox process (SNCP) [
25]. The main process of SNCP is described as follows:
M clusters scattered in
A randomly. The expected value of
M is
. We denote the center of the clusters as
. For each
, using the center point
as a mother point, a point process centered by
with an intensity of
at place
ξ is generated.
is a function of density;
is the number of nodes of cluster
. Let each cluster consist of an equal number of legitimate nodes,
i.e.,
. In addition, according to the distribution, the function of density
F at place
ξ can be expressed as:
where
is related to the distance between
ξ and
, and the sum
on the whole network is finite. For simplicity, we use function
to substitute the density function
, where
. To gain finite summation over the whole area, the function
is stated as follows:
In addition, let m scale as ; let δ be a degradation factor; and . Then, each cluster has a number of nodes , i.e., for , since is finite.
According to the node’s distribution, we can obtain the average distance between each cluster center
as:
From Equation (
3), we know, when
,
as
, and the clusters are distributed sparsely. In this work, we only consider the cluster-sparse network, where the
is heterogeneous. Let
denote the largest density and
vice versa.
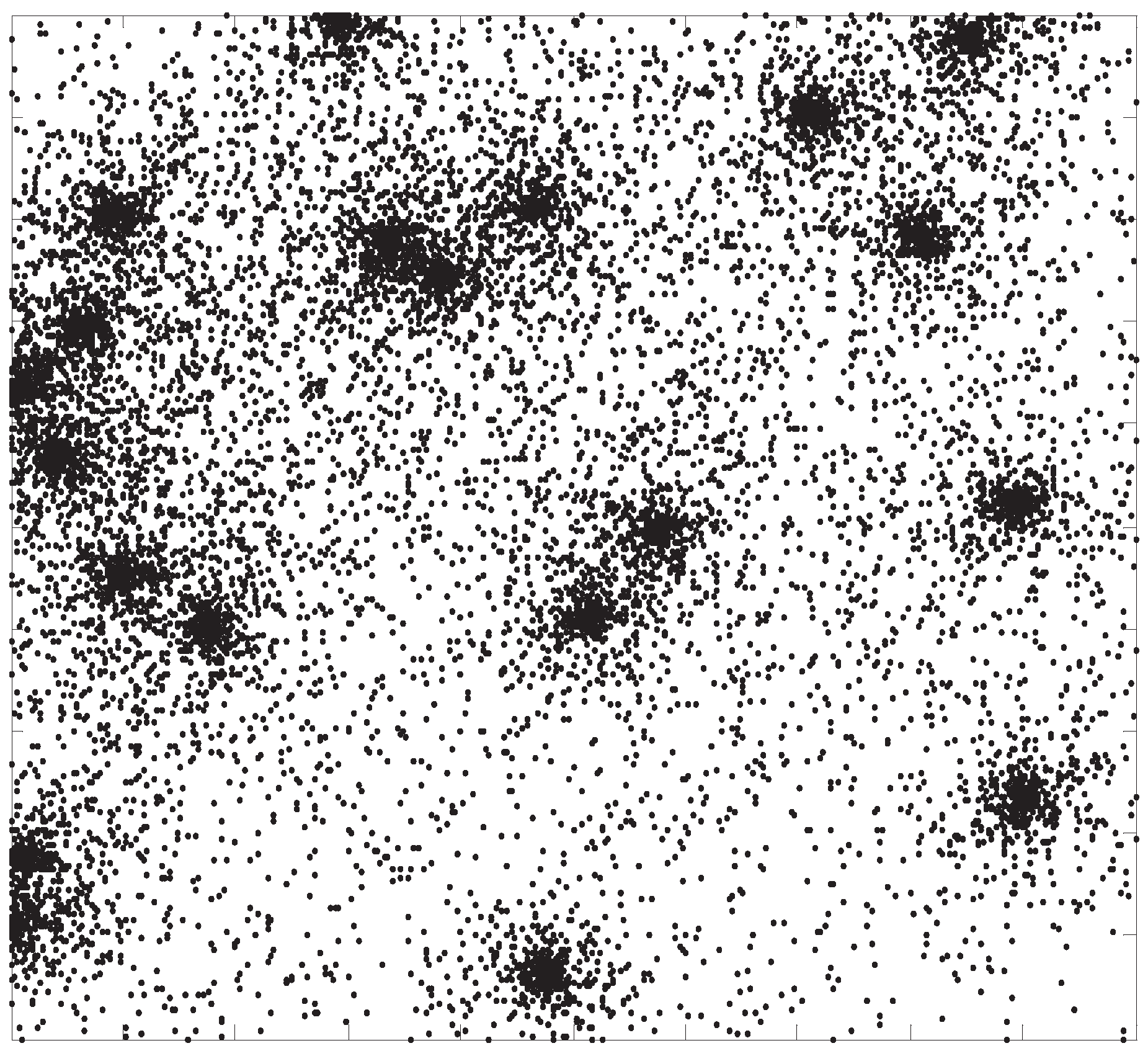
Figure 1 is an example of this kind of network topology.
Figure 1.
Example of a heterogeneous topology network. The parameter of the network is 10,000, and .
Figure 1.
Example of a heterogeneous topology network. The parameter of the network is 10,000, and .
Different from the legitimate nodes, the eavesdroppers are uniformly and independently distributed in the network with density . Let ε denote the set of eavesdroppers. Since eavesdroppers can be easily detected if they are active, the eavesdroppers are assumed to keep silent. To get insight into the secrecy throughput, the eavesdroppers is also assumed to have a super ability for computing. This means that the traditional method cannot be used here. In addition, let the transmitters know the location of the eavesdropper. Although the assumption seems idealistic, it allows one to gain valuable insight into the problem.
To get the worst case of secrecy throughput, the interference caused by simultaneous transmission is assumed as noise, whereas the eavesdroppers do not have this assumption.
4. Circular Percolation
We first construct a percolation model for the heterogeneous topology. Since the legitimate nodes are distributed heterogeneously, the traffic is divided into two parts: intra-cluster traffic and inter-cluster traffic. For each part of the traffic, we resort to the tools of percolation theory to construct the routing scheme. For the intra-cluster traffic, we establish a circle percolation model, which is different from the previous percolation model; while for the inter-cluster case, we construct a series of information pipelines to link the clusters.
In our model, by virtue of percolation theory, we present a circular percolation model and construct a set of connected highways for legitimate nodes. Different from the the work in [
6], the circular highways are from internal to external or encircling the cluster.
Lemma 1. Assume is a minimum positive constant that separates the and other nodes. Then, each cluster can build a crossing path within for .
Proof. Each cluster is tessellated into
circular squares, where
x is the number of sectors and
is the number of annuli. Note that the arc of each sector is equal,
i.e.,
. Due to the heterogeneous node distribution, the distance between every two annuli is not the same, as shown in
Figure 2.
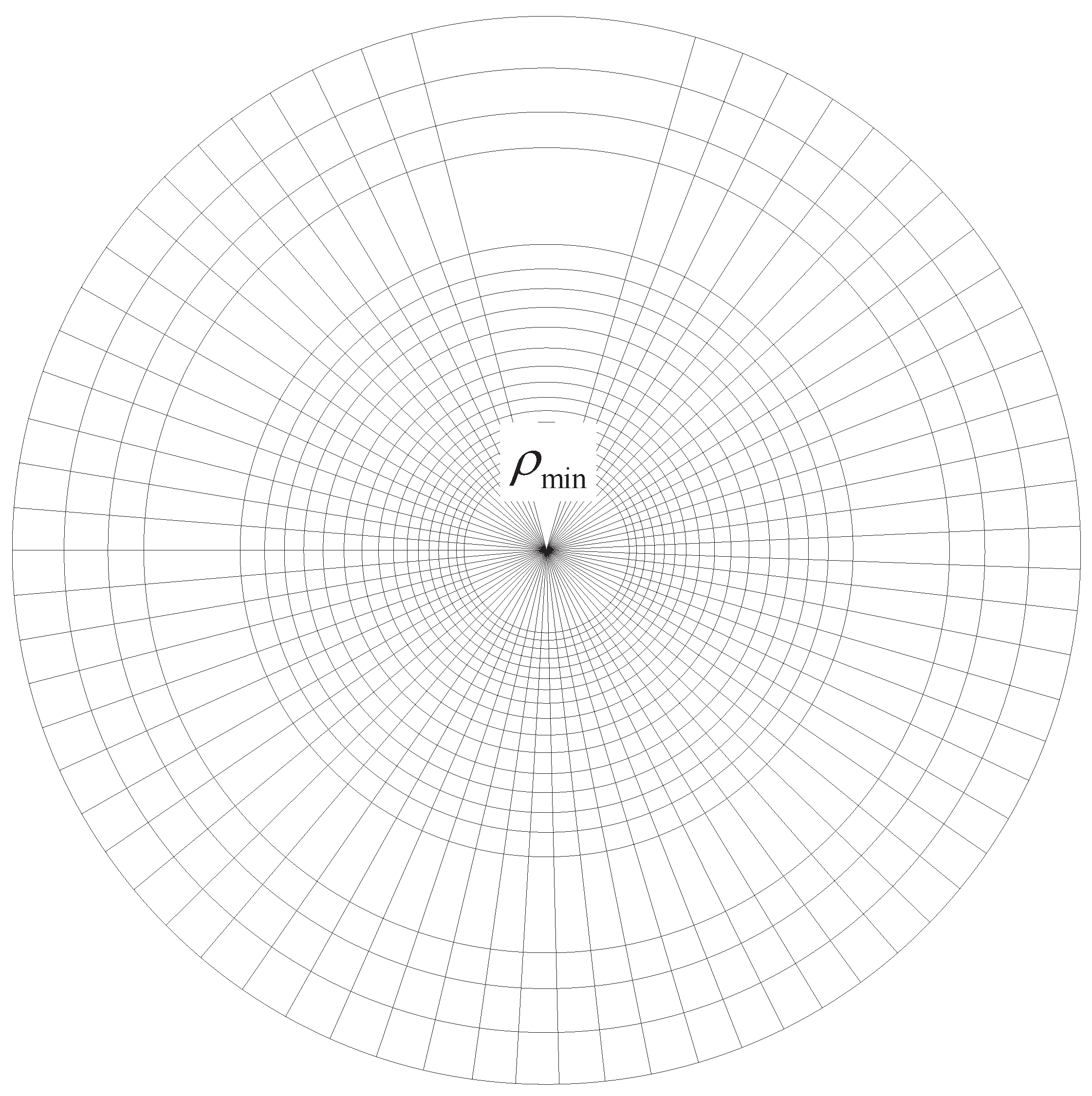
Figure 2.
A circular square in a cluster. is the minimum radius within which there is no node located.
Figure 2.
A circular square in a cluster. is the minimum radius within which there is no node located.
Due to the impact of heterogeneity, the node density at different annulus areas varies. In order to guarantee that each square contains at least one node, the external annuli need to be wider than the inner ones. Correspondingly, we set the radius of the
i-th annulus to be:
Thus, according to the circular square tessellation above, we can conclude that each cell can be treated as a square when . ☐
Lemma 2. According to the heterogeneous tessellation, we can get that the number of the parameter x is: .
Proof. From Lemma 1, we know that the radius of one cluster is:
Combining Equation (
3) and Equation (
8), we have:
Finally, we obtain . ☐
Lemma 3. For a square on the i-th annulus, let be the number of nodes distributed in ; then, we can get for .
Proof. According to percolation theory, a square
is open if there exists at least one node located in
, or closed otherwise. From the
Appendix A in [
12], the open probability of a square is:
From Equation (
10), we can observe that
decreases as increasing values of
i for
. ☐
Since the probability decreases with i, we can calculate the critical value , within which the probability can satisfy the condition of , where is the critical probability in percolation theory.
Lemma 4. There exists a critical value , within which each cluster can construct a set of connected highways if the degradation factor .
Proof. From percolation theory, there is a critical probability
, when
, that there exists many disjoint paths traversing the network, which is going to be one. Thus, we can get the following equation by Lemma 3:
where
is the probability representing that the square
is open, and
.
Following Equation (
11), we can obtain that:
where
. Substituting
into (
12), we can achieve that
. ☐
Combining Lemma 4 and Equation (
7), the critical value
is achieved. In particular, we can construct
annuli within the radius
.
The percolation model for the intra-cluster traffic has been constructed. Each cluster is partitioned into
lattices. Specifically, a path is called open if two adjacent squares are open. Based on Appendix I in [
6], we can get that there are
disjoint paths through an area of
. Hence, within area of less than
, we can build
disjoint paths from the internal to external cluster and
disjoint paths around each cluster. By the connection of these two paths, the highway system for the legitimate nodes is constructed. Although our model is a heterogeneous lattice, it can be treated similarly as a
rectangle lattice.
5. The Secrecy Rate of Intra-Cluster Traffic
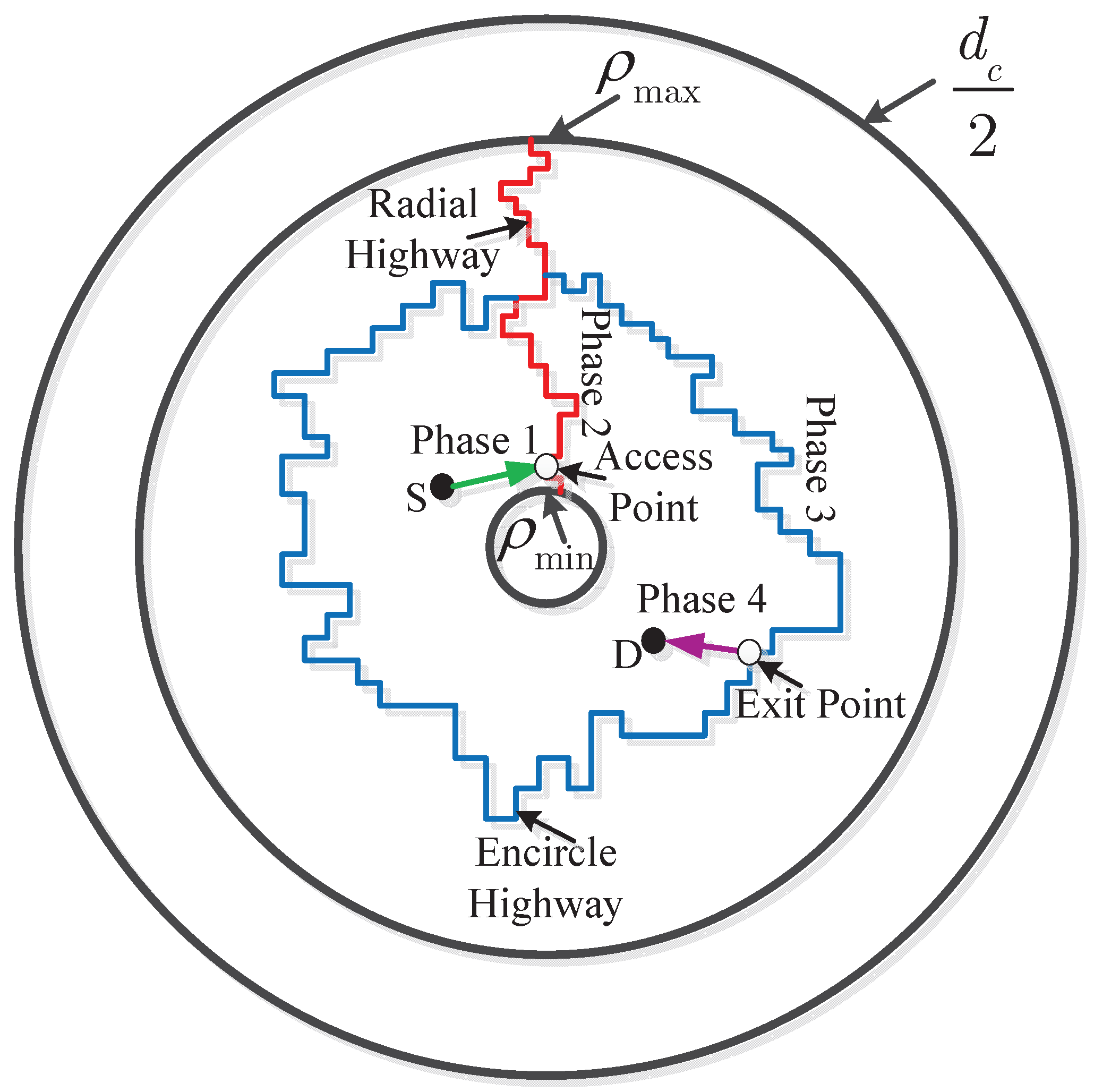
In this section, as illustrated in
Figure 3, we introduce a scheme that ensures the security over the whole path, from the source to a destination. The routing scheme of intra-cluster transmission can be partitioned into four separate phases.
Phase 1 (draining phase): Source node S drains packets to an access node on the radial highway directly. Note that the highway may not be fully contained in its corresponding sector, whereas it may deviate from it. However, according to percolation theory, a highway is never farther than from its corresponding sector.
Phase 2 (radial highway phase): Packets are carried across the cluster along the radial highway using multiple hops and multiple time slots.
Phase 3 (encircling highway phase): Similar to Phase 2, packets are transported clockwise on the annulus highway.
Phase 4 (delivering phase): Finally, packets are delivered to the receiver from the exit point on the encircling highway.
Figure 3.
A schematic representation of the routing scheme. We omit the eavesdroppers in this figure.
Figure 3.
A schematic representation of the routing scheme. We omit the eavesdroppers in this figure.
Different nodes are allocated with different power, so that we can transform the heterogeneous circular lattice into a homogenous regular square lattice. In addition, the time division multiple access (TDMA) schedule is employed, and the information is transported hop by hop, then a constant rate on the highway is obtained. However, there are still some differences between our model and the previous one; for example, not all of the highways serve identical nodes, and the power of each node is not equal.
Lemma 5. For a given square, to cancel the interference caused by simultaneous transmission, the power of legitimate nodes in square is:where is the unit power for a legitimate transmitter. Proof. For a square
, let
be the interference from the outside square and
for that from the inside square. If the distance between two nodes is
d, which is not the Euclidean distance, but the number of
d squares away, then we can get the interference from different directions as follows:
As , when , we can get . ☐
Next, we exploit the idea of the secrecy zone to guarantee the secrecy of the communication over a single hop.
By Lemma 5, for a given square, the interference caused at
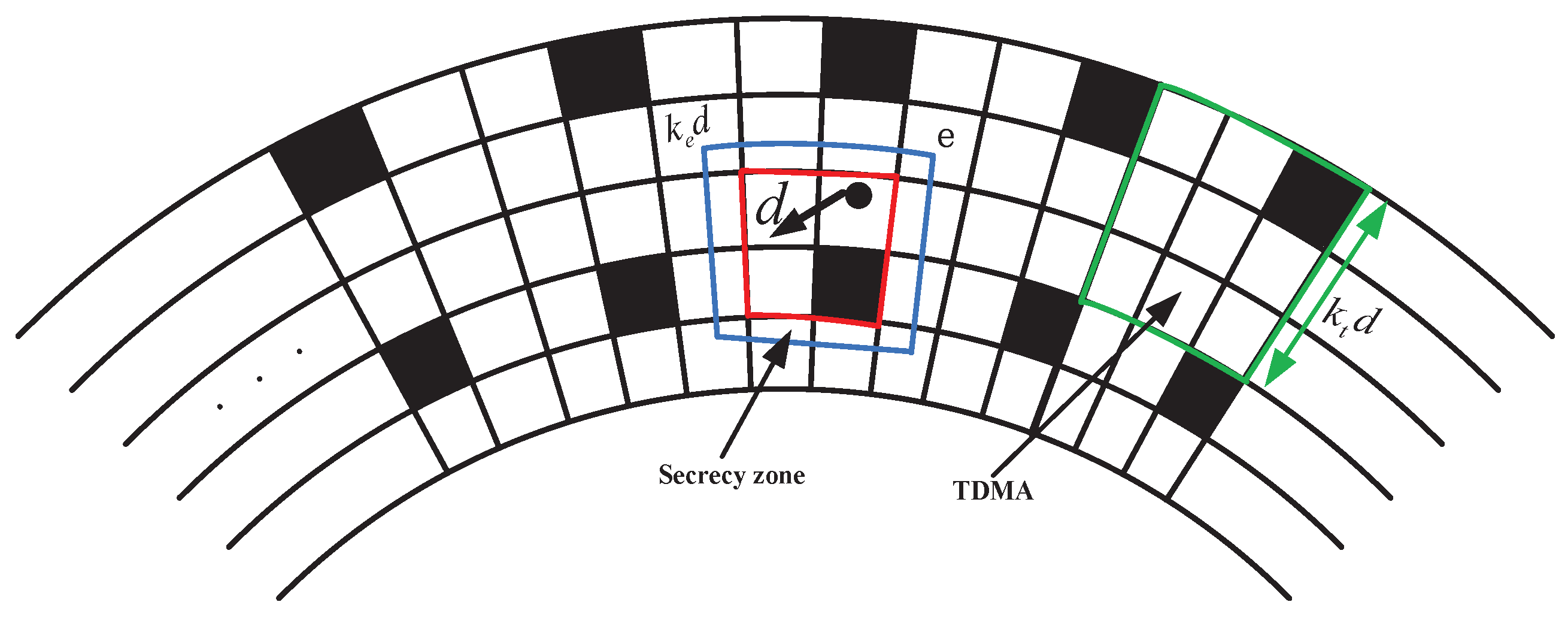
d squares is equal. Thus, we can make the cluster network as a square network. As shown in
Figure 4, we group several squares into a group with edge
squares. Each group contains
squares. Using the TDMA to schedule the transmission, that is each square takes a turn on the transmission over
slots, in each slot, a transmitter can send packets to a receiver located at most
d squares away. In
Figure 4, the larger square around a transmitting square is the secrecy zone, which consists of squares that are at most
squares away. We firstly establish an achievable secure rate on a single hop.
Figure 4.
An illustration of the TDMA strategy with size . The blue square surrounding the transmitter is the secrecy zone, which is at most squares away from the transmitter.
Figure 4.
An illustration of the TDMA strategy with size . The blue square surrounding the transmitter is the secrecy zone, which is at most squares away from the transmitter.
Theorem 6. In each square, the secrecy rate that a legitimate source-destination pair can obtain is , if:where is a constant and d is the transmission range. Proof. Assuming that transmitter
i in square
transmits toward destination
j located in square
at a distance of
d squares away, we obtain the
of the legitimate receiver as follows:
where
is the distance between source node
i and destination node
j, and
is the distance between interferer
and the receiver.
For the case of eavesdropper
, the upper bound
at the eavesdropper is:
where
is the distance between the transmitter and eavesdropper
e, where the upper bound of
is obtained by getting rid of the interference at the eavesdropper. Note that the distance between the
i and
j is at most
,
i.e.,
and:
Let
denote the upper bound of the interference caused by simultaneous transmitter nodes. Then,
notice that this sum will converge to a constant
, if
, and the proof is shown in
Appendix A.
Substitute Equation (
20)–Equation (
22) in Equation (
18) and Equation (
19); we obtain that:
and:
Hence,
for every eavesdropper
e, if we choose
such that:
According to the Gaussian wiretap channel capacity [
27], the secrecy rate
in each square is:
where
is the time utilization factor. ☐
Now, similar to Lemma 2 in [
22], we adopt the multi-hop randomization strategy, which guarantees the security over the entire path, from source to destination, at each eavesdropper listening to all transmissions. In [
22], the authors assumed that each legitimate node used identical power for transmission, while we assign different powers for different nodes, as shown in Lemma 5. Despite the difference in the power, the proof goes along the same line as [
22]. For conciseness, we omit details.
Lemma 7. (Lemma 2 in [22]) If we can secure each hop from an eavesdropper, then we can ensure secure for all hops from any eavesdropper located on the edge of the secrecy zone. In
Section 4, we have described the circular percolation model and constructed highways without the constraint of security. If taking the secrecy constraint into consideration, a square is open if the square contains at least one legitimate node and there is no eavesdropper within the secrecy zone of the square. The following result gives the existence of a sufficient number of secure highways in intra-cluster transmission.
Lemma 8. We can construct a number of radial secrecy highways and encircling highways within the radius , if .
Proof. For a given square, let
be the probability of
contained in a secrecy zone without eavesdroppers. According to a Poisson random distribution, the average number of eavesdroppers located in a secrecy zone is
, and
can be denoted as:
Since , , we have that trends to one if .
Note that the status of edges in squares is not statistically independent due to the intersection of the associated secrecy zone. If both secrecy zones did not cross, the states of two squares would be independent. This occurs when the squares are at a distance of at least
squares away. Thus, we can conclude that the dependent model is related to a finite dependence model, as
and
d are constants. According to Theorem 7.65 in [
28], this dependent model stochastically dominates an independent model. Let
be the probability that squares are independently open. If
can be made arbitrarily high,
will be close to one. Therefore, under the assumption of the finite dependence model and some desirable properties, we can prove that the network will still percolate with the same properties, since both
and
can be set sufficiently large.
Under the independent square model, by Theorem 5 in [
6], with a square openness probability of
, we can obtain that there are
radial secrecy highways and
annuli highways. ☐
Till now, we have established the existence of a sufficient number of secure highways using the circular percolation model. Since there are four phases for packet transmission, we will derive the secrecy rate in each phase to find the rate bottleneck.
Lemma 9. If a cluster is divided into w sectors with an arc of , then for each sector , there are no more than legitimate nodes located.
Proof. Let
represent the number of legitimate nodes located in
and
be the probability that there exists a sector containing more than
nodes. For each sector, the number of nodes follows a Poisson distribution of
. According to the Chernoff bound, when
, then:
Therefore, we can get that there is no sector existing with more than nodes. ☐
Lemma 10. In Phase 1, if the density of the eavesdropper is , each legitimate node can achieve a secrecy access rate with a node on the radial highway.
Proof. According to Theorem 5 in [
6], if we choose
ϵ and
κ appropriately, there exist at least
radial highways within a sector of arc
. From percolation theory, we know that each highway may not be fully contained in its corresponding sector, and it may deviate from it. However, it never deviate by an arc of
from its corresponding sector,
i.e., it will not be father than
squares.
By Theorem 6, let
; we can get that the secrecy rate between a legitimate node and an access node is:
Since there is an amount of nodes in a square, they need to share the bandwidth. From Lemma 9, we have that, if the associated secrecy zone contains no eavesdropper, the secrecy rate for Phase 1 is . Next, we elaborate that this will happen if as n goes to infinity.
For the
i-th annulus, the area of the guard zone is
, which is the area to eliminate the eavesdroppers. Let
be the number of eavesdroppers in a cluster (Poisson with parameter
) and
as the total amount of legitimate nodes in a cluster. In addition, we denote the total area that the eavesdroppers make it impossible for a legitimate user to arrive at a highway as
. Clearly,
, where
. For each
, let the amount of legitimate nodes in this region be
. According to the heterogeneity of node distribution, we have
. Thus, for each cluster, by the Chebyshev inequality, we have:
for any
with high probability as
. Let
ϝ be the fraction of legitimate nodes that cannot transmit to highways due to the eavesdropper, and we can obtain the upper bound of
ϝ as:
with the probability going to one as
. The first inequality is deduced from the intersecting secrecy zones caused by eavesdroppers, and the second inequality derives from Equation (
30), while the limit holds as
and
. Under this condition, we can conclude that almost all of the legitimate nodes are securely connected to the highways as
. ☐
Phase 4 is the opposite process of Phase 1. Therefore, a similar conclusion can be made for this phase.
Lemma 11. In Phase 4, if the density of eavesdropper , then a legitimate node can receive information securely from the highway at a rate of .
In the highway phase, the information is transmitted hop by hop. Let in Theorem 6; we obtain the secrecy rate in Phase 2.
Lemma 12. In Phase 2, if the density of eavesdropper , then a legitimate node on the radial highway can achieve a secrecy rate .
Proof. According to the highway system, the transmission is occurring from one square to a neighboring square, where within the secrecy zone, there are no eavesdroppers. Thus, using Theorem 6 and letting , the secrecy rate in Phase 2 is . Since , there are radial paths extended from internal to external. By Lemma 9, we have that there are at most users w.h.p. in the sector of . That is, each node can enjoy a rate of order in the radial highway. ☐
In this way, the following lemma gives the secrecy rate of Phase 3.
Lemma 13. The legitimate nodes on the annulus highway can enjoy a per-node secrecy rate , where is a “heterogeneous factor”, which is only decided by δ.
Proof. Compared to the radial highways, it is more complicated for data delivered around the cluster, since the number of nodes served by the annulus paths is not identical. Assume each annulus highway is identical, similar to Lemma 12; the secrecy rate of order
. Nevertheless, due to the impact of heterogeneity, we denote the achievable secrecy rate as
, where
is a function of heterogeneous factor
δ, which will be discussed in detail in
Appendix B. ☐
Comparing the secrecy rate and the tolerable density of eavesdroppers in each phase, the secrecy rate of intra-cluster transmission can be concluded as follows.
Theorem 14. For the intra-cluster traffic, if the density of eavesdropper , then each legitimate node located within can achieve a secrecy rate of ,
Proof. Comparing the achievable secrecy rate in each phase, the rate bottleneck occurs in Phase 2. Since the information is transmitted hop by hop, we need to guarantee security in each phase. Thus, comparing the density of eavesdroppers in each phase, we can get that, if the density of eavesdroppers
, the secrecy rate of intra-cluster transmission is
(the proof is in
Appendix B). ☐
6. The Secrecy Transmission of Inter-Cluster Traffic
Since we focus on the cluster-sparse network, the node density outside the circular square is much lower. Thus, we cannot use the highway system constructed in
Section 5. However, according to the distribution of PPP, we can extract part of nodes with a density of
ϕ to build “information pipelines”, where
ϕ is smaller than
and is selected randomly and uniformly. As shown in
Figure 5, we use these “information pipelines” to connect the clusters.
Similarly, by virtue of percolation theory, we can divide the area into regular squares with a side length of , where is a constant. For some special large value , we can extract part of nodes to form “information pipelines”, which is similar to the highways constructed in the homogeneous network. However, due to the heterogeneity, each square contains difference nodes.
In the previous section, we have already achieved the secrecy rate in the cluster area through a highway system. Within the dense areas, information is transmitted by the routes formed by the highway system. Only if the destination is located in different clusters, the information will be delivered through the “information pipelines”. Similar to the derivation of intra-cluster transmission, the achievable secrecy rate of inter-cluster traffic can be obtained easily.
Borrowing the tools from percolation theory in [
6], we can construct
pipelines among clusters. All of these pipelines need to serve
clusters. Similar to Lemma 1 in [
22], a secrecy zone is employed to protect the secrecy transmission over a single hop, where the edge of the secrecy zone is not
c, but
. Correspondingly, we can build
pipelines between two neighboring clusters,
i.e., each cluster can enjoy
pipelines. By Theorem 6 in [
22], we can conclude that, if
, the secrecy rate of inter-cluster transmission is
.
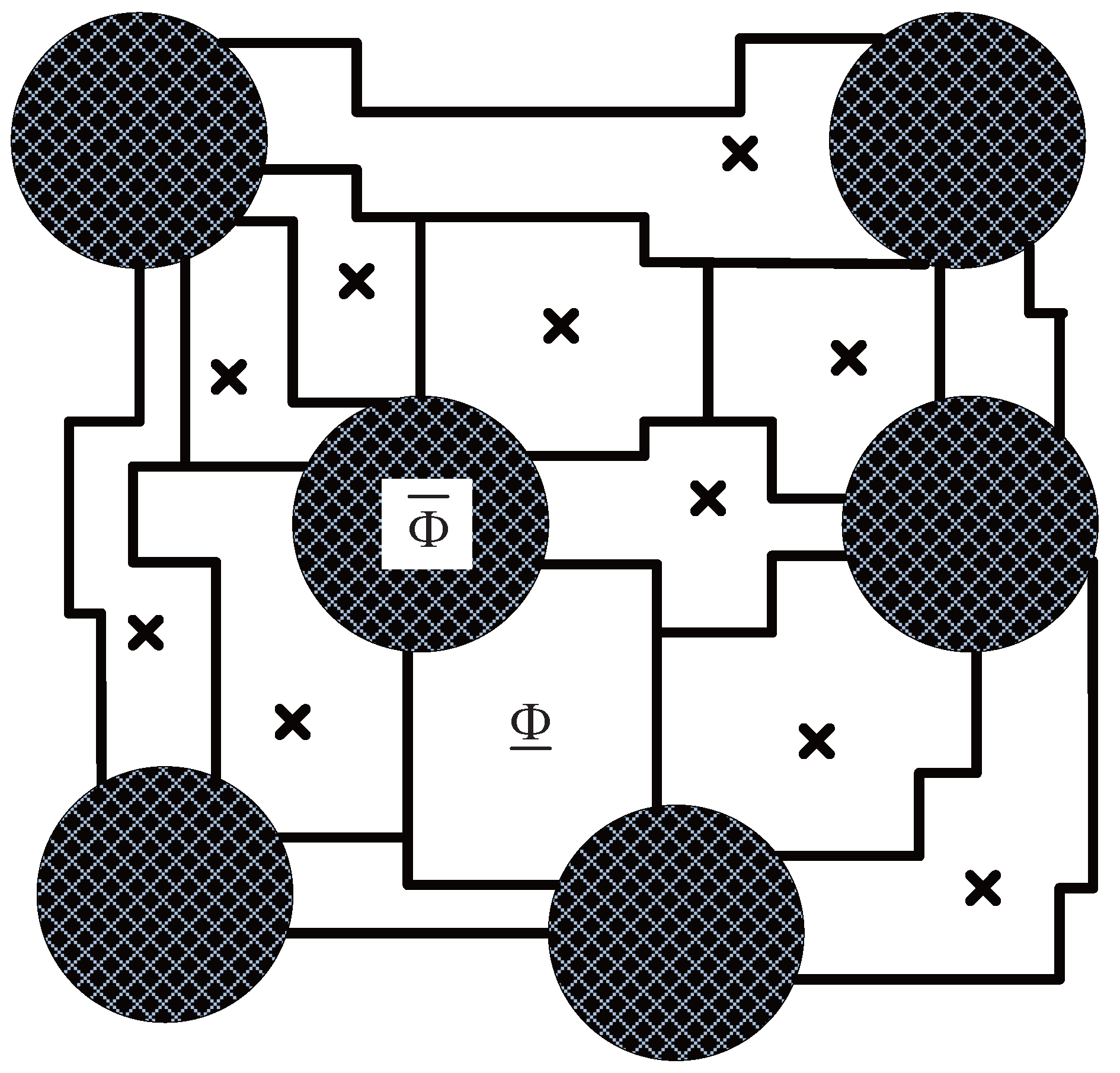
Figure 5.
An illustration of information pipelines among clusters. Since the minimum node density is , we can construct pipelines among clusters. The crosses denote the eavesdroppers.
Figure 5.
An illustration of information pipelines among clusters. Since the minimum node density is , we can construct pipelines among clusters. The crosses denote the eavesdroppers.
Theorem 15. For the inter-cluster transmission, the achievable secrecy rate is , if the density of the eavesdropper .
Figure 6 compares the throughput under homogeneous networks and heterogeneous networks. By observing the secrecy rate of intra-cluster and inter-cluster transmission, we find that the secrecy rate of intra-cluster transmission is higher than that of homogeneous networks; therefore, the bottleneck occurs in the inter-cluster transmission. This is due to the reduction of the number of highways caused by the lower density and, thereby, the amount of relaying traffic increasing. Particularly, when the network is transferred to a homogeneous network,
i.e.,
, the secrecy rate is
, and the tolerable density of the eavesdropper is
, which is the same result as that in homogeneous wireless networks [
22].
Figure 6.
An illustration of secrecy throughput. We also give a comparison with that in a homogeneous networks [
22].
Figure 6.
An illustration of secrecy throughput. We also give a comparison with that in a homogeneous networks [
22].