The Applications of Decision-Level Data Fusion Techniques in the Field of Multiuser Detection for DS-UWB Systems
Abstract
:1. Introduction
2. Problem Statement
2.1. Some Typical MUD Algorithms for DS-UWB Systems
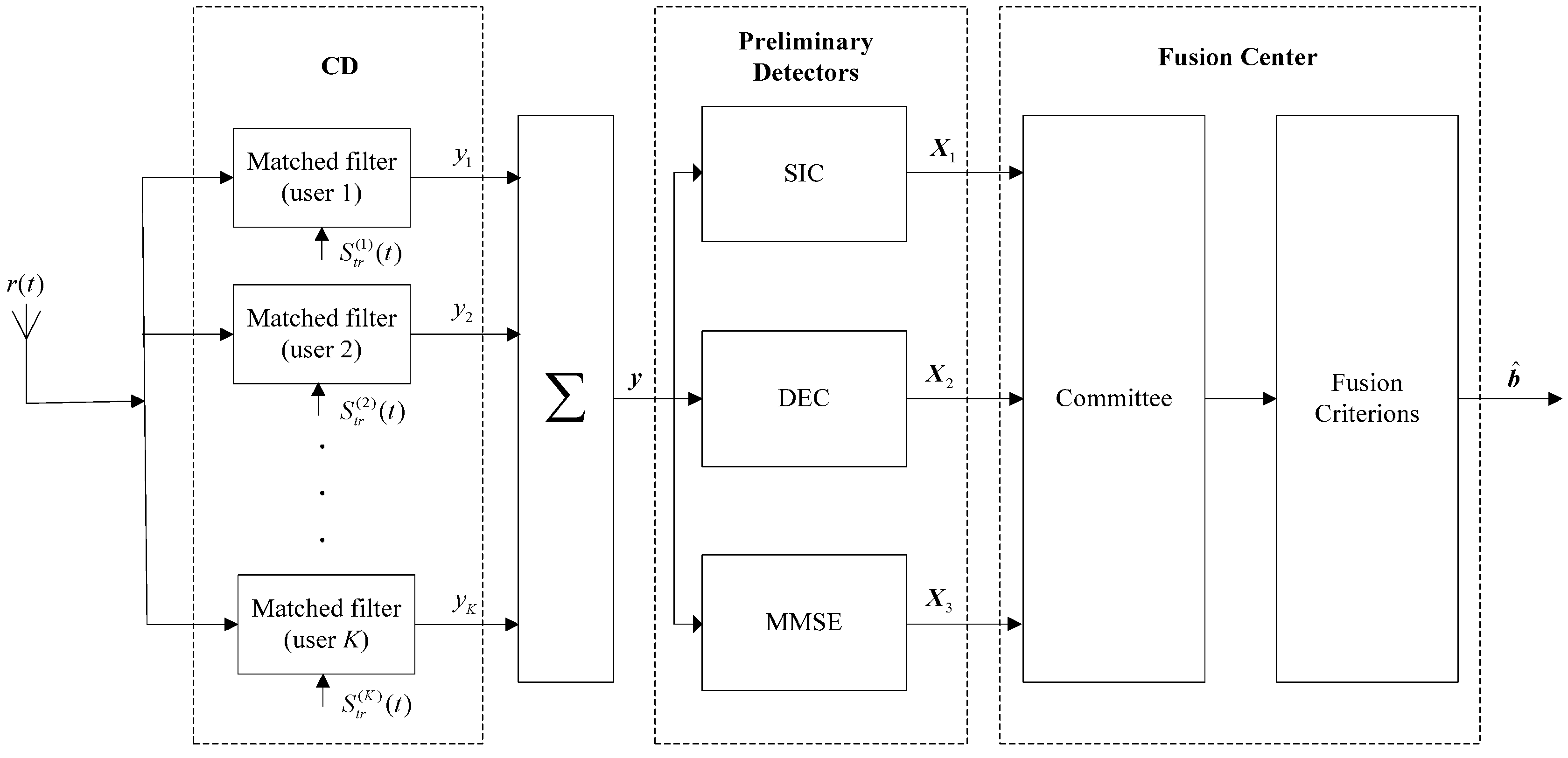
2.2. Decision-Level Fusion Based MUD System Model
- (1)
- The outputs of CD y = (y1, y2, …, yK)T are passed to the preliminary sub-optimal detectors, including SIC, DEC, and MMSE detectors;
- (2)
- The preliminary decisions of SIC, DEC, and MMSE (let X1, X2 and X3) are sent to the fusion center;
- (3)
- The fusion center consists of two parts: committee and fusion criterions. Depending on different decision-level fusion criterions (DFCs), the committee can make a different final decision on the basis of these preliminary decisions.
- (4)
- This scheme is not distributed in fact, for it only needs one antenna to receive signals. Consequently, the computational complexity and apparatus integration are saved.
3. Optimal Decision-Level Fusion Criterion (O-DFC) and Its Simplified Form
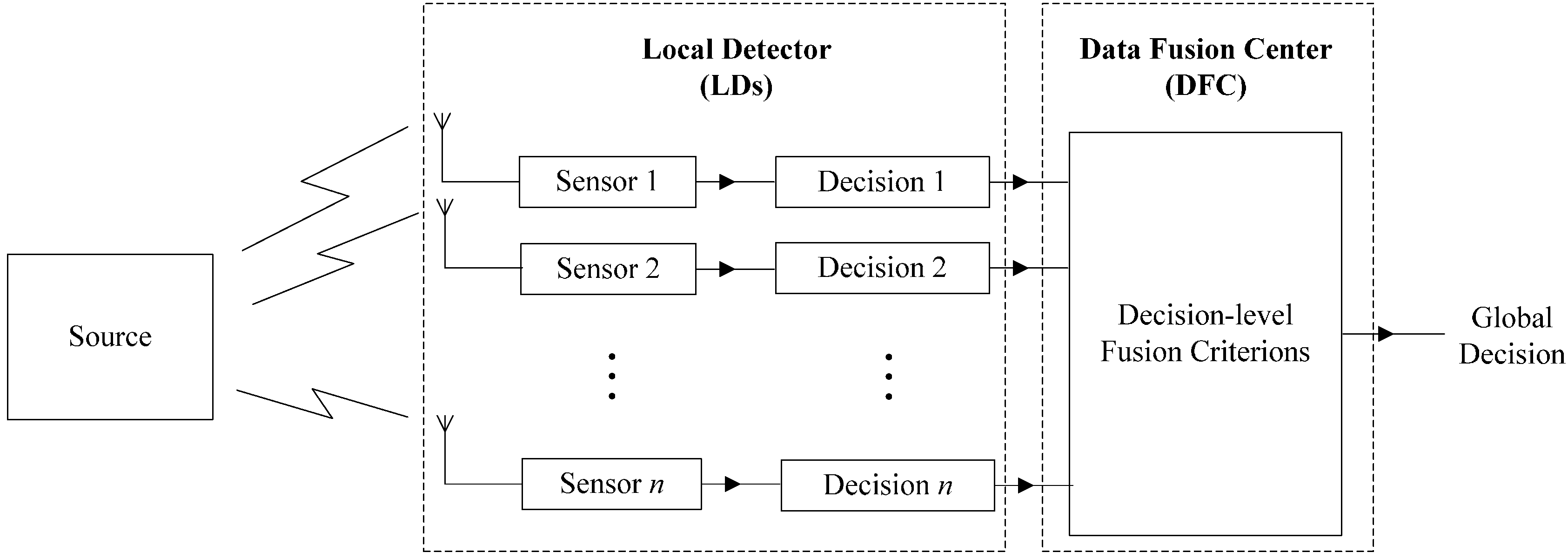
3.1. Optimal Decision-Level Fusion Criterion (O-DFC)
3.2. The Simplified form of O-DFC: the Majority Voting Decision-Level Fusion Criterion (MV-DFC)
4. Two Improved Decision-Level Fusion Criterions for MUD
4.1. The Problems in O-DFC and MV-DFC
4.2. The Chairman Arbitrating Decision-Level Fusion Criterion (CA-DFC)
4.3. The Veto Logic Decision-Level Fusion Criterion (VL-DFC)
- (1)
- Calculate the K-dimensional voting vector U by Equation (30);
- (2)
- Construct a simplified L-dimensional solution space based on U, and L is the number of undetermined bits in U;
- (3)
- Compare the 2L likely solutions in this space, and consider the solution that has the largest value of Equation (27) as the final decision made by the chairman.
5. Numerical Results and Analysis
| System | DS-UWB |
| Modulation Mode | BPSK |
| Pseudo random sequences (PRS) | m sequences |
| The length of PRS | 31 |
| Communication channel | AWGN or IEEE 802.15.3a (CM2) |
| The number of testing information symbols | 105 |
| The width of UWB pulse | 0.7531 ns |
| The pulse repetition period | ≈2 ns |
| The number of active users | K = 5, 10, 15, 20 |
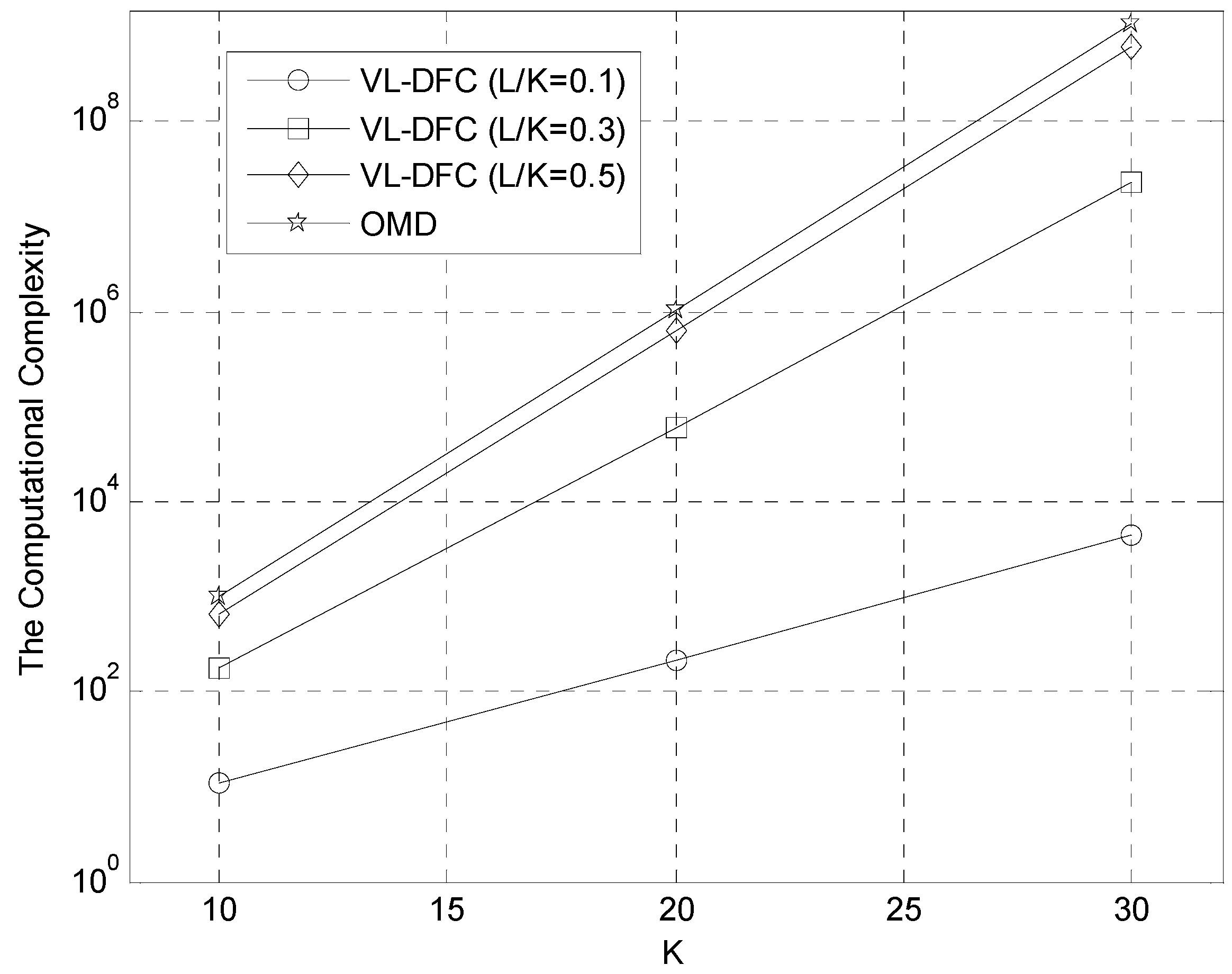
5.1. The Computational Complexity Comparison
| MUD Algorithms | Calculation Number |
|---|---|
| CA-DFC | n |
| VL-DFC | 2L |
| OMD | 2K |
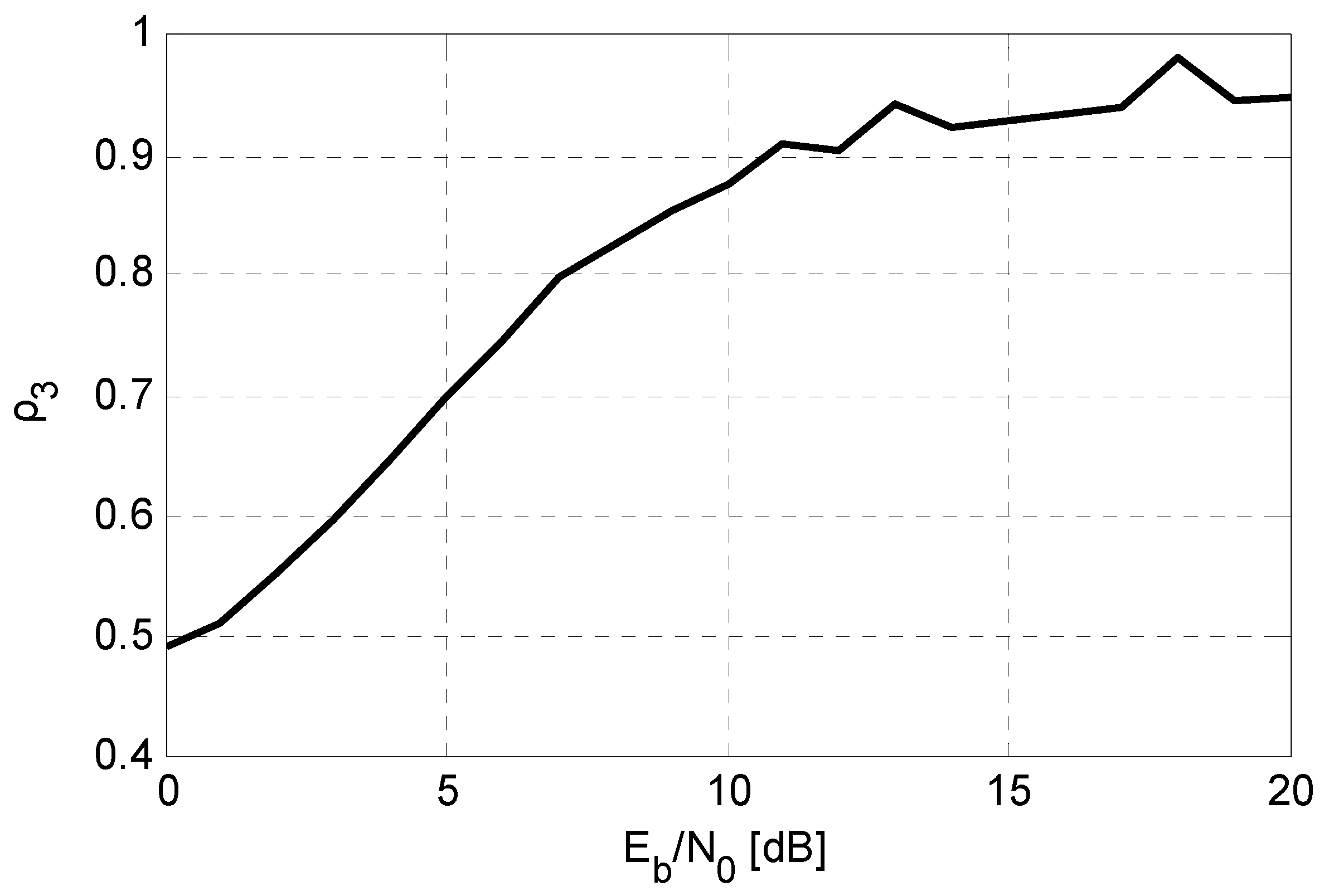
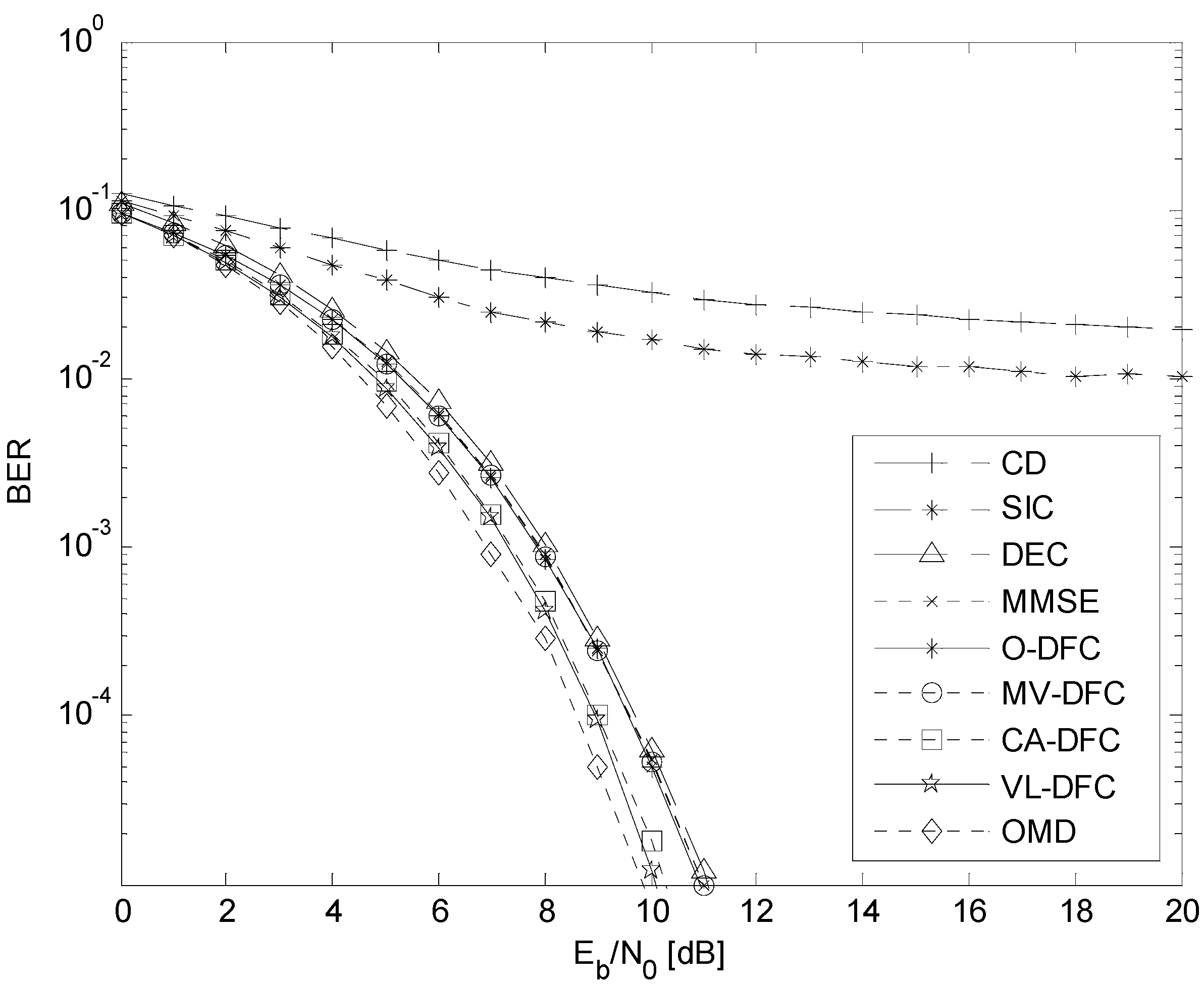
5.2. The BER Performance versus Eb/N0 Comparison
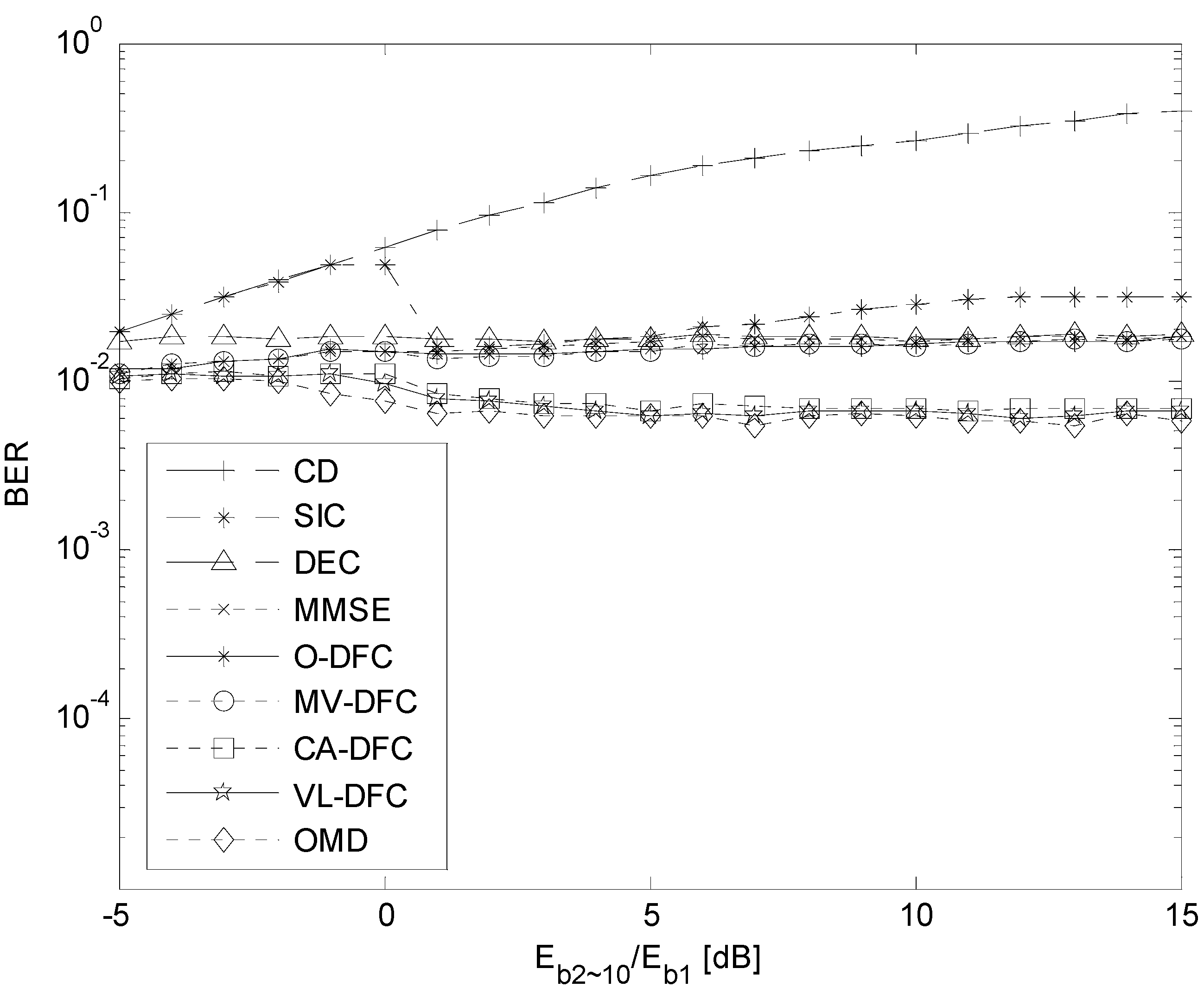
5.3. The NFE Resistant Ability Comparison
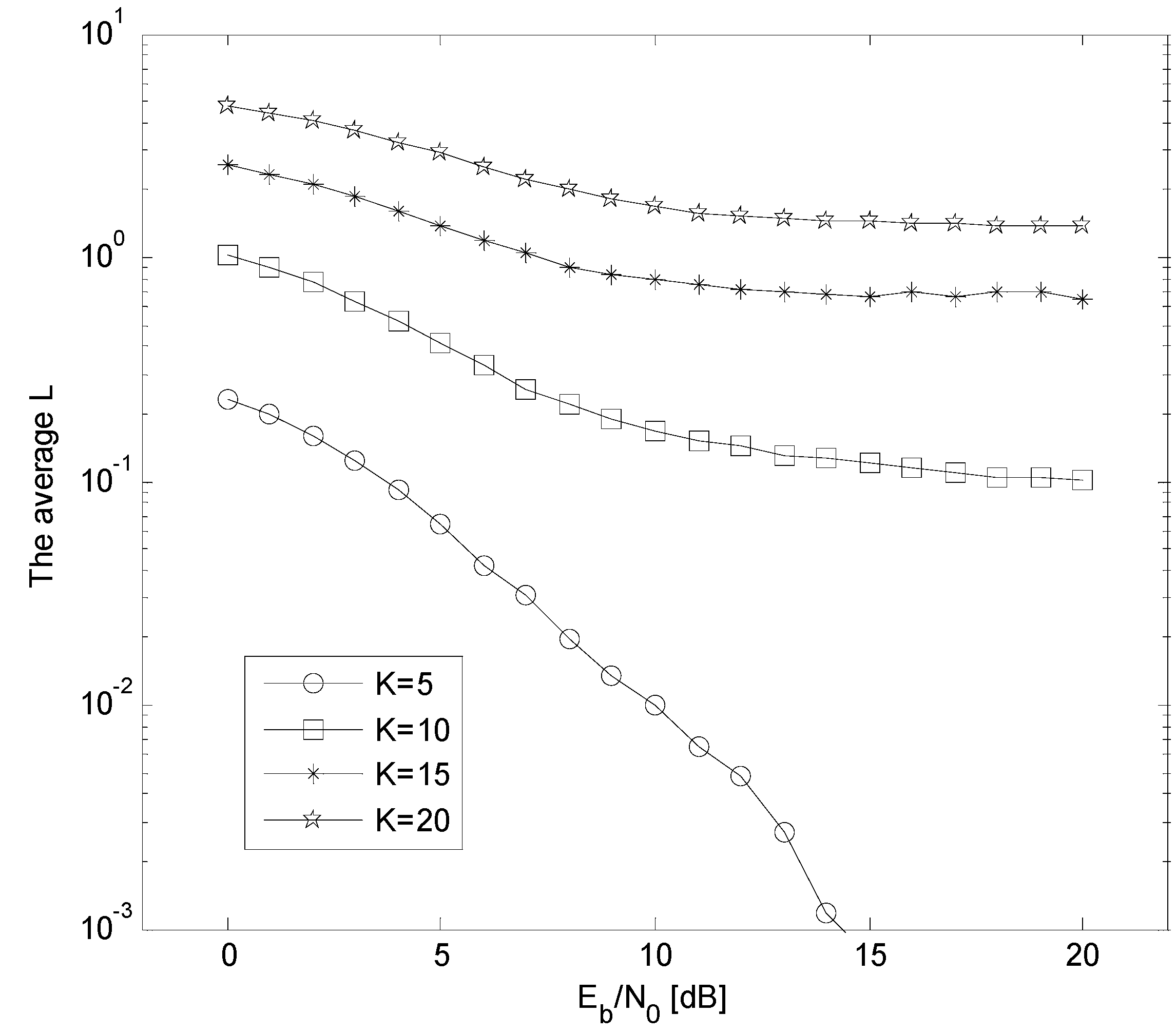
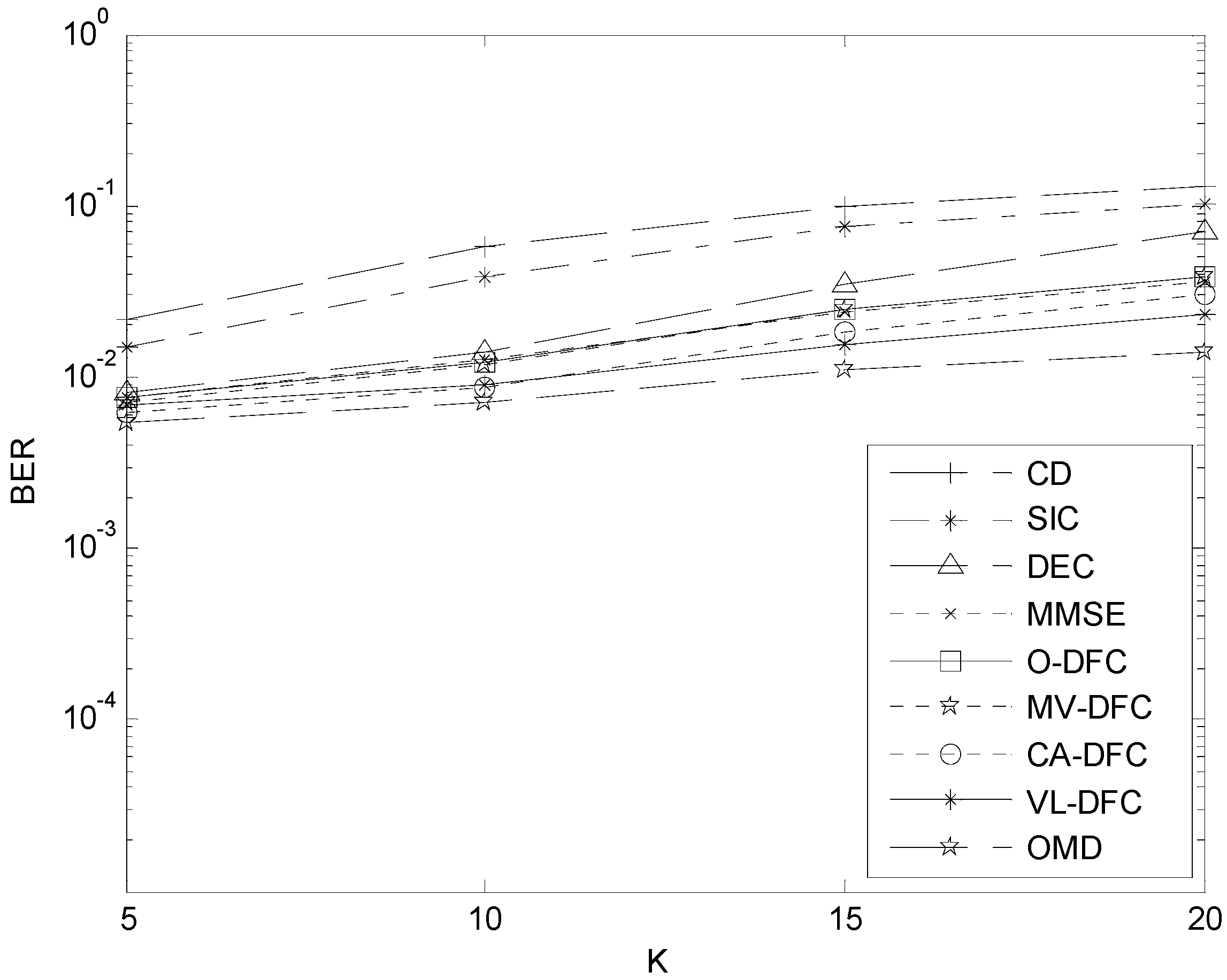
5.4. The BER Performance versus K Comparison
5.5. The BER Performance Comparison in Multipath Environment

6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- White, F.E. Data Fusion Lexicon: Data Fusion Subpanel of the Joint Directors of Laboratories Technical Panel for C3; IEEE Trans.: San Diego, CA, USA, 1991. [Google Scholar]
- Khaleghi, B.; Khamis, A.; Karray, F.O.; Razavi, S.N. Multisensor data fusion: A review of the state-of-the-art. Inf. Fusion 2013, 14, 28–44. [Google Scholar] [CrossRef]
- Saporta, G. Data fusion and data grafting. Comput. Stat. Data Anal. 2002, 38, 465–473. [Google Scholar] [CrossRef]
- Cho, S.; Baek, S.; Kim, J.S. Exploring artificial intelligence-based data fusion for conjoint analysis. Expert Syst. Appl. 2003, 24, 287–294. [Google Scholar] [CrossRef]
- Dasarathy, B.V. Decision Fusion; IEEE Computer Society Press: Los Alamitos, CA, USA, 1994. [Google Scholar]
- Dasarathy, B.V. Decision fusion benefits assessment in a three-sensor suite framework. Opt. Eng. 1998, 37, 354–369. [Google Scholar] [CrossRef]
- Mangai, U.G.; Samanta, S.; Das, S.; Chowdhury, P.R. A survey of decision fusion and feature fusion strategies for pattern classification. IETE Tech. Rev. 2010, 27, 293–307. [Google Scholar] [CrossRef]
- Xu, L.; Krzyżak, A.; Suen, C.Y. Methods of combining multiple classifiers and their applications to handwriting recognition. IEEE Trans. Syst. Man Cybern. 1992, 22, 418–435. [Google Scholar] [CrossRef]
- Kittler, J.; Hatef, M.; Duin, R.P.W.; Matas, J. On combining classifiers. IEEE Trans. Pattern Anal. Mach. Intell. 1998, 20, 226–239. [Google Scholar] [CrossRef]
- Littlestone, N.; Warmuth, M.K. The weighted majority algorithm. Inf. Comput. 1994, 108, 212–261. [Google Scholar] [CrossRef]
- Huang, Y.S.; Suen, C.Y. A method of combining multiple experts for the recognition of unconstrained handwritten numerals. IEEE Trans. Pattern Anal. Mach. Intell. 1995, 17, 90–94. [Google Scholar] [CrossRef]
- Kuncheva, L.I. Combining Pattern Classifiers: Methods and Algorithms; John Wiley & Sons: Hoboken, NJ, USA, 2004. [Google Scholar]
- Ho, T.K.; Hull, J.J.; Srihari, S.N. Decision combination in multiple classifier systems. IEEE Trans. Pattern Anal. Mach. Intell. 1994, 16, 66–75. [Google Scholar]
- Lam, L.; Suen, C.Y. Optimal combinations of pattern classifiers. Pattern Recognit. Lett. 1995, 16, 945–954. [Google Scholar] [CrossRef]
- Kuncheva, L.I.; Bezdek, J.C.; Duin, R.P.W. Decision templates for multiple classifier fusion: An experimental comparison. Pattern Recognit. 2001, 34, 299–314. [Google Scholar] [CrossRef]
- Shafer, G. A Mathematical Theory of Evidence; Princeton University Press: Princeton, NJ, USA, 1976. [Google Scholar]
- Liu, K.H.; Cai, L.; Shen, X.S. Exclusive-region based scheduling algorithms for UWB WPAN. IEEE Trans. Wirel. Commun. 2008, 7, 933–942. [Google Scholar]
- Li, Z.P.; Kuo, G.S. Layered MAC for high-rate UWB WPAN system. In Proceedings of the IEEE 64th Vehicular Technology Conference, Melbourne, Australia, 7–10 May 2006.
- Aripin, N.M.; Fisal, N. Analysis of channel time allocations for MPEG-4 video transmission over UWB WPAN. In Proceedings of the IEEE Symposium on Industrial Electronics & Applications, (ISIEA 2009), Kuala Lumpur, Malaysia, 4–6 October 2009; Volume 2, pp. 705–710.
- Yoon, Y.C.; Kohno, R. Optimum multi-user detection in ultra-wideband (UWB) multiple-access communication systems. In Proceedings of the IEEE International Conference on Communications, New York, NY, USA; 2002. [Google Scholar]
- Tan, S.S.; Nallanathan, A.; Kannan, B. Performance of DS-UWB multiple-access systems with diversity reception in dense multipath environments. IEEE Trans. Veh. Technol. 2006, 55, 1269–1280. [Google Scholar] [CrossRef]
- Sato, H.; Ohtsuki, T. Frequency domain channel estimation and equalisation for direct sequence-ultra wideband (DS-UWB) system. IEE Proc. Commun. 2006, 153, 93–98. [Google Scholar] [CrossRef]
- Scholtz, R. Multiple access with time-hopping impulse modulation. In Proceedings of the IEEE MILCOM’93, Boston, MA, USA, 11–14 October 1993; Volume 2, pp. 447–450.
- Win, M.Z.; Scholtz, R.A. Ultra-wide bandwidth time-hopping spread-spectrum impulse radio for wireless multiple-access communications. IEEE Trans. Commun. 2000, 48, 679–689. [Google Scholar] [CrossRef]
- Somayazulu, V.S. Multiple access performance in UWB systems using time hopping vs. direct sequence spreading. In Proceedings of the 2002 IEEE Wireless Communications and Networking Conference, Orlando, FL, USA, 17–21 March 2002; Volume 2, pp. 522–525.
- Guo, Z.; Letaief, K. An effective multiuser receiver for DS/CDMA systems. IEEE J. Sel. Areas Commun. 2001, 19, 1019–1028. [Google Scholar]
- De Rango, F.; Veltri, F.; Fazio, P.; Marano, S. BER regression analysis of DS-UWB based WPAN. In Proceedings of the IEEE 65th Vehicular Technology Conference, Dublin, Ireland, 22–25 April 2007; pp. 2286–2290.
- Boubaker, N.; Letaief, K.B. Performance analysis of DS-UWB multiple access under imperfect power control. IEEE Trans. Commun. 2004, 52, 1459–1463. [Google Scholar] [CrossRef]
- Verdú, S. Optimum multiuser asymptotic efficiency. IEEE Trans. Commun. 1986, 34, 890–897. [Google Scholar] [CrossRef]
- Giorgetti, A.; Varrella, M.; Chiani, M. Analysis and performance comparison of different cognitive radio algorithms. In Proceedings of the Second International Workshop on Cognitive Radio and Advanced Spectrum Management, Aalborg, Denmark, 18–20 May 2009; pp. 127–131.
- D’Errico, R.; Sibille, A.; Giorgetti, A.; Chiani, M. Antenna diversity in UWB indoor channel. In Proceedings of the IEEE International Conference on Ultra-Wideband, Hannover, Germany, 10–12 September 2008.
- Decarli, N.; Giorgetti, A.; Dardari, D.; Chiani, M.; Win, M.Z. Stop-and-go receivers for non-coherent impulse communications. IEEE Trans. Wirel. Commun. 2014, 13, 4821–4835. [Google Scholar] [CrossRef]
- Shao, H.; Beaulieu, N.C. A novel zonal UWB receiver with superior performance. IEEE Trans. Commun. 2009, 57, 1197–1206. [Google Scholar] [CrossRef]
- Verdu, S. Minimum probability of error for asynchronous Gaussian multiple-access channels. IEEE Trans. Inf. Theory 1986, 32, 85–96. [Google Scholar] [CrossRef]
- Lupas, R.; Verd, S. Near-far resistance of multiuser detectors in asynchronous channels. IEEE Trans. Commun. 1990, 38, 496–508. [Google Scholar] [CrossRef]
- Verdu, S. Computational complexity of optimum multiuser detection. Algorithmica 1989, 4, 303–312. [Google Scholar] [CrossRef]
- Alagöz, F. A new algorithm for optimum multiuser detection in synchronous CDMA systems. AEU-Int. J. Electron. Commun. 2003, 57, 263–269. [Google Scholar] [CrossRef]
- Kaligineedi, P.; Bhargava, V.K. Frequency-domain turbo equalization and multiuser detection for DS-UWB systems. IEEE Trans. Wirel. Commun. 2008, 7, 3280–3284. [Google Scholar] [CrossRef]
- Li, Q.; Kong, Z.; Fang, Y.; Yao, J.; Wang, C. Multiuser detection employing a novel Genetic algorithm for UWB communications. Proc. Eng. 2011, 15, 2505–2510. [Google Scholar]
- Zhao, N.; Wu, Z.; Zhao, Y.; Quan, T. A population declining mutated ant colony optimization multiuser detector for MC-CDMA. IEEE Commun. Lett. 2010, 14, 497–499. [Google Scholar] [CrossRef]
- Liu, H.; Li, J. A particle swarm optimization-based multiuser detection for receive-diversity-aided STBC systems. IEEE Signal Process. Lett. 2008, 15, 29–32. [Google Scholar]
- Wu, Z.; Zong, Z.; Yin, Z.; Chen, X. Joint multiuser detection of CD and AFSA in DS-UWB communication systems. Inf. Technol. J. 2011, 10, 422–427. [Google Scholar] [CrossRef]
- Hu, J.; Blum, R.S. Application of distributed signal detection to multiuser communication systems. IEEE Trans. Aerosp. Electron. Syst. 2002, 38, 1220–1229. [Google Scholar]
- Blum, R.S.; Hu, J. Distributed multiuser detection. In Proceedings of the Conference Record of the Thirty-Third Asilomar Conference on Signals, Systems, and Computers, Pacific Grove, CA, USA, 24–27 October 1999.
- Verdu, S. Multiuser Detection; Cambridge University Press: Cambridge, UK, 1998. [Google Scholar]
- Durisi, G.; Benedetto, S. Performance evaluation of TH-PPM UWB systems in the presence of multiuser interference. IEEE Commun. Lett. 2003, 7, 224–226. [Google Scholar] [CrossRef]
- Chair, Z.; Varshney, P.K. Optimal data fusion in multiple sensor detection systems. IEEE Trans. Aerosp. Electron. Syst. 1986, AES-22, 98–101. [Google Scholar] [CrossRef]
- Chen, J.G.; Ansari, N.; Sivesk, Z. Improving multiuser detection performance by data fusion. In Proceedings of the Global Telecommunications Conference, London, UK, 18–22 November 1996; Volume 3, pp. 1794–1798.
- Goebel, K.; Yan, W.; Cheetham, W. A method to calculate classifier correlation for decision fusion. In Proceedings of the Decision and Control, Las Vegas, NV, USA, December 2002; pp. 135–140.
- Abou-Rjeily, C. Performance analysis of UWB systems over the IEEE 802.15. 3a channel model. IEEE Trans. Commun. 2011, 59, 2377–2382. [Google Scholar] [CrossRef]
- Hao, K.; Gubner, J. Theoretical performance analysis of the IEEE 802.15. 3a UWB channel model. In Proceedings of the IEEE Global Telecommunications Conference, Washington, DC, USA, 26–30 November 2007; pp. 1770–1774.
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gu, Y.; Yang, M.; Shi, Z.; Wu, Z. The Applications of Decision-Level Data Fusion Techniques in the Field of Multiuser Detection for DS-UWB Systems. Sensors 2015, 15, 24771-24790. https://doi.org/10.3390/s151024771
Gu Y, Yang M, Shi Z, Wu Z. The Applications of Decision-Level Data Fusion Techniques in the Field of Multiuser Detection for DS-UWB Systems. Sensors. 2015; 15(10):24771-24790. https://doi.org/10.3390/s151024771
Chicago/Turabian StyleGu, Yebo, Minglei Yang, Zhenguo Shi, and Zhilu Wu. 2015. "The Applications of Decision-Level Data Fusion Techniques in the Field of Multiuser Detection for DS-UWB Systems" Sensors 15, no. 10: 24771-24790. https://doi.org/10.3390/s151024771





