A Hybrid Sender- and Receiver-Initiated Protocol Scheme in Underwater Acoustic Sensor Networks
Abstract
:1. Introduction
2. Related Work
3. Problem Statements
3.1. Hidden-Node Problem in UWSNs
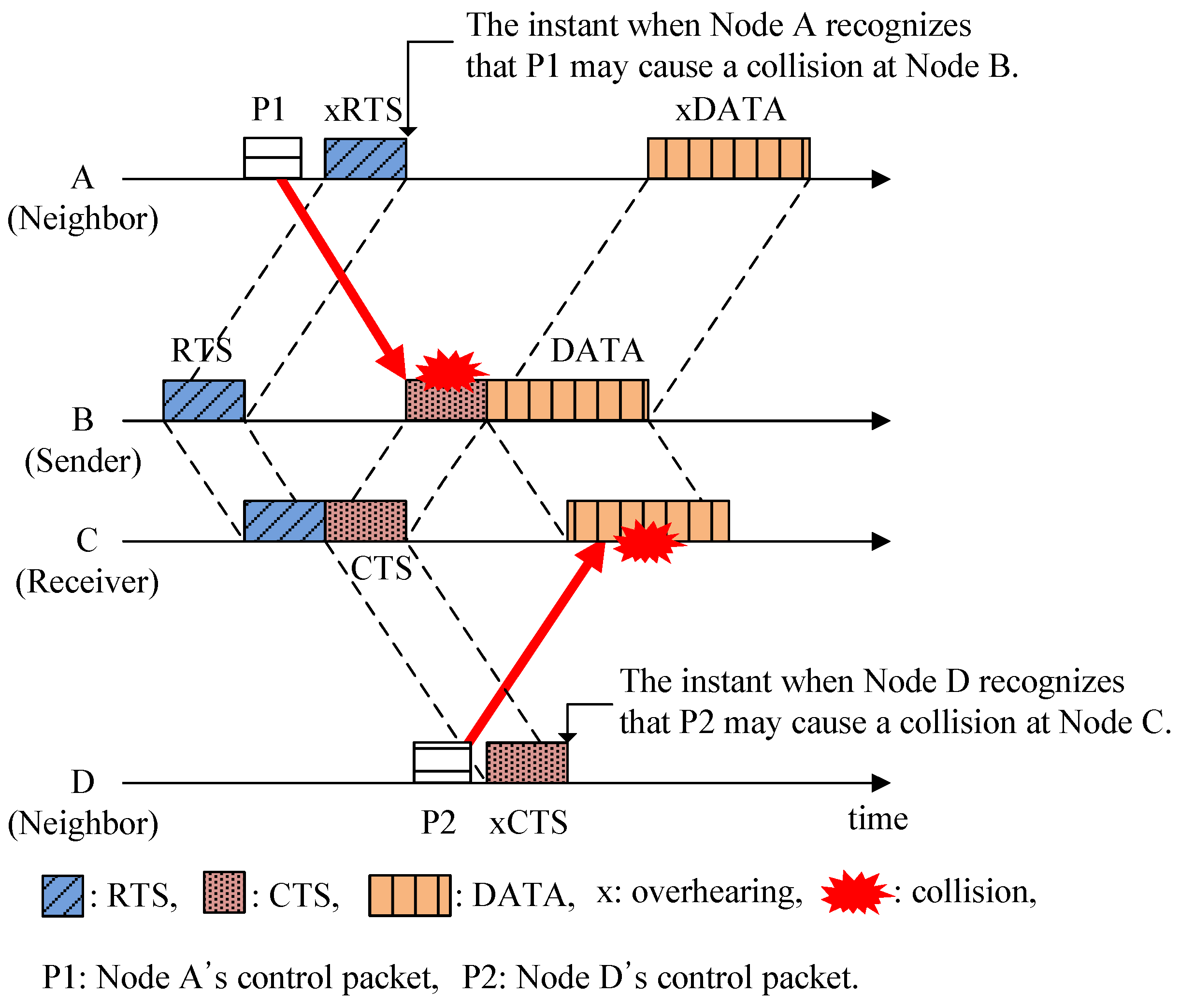
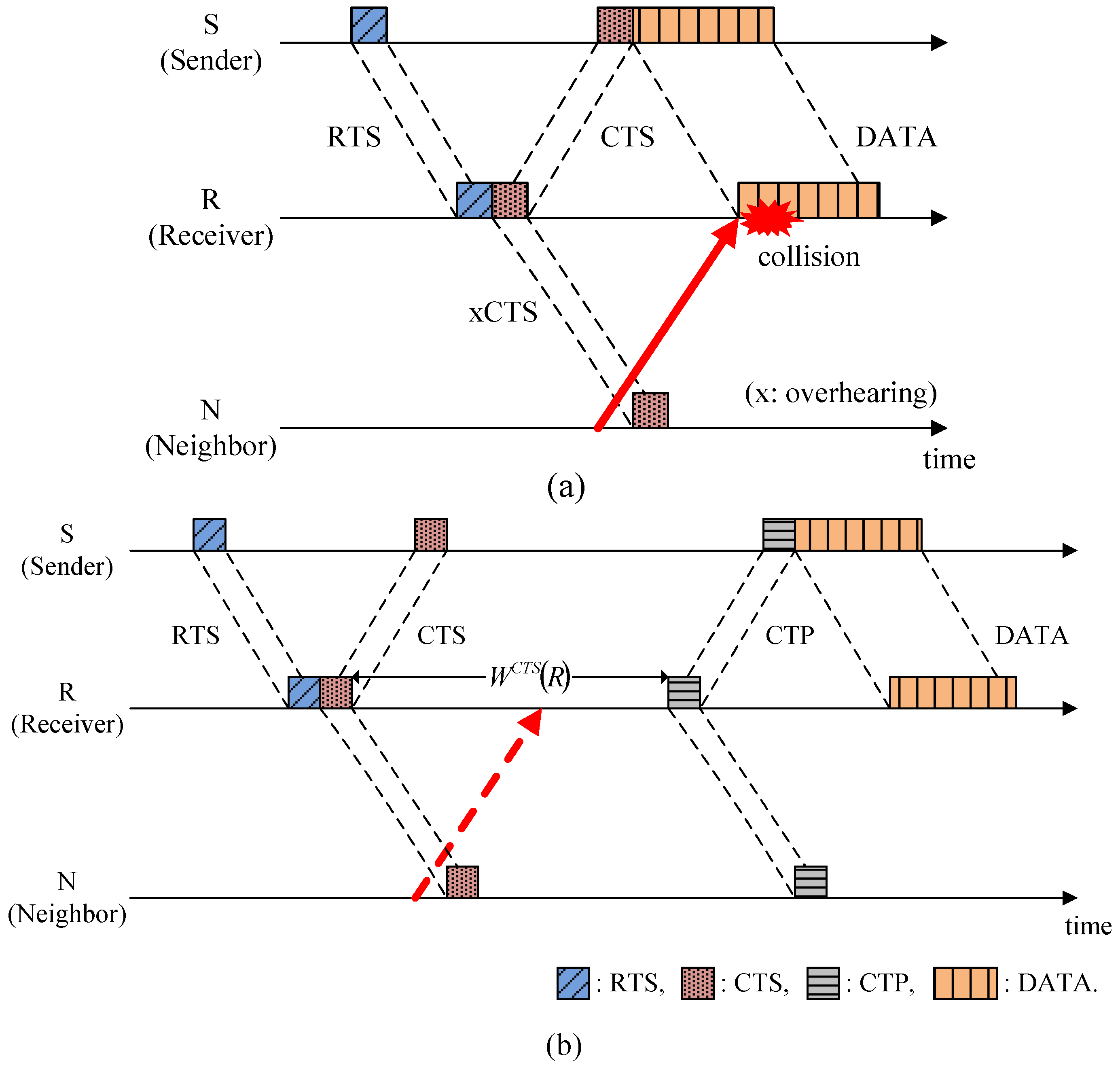
3.2. Spatial Unfairness Problem in UWSNs

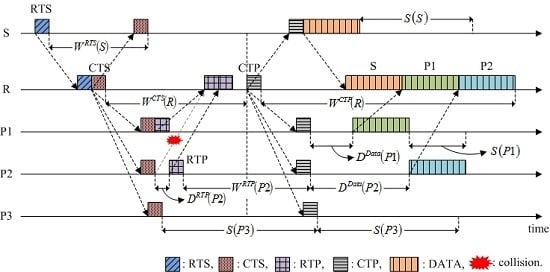
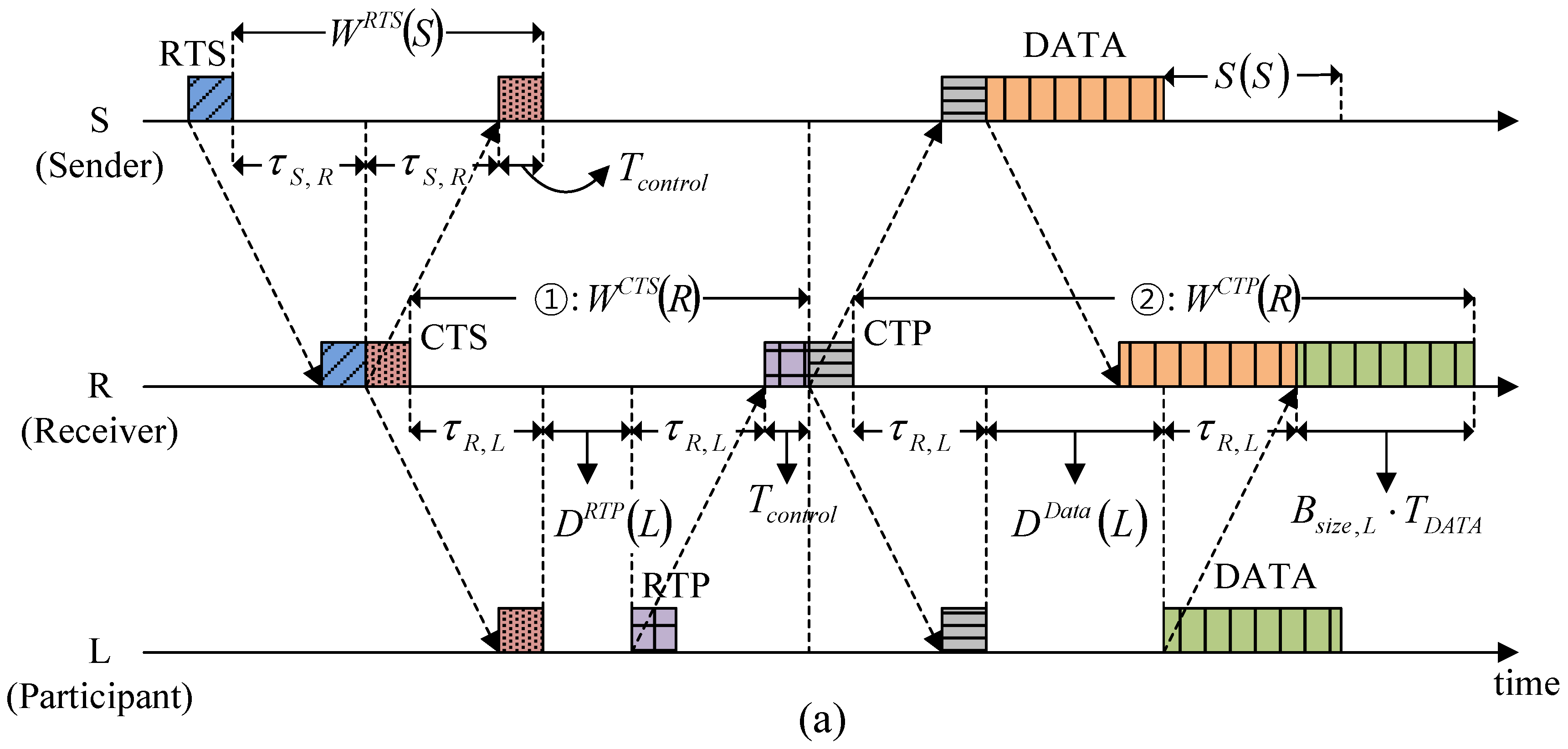
4. Proposed HSR Protocol
4.1. System Description
4.1.1. Assumptions
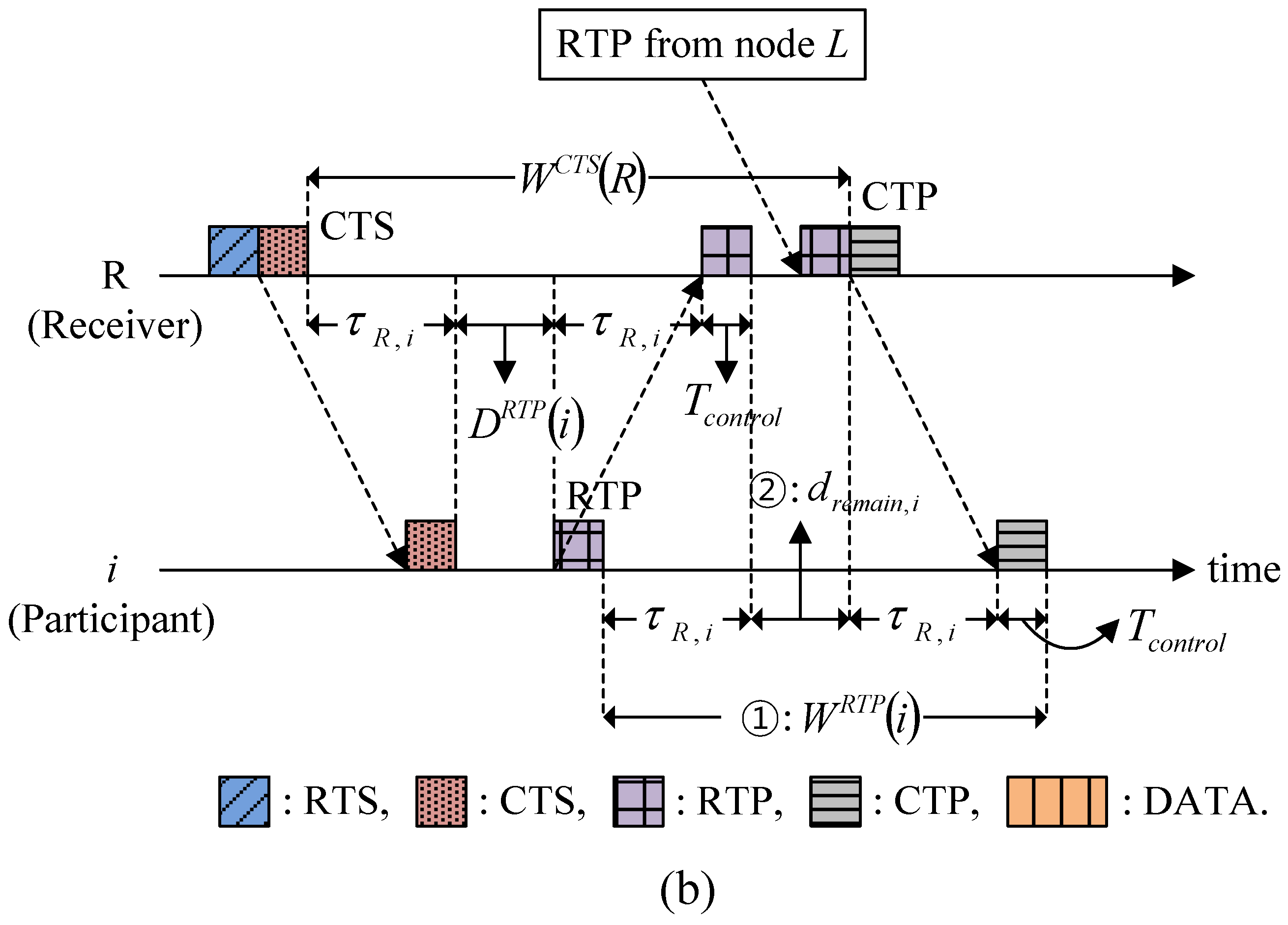
4.1.2. Time Duration Parameters in HSR

4.2. Fundamental Operation and Features
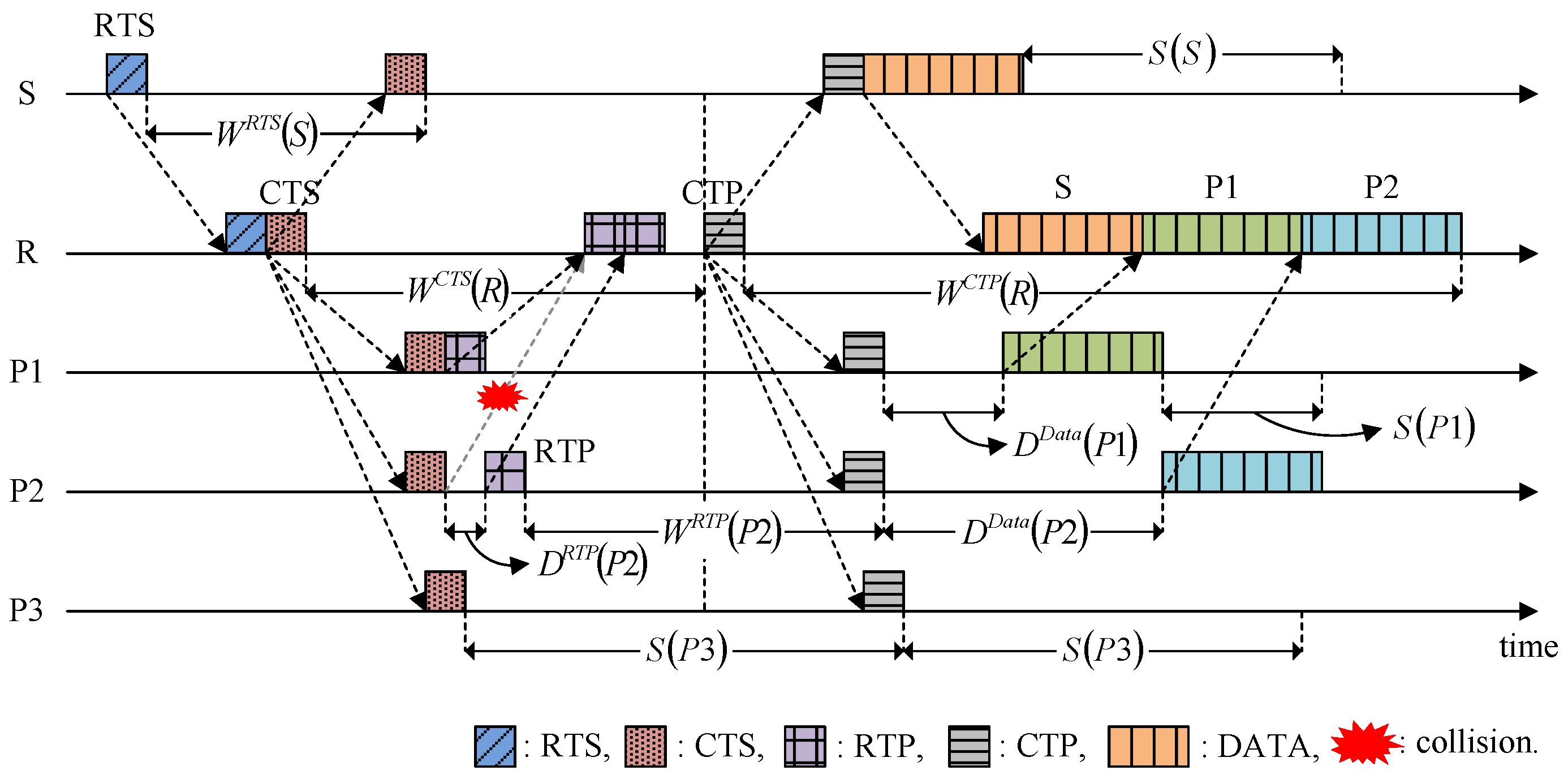
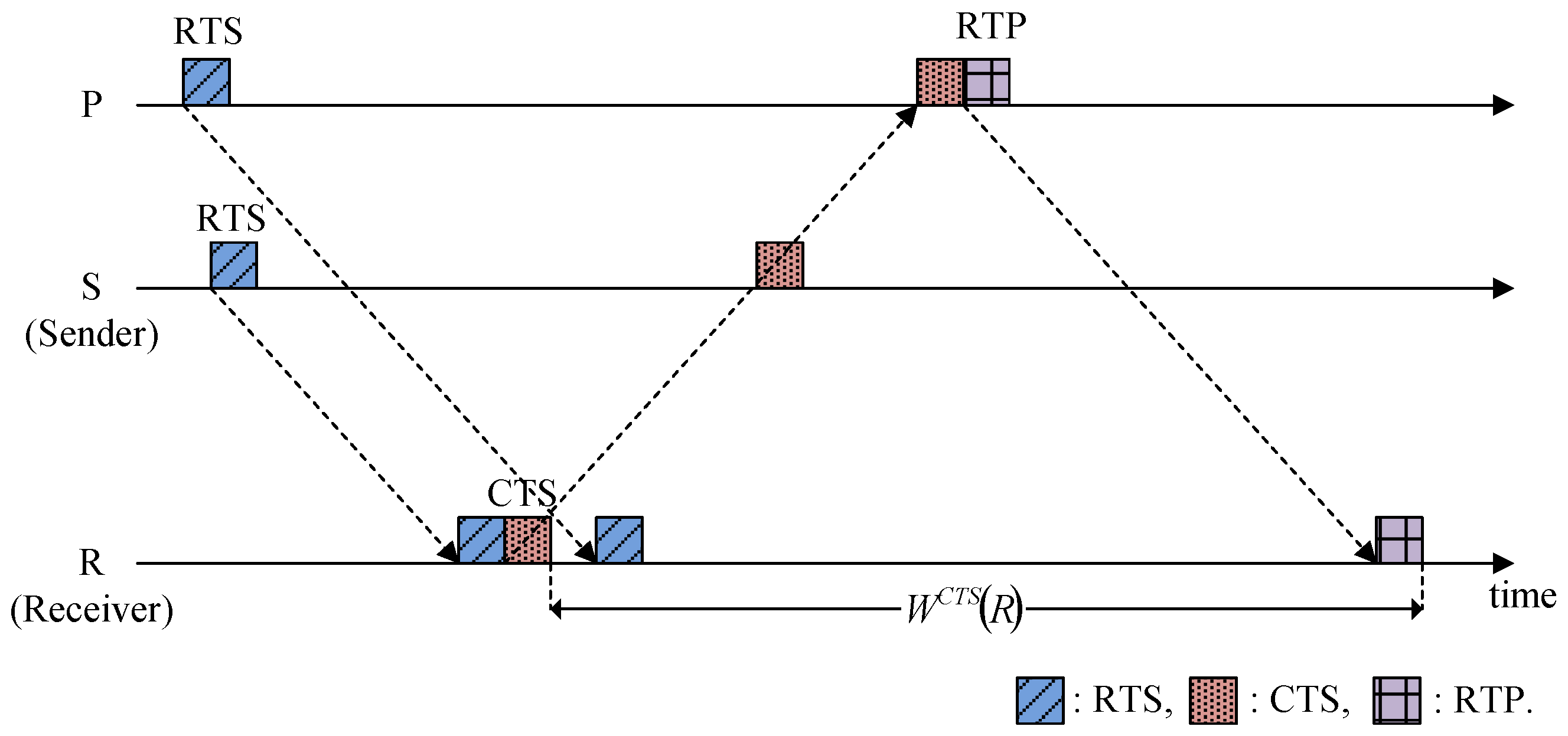
4.3. Calculating the Time Duration Parameters
4.3.1. Delay for the RTP and Data Transmission
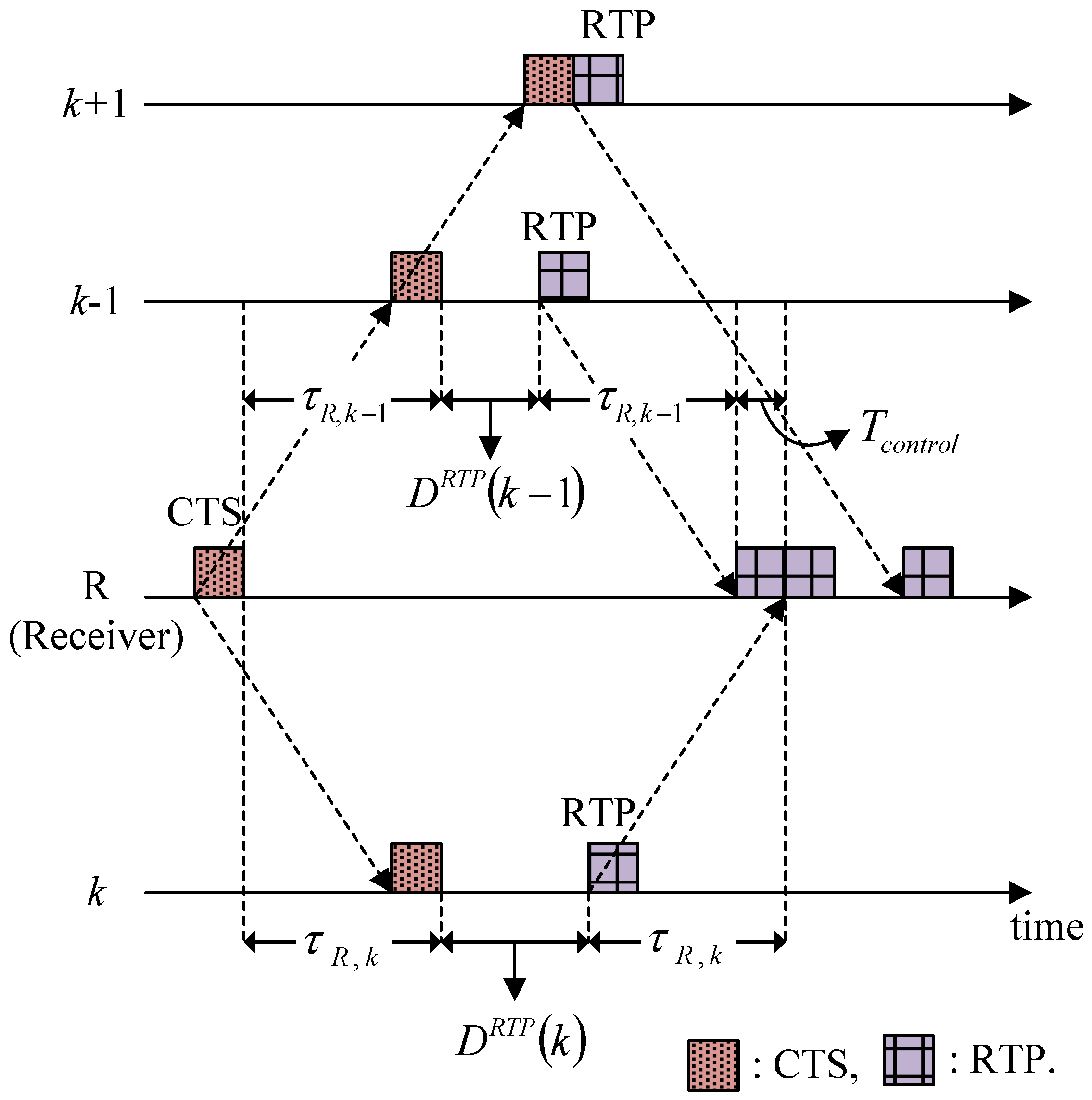
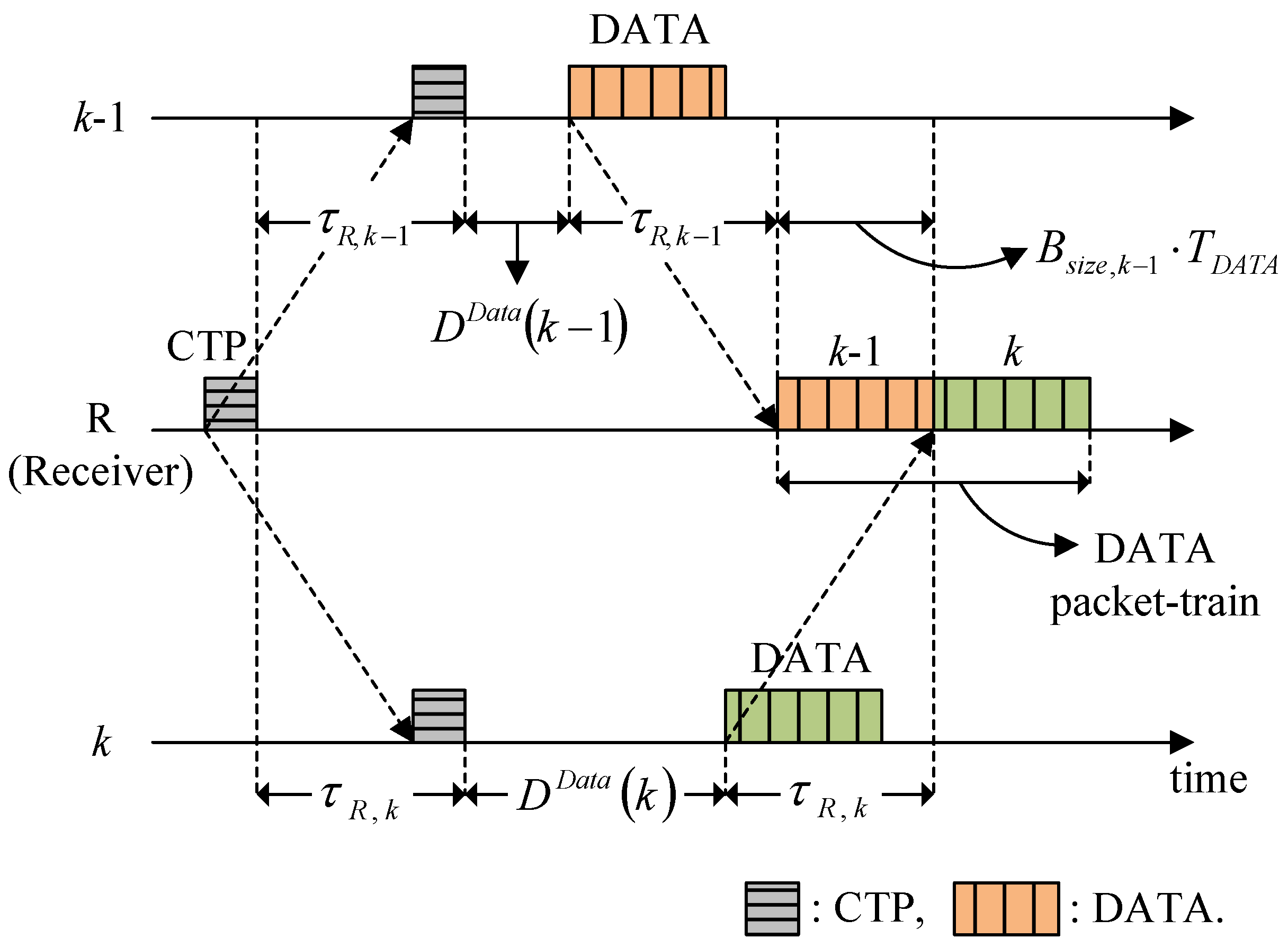
4.3.2. Waiting for Responses to RTS, CTS, RTP, and CTP
5. Simulations and Results
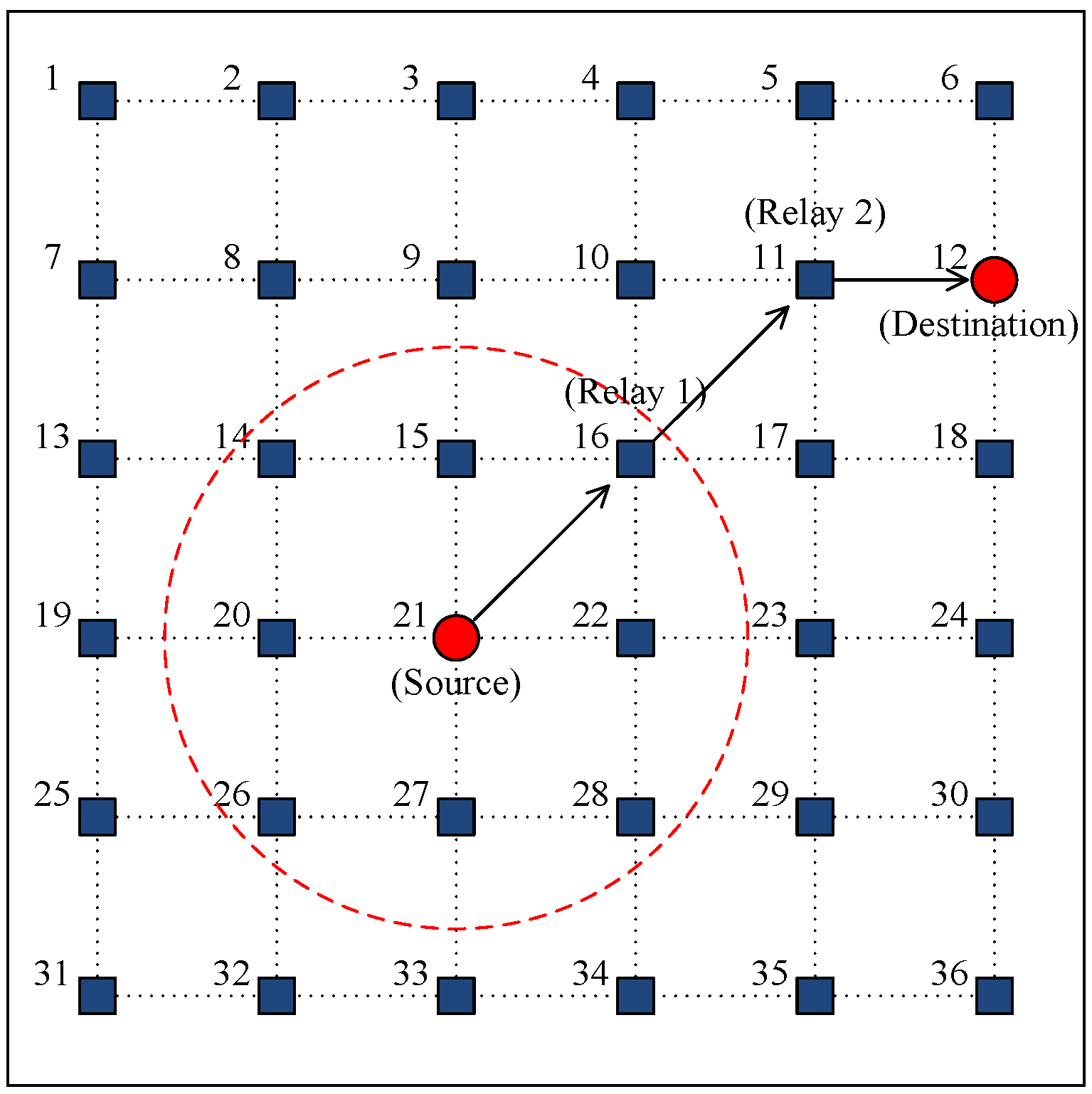
5.1. Simulation Model
| Parameter | Value |
|---|---|
| Transmission Rate | 9600 bps |
| Size of Data Packet | 1200 bits |
| Size of Control Packet | 120 bits |
| Minimum Back-Off Counter | 1 |
| Maximum Back-Off Counter | 64 |
| Capacity of Buffer | 300 packets |
| Speed of Acoustic Wave | 1500 m/s |
5.2. Simulation Results
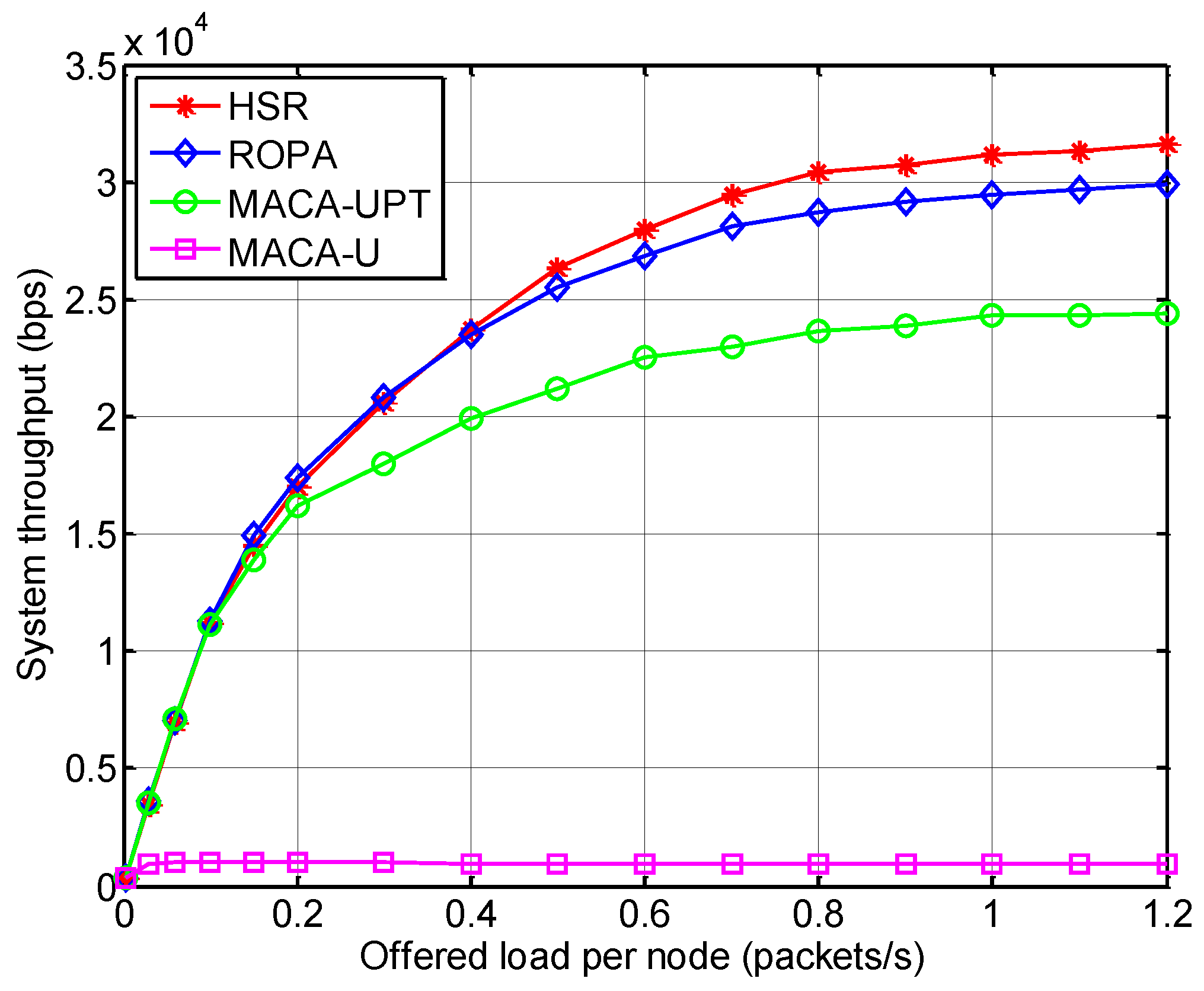
5.2.1. Throughput and Delay Analysis


| Feature | Handshake-Sharing | Packet-Train Method | Solving the Hidden-Node Problem | |
|---|---|---|---|---|
| MAC Protocol | ||||
| HSR | O | O | O | |
| ROPA | O | O | X | |
| MACA-UPT | X | O | X | |
| MACA-U | X | X | X | |
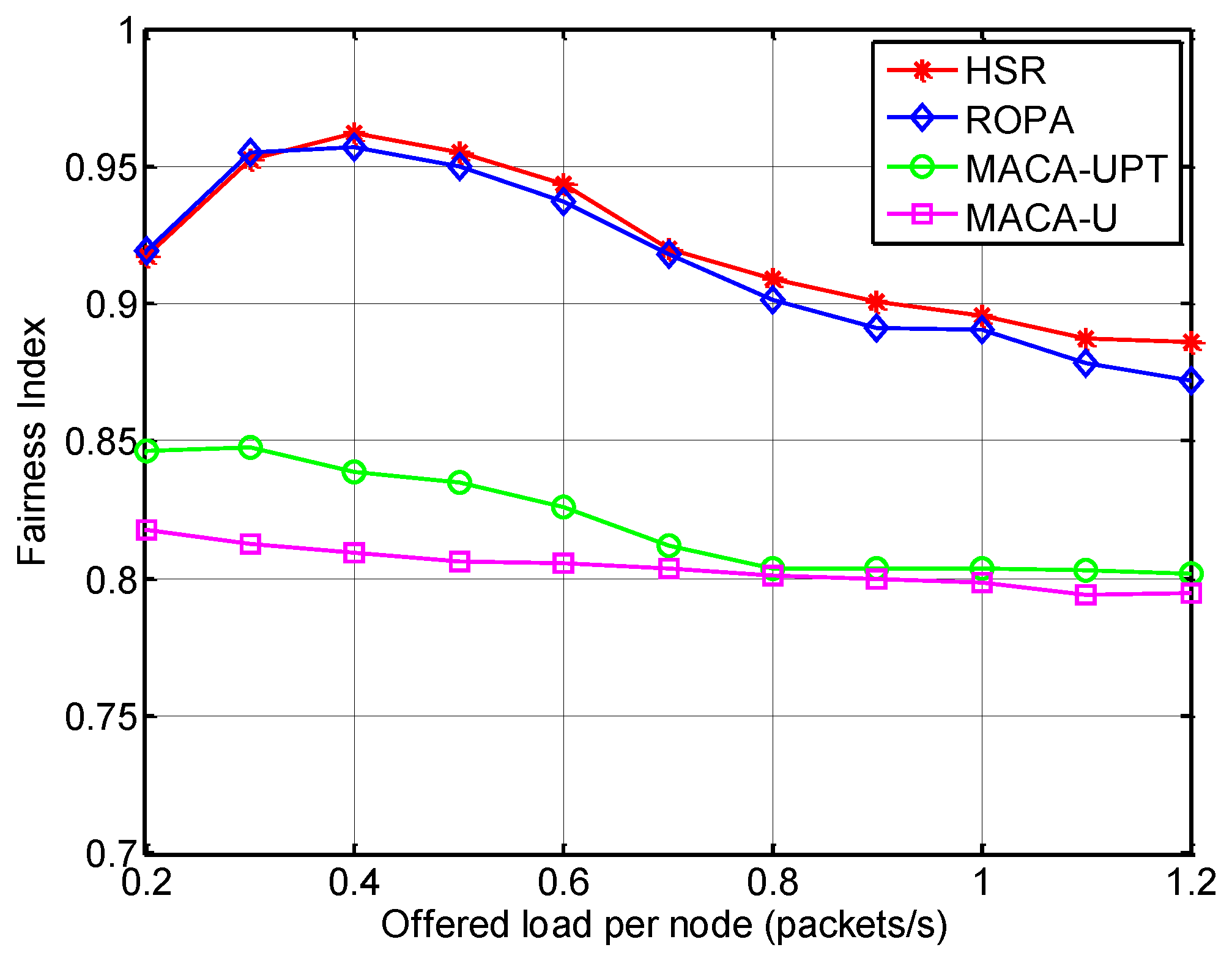
5.2.2. Analysis of Spatial Fairness
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Akyildiz, I.F.; Pompili, D.; Melodia, T. Underwater Acoustic sensor networks: Research challenges. Ad Hoc Netw. 2005, 3, 257–279. [Google Scholar] [CrossRef]
- Zhang, B.; Sukhatme, G.S.; Requicha, A.G. Adaptive sampling for marine microorganism monitoring. In Proceedings of the IEEE/RSJ International Conference on Intelligent Robots and System (IROS 2004), Sendai, Japan, 28 September–2 October 2004; pp. 1115–1122.
- Chen, K.; Ma, M.; Cheng, E.; Yuan, F.; Su, W. A survey on mac protocols for underwater wireless sensor networks. IEEE Commun. Surv. Tutor. 2014, 16, 1433–1447. [Google Scholar] [CrossRef]
- Partan, J.; Kurose, J.; Levine, B.N. A survey of practical issues in underwater networks. In Proceedings of the 1st ACM International Workshop on Underwater Networks (WUWNet), Los Angeles, CA, USA, 25 September 2006; pp. 17–24.
- Chitre, M.; Shahabudeen, S.; Stojanovic, M. Underwater acoustic communication and networks: Recent advances and future challenges. Mar. Technol. Soc. J. 2008, 42, 103–116. [Google Scholar] [CrossRef]
- Karn, P. MACA: A new channel access method for packet radio. In Proceedings of the 9th Computer Networking Conference, London, ON, Canada, 22 September 1990; pp. 134–140.
- Ng, H.H.; Soh, W.S.; Montani, M. MACA-U: A media access protocol for underwater acoustic networks. In Proceedings of the IEEE Global Telecommunications Conference 2008, New Orleans, LO, USA, 30 November–4 December 2008.
- Guo, X.; Frater, M.R.; Ryan, M.J. Design of a propagation-delay-tolerant mac protocol for underwater acoustic sensor networks. IEEE J. Ocean. Eng. 2009, 34, 170–180. [Google Scholar] [CrossRef]
- Chirdchoo, N.; Soh, W.S.; Chua, K.C. MACA-MN: A MACA-based MAC protocol for underwater acoustic networks with packet train for multiple neighbors. In Proceedings of the IEEE Vehicular Technology Conference, Singapore, 11–14 May 2008; pp. 46–50.
- Ng, H.H.; Soh, W.S.; Montani, M. BiC-MAC: Bidirectional-concurrent mac protocol with packet bursting for underwater acoustic networks. In Proceedings of the MTS/IEEE OCEANS 2010, Seattle, WA, USA, 20–23 September 2010.
- Chirdchoo, N.; Soh, W.S.; Chua, K. RIPT: A receiver-initiated reservation-based protocol for underwater acoustic networks. IEEE J. Sel. Areas Commun. 2008, 26, 1744–1753. [Google Scholar] [CrossRef]
- Ng, H.H.; Soh, W.S.; Montani, M. An Underwater Acoustic MAC protocol using reverse opportunistic packet appending. Comput. Netw. 2013, 57, 2733–2751. [Google Scholar] [CrossRef]
- Molins, M.; Stojanovic, M. Slotted FAMA: A MAC protocol for underwater acoustic networks. In Proceedings of the IEEE OCEANS’06 Asia Pacific, Singapore, 16–19 May 2006; pp. 16–19.
- Peleato, B.; Stojanovic, M. Distance aware collision avoidance protocol for ad-hoc underwater acoustic sensor networks. IEEE Commun. Lett. 2007, 11, 1025–1027. [Google Scholar] [CrossRef]
- Liao, W.H.; Huang, C.C. SF-MAC: A spatially fair MAC protocol for underwater acoustic sensor networks. IEEE Sens. J. 2012, 12, 1686–1694. [Google Scholar] [CrossRef]
- Lin, W.; Cheng, E.; Yuan, F. EHM: A novel efficient protocol based handshaking mechanism for underwater acoustic sensor networks. Wirel. Netw. 2013, 19, 1051–1061. [Google Scholar] [CrossRef]
- Xie, P.; Cui, J.H. R-MAC: An energy-efficient MAC protocol for underwater sensor networks. In Proceedings of the IEEE International Conference on Wireless Algorithms, Systems and Applications 2007 (WASA 2007), Chicago, IL, USA, 1–3 August 2007; pp. 187–198.
- LAN/MAN (IEEE 802) Standards Committee. Wireless LAN Media Access Control (MAC) and Physical Layer (PHY) Specifications; IEEE: New York, NY, USA, 1999. [Google Scholar]
- LinkQuest Inc. Available online: http://www.link-quest.com (accessed on 30 August 2014).
- Lee, J.W.; Cho, H.S. Cascading multi-hop reservation and transmission in underwater acoustic sensor networks. Sensors 2014, 14, 18390–18409. [Google Scholar] [CrossRef] [PubMed]
- Syed, A.; Ye, W.; Heidemann, J. Comparison and evaluation of the T-Lohi MAC for underwater acoustic sensor networks. IEEE J. Sel. Areas Commun. 2008, 26, 1731–1743. [Google Scholar] [CrossRef]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, J.-W.; Cho, H.-S. A Hybrid Sender- and Receiver-Initiated Protocol Scheme in Underwater Acoustic Sensor Networks. Sensors 2015, 15, 28052-28069. https://doi.org/10.3390/s151128052
Lee J-W, Cho H-S. A Hybrid Sender- and Receiver-Initiated Protocol Scheme in Underwater Acoustic Sensor Networks. Sensors. 2015; 15(11):28052-28069. https://doi.org/10.3390/s151128052
Chicago/Turabian StyleLee, Jae-Won, and Ho-Shin Cho. 2015. "A Hybrid Sender- and Receiver-Initiated Protocol Scheme in Underwater Acoustic Sensor Networks" Sensors 15, no. 11: 28052-28069. https://doi.org/10.3390/s151128052