Emergency Navigation without an Infrastructure
Abstract
: Emergency navigation systems for buildings and other built environments, such as sport arenas or shopping centres, typically rely on simple sensor networks to detect emergencies and, then, provide automatic signs to direct the evacuees. The major drawbacks of such static wireless sensor network (WSN)-based emergency navigation systems are the very limited computing capacity, which makes adaptivity very difficult, and the restricted battery power, due to the low cost of sensor nodes for unattended operation. If static wireless sensor networks and cloud-computing can be integrated, then intensive computations that are needed to determine optimal evacuation routes in the presence of time-varying hazards can be offloaded to the cloud, but the disadvantages of limited battery life-time at the client side, as well as the high likelihood of system malfunction during an emergency still remain. By making use of the powerful sensing ability of smart phones, which are increasingly ubiquitous, this paper presents a cloud-enabled indoor emergency navigation framework to direct evacuees in a coordinated fashion and to improve the reliability and resilience for both communication and localization. By combining social potential fields (SPF) and a cognitive packet network (CPN)-based algorithm, evacuees are guided to exits in dynamic loose clusters. Rather than relying on a conventional telecommunications infrastructure, we suggest an ad hoc cognitive packet network (AHCPN)-based protocol to adaptively search optimal communication routes between portable devices and the network egress nodes that provide access to cloud servers, in a manner that spares the remaining battery power of smart phones and minimizes the time latency. Experimental results through detailed simulations indicate that smart human motion and smart network management can increase the survival rate of evacuees and reduce the number of drained smart phones in an evacuation process.1. Introduction
The large amount of multi-domain sensory information generated by increasingly advanced sensor networks can aggravate the burden of emergency navigation systems, which demand a time-critical response with respect to data collection, interpretation and transmission. Traditional WSN-based emergency management systems, which consist of functionality-identical sensors, have difficulty in offering optimal evacuations in a timely manner in the presence of time-varying hazards, due to the limitation in processing capability, battery power and communication speed [1]. Although the evolution from homogeneous architectures to heterogeneous architectures with functionally-separated nodes makes WSN-based systems more energy-efficient and fault-tolerant, this structure still suffers from resource restriction problems due to cost and unattended operation during lifetime.
Owing to the high processing power, large storage, low risk level and high interoperability, cloud computing has become a dominating technology and has the potential to revolutionise the emergency management landscape. Accompanying this tendency, a new interest has been aroused to consider smart phones as simple clients for the back-end cloud due to their large-scale adoption and sensing abilities [2,3]. Compared with WSN-based counterparts, smart phone-aided, cloud-based emergency response systems are more flexible due to the elimination of both the extensive time to setup a permanent WSN and the routine maintenance, such as battery changes. Furthermore, owing to the enormous processing power, cloud computing can be beneficial in providing better quality of information (Qol) [4] and making more sophisticated decisions. Additionally, cloud-based emergency navigation systems can decrease the likelihood of being affected by the ongoing hazard and reduce energy consumption of thin clients by offloading computations to the remote cloud.
However, state-of-the-art cloud-based emergency navigation systems, which are based on the client-server model, still face many challenges. For instance, most systems adopt optimal path-finding algorithms that demand time-consuming full graph searches and information synchronization processes, especially when a large-scale environment is involved. Meanwhile, the gathering and disseminating of a large volume and a wide variety of sensory information, such as multi-media geographical data, can deplete client devices quickly. Moreover, clients in existing systems are presumed to be trusted and cooperative. Hence, misbehaving clients or incorrect reading of sensors can have a significant impact on the system performance.
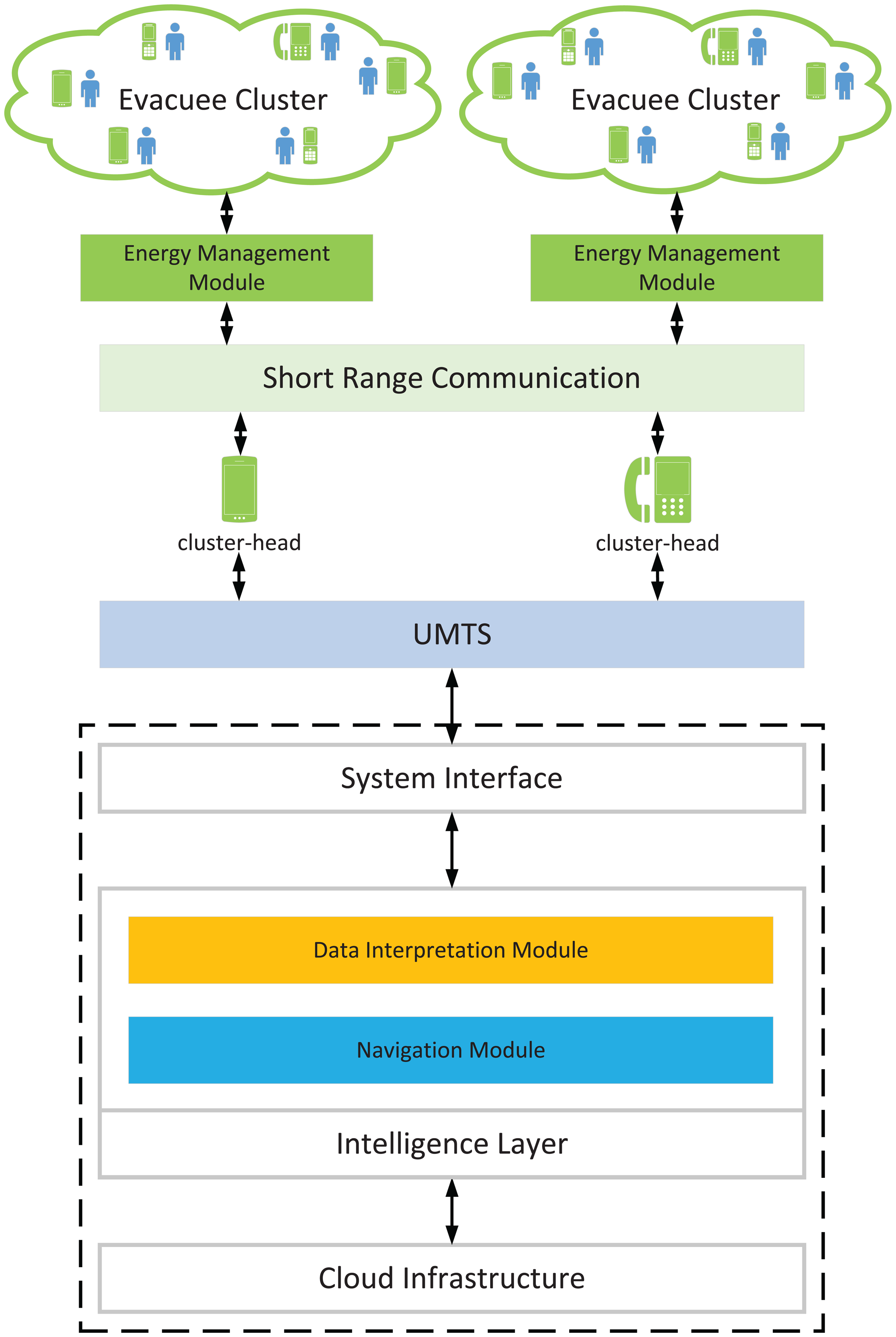
Thus, in this paper, we propose a novel cloud-based emergency navigation system that borrows the concept of a cognitive packet network (CPN) [5] and social potential fields [6] to evacuate civilians in built environments. As a software-defined network, CPN can be completely implemented in software and, therefore, is easy to deploy on cloud servers as virtual “CPN nodes” in a distributed manner. In addition, CPN can achieve fast adjustments, because each CPN node operates as a sub-system to detect the environment, and no synchronization procedure is required. In this framework, smart phones are used as clients to connect to the access point(s) of cloud servers that carry out the intensive computations. Evacuees are directed to exits with a cooperative strategy to improve the elasticity in communication and localization, as well as to increase the possibility for a civilian to obtain assistance when at risk. A power-aware QoS metric [7], which is based on the ad hoc cognitive packet network (AHCPN) protocol [8] that uses an energy-aware sensible routing technique [9], is also presented to prolong the lifetime of smart handsets. One advantage of the AHCPN protocol is that it can locate malicious users readily, as detailed path information is contained in the route-search packets. When an emergency happens, we assume that a few cloud access points can be rapidly deployed between the emergency locations and the cloud and that the evacuees themselves are only equipped with smart phones that constitute an energy-efficient ad hoc network between each other, so as to reach the access points for two-way communication.
Since mathematical models [10] cannot handle the full complexity that is encountered during an emergency and evacuation drills are high-priced and time-consuming, agent-based simulation methods [11–13] are indeed the tools of choice to study such systems. Hence, in this work, the proposed algorithms are evaluated in a simulated built environment where a fast-spreading fire breaks out.
The remainder of the paper is organized as follows: Section 2 presents the related studies of cloud-enabled emergency navigation systems and coordinated behaviour-involved algorithms in emergency evacuation. In Section 3, we recall the concept of the cognitive packet network and then describe the system architecture and related algorithms in Section 4. The simulation model and assumptions are introduced in Section 5, and results are presented in Section 6. Finally, we draw conclusions and present future work in Section 7.
2. Related Work
2.1. Cloud-Based Emergency Management Systems
Cloud computing provides a service-oriented architecture that harnesses the computing capability of massive inter-networked computers. Since the concept was explored in the 1960s, the scope of cloud computing has grown tremendously over the last few decades and has motivated considerable research in the field of emergency management. For example, [14] proposes a community-based cloud-enabled emergency management system that leverages existing social network sites (SNS) to collect and disseminate emergent information. This platform consists of a information repository layer and a social networking layer, and a semantics-based query is used to overcome heterogeneous data from diverse organizations. In [15], an intelligent transportation system (ITS) is presented with the aid of vehicular ad hoc networks (VANETs) and cloud computing. Different computational models are available in the cloud to generate the optimum strategy for diverse situations. Simulations are performed in the transportation network of a city where the Lighthill-Whitham-Richards (LWR) model is used to mimic the traffic. Results indicate that this large-scale emergency response system, which can collect and propagate information through different communication modes, overcomes the traditional analogues using media. Because of the handicaps, such as limited battery power and computing speed in the hybrid fire evacuation system (HBFES) [16], which uses mobile phones and radio frequency identification (RFID) to locate evacuees and calculate evacuation routes, in [17], this system is extended by employing an external cloud server to perform computations. Due to the limitations of common indoor positioning technologies and the unavailability of GPS, in [18], a smart phone-assisted system to locate evacuees with pedometry-based localization and image-based positioning is suggested. The cloud-based server can obtain the position of individuals by matching the image snapshots uploaded by evacuees and then provide uncrowded routes for users. However, current cloud-enabled emergency response systems with the aid of portable devices do not consider the impact of significant energy utilisation in the client side during the communication process. On the other hand, smart phones using the Universal Mobile Telecommunications System (UMTS) protocol require base stations and a substantial infrastructure, which may be destroyed or overloaded during an emergency. Furthermore, UMTS systems themselves can easily come under attack [19,20], including by various forms of denial of service attacks [21].
2.2. Coordination Algorithms for Evacuation
Much research has demonstrated that cooperative strategies have a significant positive influence on multi-agent systems, and related studies have emerged for decades as organizational paradigms in agent-based structures [22] and autonomous search by large-scale robotic systems [6,23]. However, most related research on emergency evacuation focuses on developing diverse models [24] to simulate the crowd or coordinated behaviours, such as kin behaviour [25] in emergencies.
“Social potential fields”, which were initially used for coordinating robots in a very large-scale robotic system [6], have been employed for emergency navigation in [26]. A self-organizing sensor network is established with “artificial potential fields” where artificial forces exist. Exits and dangerous zones generate attractive forces and repulsive forces, respectively, and evacuees move under the actuation of the resultant force. However, the original SPF considers the interactions between robots to avoid congestion, while the artificial potential fields in [26] does not take influences among evacuees into account.
Emergency evacuation often accompanies the malfunction of communication infrastructures or sensors, which can be caused by an on-going hazard or malicious attacks. The failure of the communication infrastructure can render a centralized system invalid, while the malfunction of sensors will affect the QoI and accuracy of localization. To solve the above problems, some coordinated behaviour-involved algorithms, such as opportunistic communications and delay tolerant networks, have been investigated to increase the resilience of emergency management systems [27–29]. For instance, [30–32] have proposed a resilient emergency support system (ESS) with the aid of opportunistic communications [33]. This system consists of sensor nodes (SNs) and communication nodes (CNs). SNs can detect the hazard in its vicinity and inform the evacuees passing by of the location, while CNs are portable devices that are taken by occupants. The civilians initially wander in the environment and can only inform the civilians about the hazard within its communication range. Each civilian calculates the shortest path to the exits with Dijkstra's algorithm. However, this work concentrates on studying the impact of “passive” cooperation among evacuees, who exchange emergent messages with other civilians, and no active mechanism is used to improve the information dissemination efficiency.
3. Cognitive Packet Network
Searching physical routes for evacuees or communication routes for emergent messages can be modelled as nonlinear combinatorial optimisation problems to search optimal paths, while minimizing desired cost functions [34]. Due to the fact that classical optimization algorithms can be easily trapped in local minima [35] and exact solutions can be computationally expensive and time consuming for NP-hard problems [36], in this paper, we use the concept of the cognitive packet network, which is a meta-heuristic inspired by natural intelligence, to emergency planning problems.
The cognitive packet network (CPN) introduced in [37–39] was originally proposed for large-scale and fast-changing packet networks and can provide QoS-driven routing to satisfy diverse end users in multimedia networks. By employing smart packets (SPs), CPN can discover optimal routes rapidly and heuristically and realise continuous self-improvement. Contrary to conventional routing protocols, in the CPN, intelligence is realised by using random neural networks (RNNs) [40–43], which is a mathematical model of natural mammalian neuronal networks and is constructed into SP search. Hence, SPs can discover optimised routes with their predefined goals and improve QoS by learning from their own investigations and experience from other packets.
CPN has been applied to many domains, including emergency navigation [44,45] and emergency resource allocation [35,46–48]. As the world's first software-defined network (SDN), it can be installed on computers seamlessly [49]. In the proposed system, the CPN-based algorithm is deployed in the back-end cloud, and each node in the CPN represents a realistic location where evacuees can identify their locations by uploading visual snapshots and querying the cloud. Each node is composed of a recurrent RNN to determine the direction of SPs and a mailbox (MB). Each neuron in the RNN represents a neighbour node, and the neighbour node associated with the highest excitation probability indicates the most beneficial forwarding direction of SPs. The notation in Table 1 is the same as that used in the original RNN model [40]. The mailbox maintains a routing list to store the paths discovered by SPs and sensory data uploaded by smartphones. Consequently, the original WSN-based CPN algorithm in [44] is virtualised in the cloud. CPN contains three types of packets: smart packets (SPs), acknowledgements (ACKs) and dumb packets (DPs). SPs gather information from the traversed nodes and search paths to destinations with respect to predefined QoS goals. They can either choose the neighbour node decided by random neural networks as the next hop or drift randomly to explore and update routes. When an SP reaches the destination, an ACK, which reserves the discovered path, and collected data will be generated and sent back to the source node through the reverse path. When an ACK reaches a node, it will update the MB and train the random neural network by performing reinforcement learning (RL), as shown in Pseudocode 1. DPs are the packets that actually carry the payloads. they always choose the top-ranked path in the routing list as the next hop. In the context of emergency evacuation, evacuees are considered as DPs.
AHCPN [8] is a variant of the original CPN and is used in the high dynamic mobile ad hoc networks (MANETs) in which the position of users varies continuously. Since CPN can allocate resources in proportion to the probability of finding an optimal route there, it can significantly replace broadcast transmissions in traditional routing protocols with unicasts. Because each smart phone can communicate with the cloud via 3G directly, hence each smart phone can be considered as a local “exit”, and SPs need to decide when to stop searching among mobile phones and transmit to the access node that connects to the remote cloud. Benefiting from their inherent intelligence, SPs can self-determine to transmit to the cloud when any of the two following conditions is fulfilled:
If all of the neighbour portable devices of the current smart handset in the near-field communication range have already been visited by checking the cognitive map of SPs.
If the predicted path availability (calculated by Formula 3) of conveying a payload from the current discovered path is larger than the estimated path availability of transmitting directly from the source smart phone.
Furthermore, emergencies caused by terrorist attacks can also be accompanied with network attacks, such as node capture or denial of sleep in the client side and denial of service in the server side [50]. CPN can naturally benefit the process of defending malicious acts, because SPs and ACKs store all of the intermediate nodes from the source to the destination. Therefore, the potential malicious nodes can be located easily. All of the nodes between a malicious origin and the target node can drop attacking traffic to avoid useless occupancy of bandwidth. Meanwhile, as CPN is a QoS-driven protocol, packets can determine the validity by QoS, and smart phones can allocate different bandwidth for flows different QoS.
| Pseudocode 1 The training process of RNN. | |
| Input: Path information brought back by an ACK | |
| Output: The excitation probability of neurons in the RNN | |
| 1: | When an ACK reaches a node, extract gathered path information from the ACK |
| 2: | Calculate the path cost G based on the collected information and the associated goal function |
| 3: | Compute the reward |
| 4: | Calculate the decision threshold Tl = aTl−1 + (1−a) Ri |
| 5: | for each neuron i in the RNN do |
| 6: | /* Compute the current total firing rate coming out of neuron i */ |
| 7: | |
| 8: | end for |
| 9: | for each neuron i in the RNN, except neuron j do |
| 10: | /* Compare the Rl with the previous threshold Tl−1 and update weights of neurons */ |
| 11: | if Rl ≥ Tl−1 then |
| 12: | |
| 13: | |
| 14: | else |
| 15: | |
| 16: | |
| 17: | end if |
| 18: | end for |
| 19: | for each neuron i in the RNN do |
| 20: | /* Compute the updated total firing rate of neuron i */ |
| 21: | |
| 22: | end for |
| 23: | for each neuron i in the RNN do |
| 24: | /* Normalize the weights of the neurons */ |
| 25: | for each linked neuron m of neuron i in the RNN do |
| 26: | |
| 27: | |
| 28: | end for |
| 29: | end for |
| 30: | for each neuron i in the RNN do |
| 31: | /* Calculate the excitation probability qi of the neuron i */ |
| 32: | |
| 33: | |
| 34: | |
| 35: | end for |
5. Simulation Model and Assumptions
We use an agent-based discrete-event simulator, namely the Distributed Building Evacuation Simulator (DBES), to evaluate the effectiveness of the novel navigation algorithm, as well as the AHCPN-based energy-efficient protocol in a fire-related emergency evacuation. The physical area is hypothesised as a graph: vertices are positions with landmarks by which evacuees can easily identify their locations by uploading snapshots and querying the server; edges are physical links by which evacuees can move inside the building. The graph can be downloaded from the cloud when a hazard occurs. The building model we employed is a large canary wharf shopping mall with relatively wide paths for evacuees to move in clusters. The shopping mall is a three-story building with two exits on the ground floor, as shown in Figure 2. Initially, evacuees are randomly scattered in the building, and they are assumed to be equipped with smart phones with random remaining battery power. When the battery power of smart phone is depleted, the evacuee will wander or follow other evacuees in the line of sight to the exits.
We assume that no related sensors are pre-installed in the built environment. Hence, hazards can only be discovered by residents in the building. When an evacuee discovers a hazard, he/she will inform the server by using the smart phone, and then, the server will alarm all of the related civilians. Civilians can locate themselves by taking image snapshots and matching them with pre-known landmarks, which are stored in cloud severs. The photos are taken by built-in cameras on the mobile phones and then uploaded to the cloud. The image-based localization algorithms [18] are performed in cloud severs. The spreading of the hazard is reported by evacuees and predicted by hazard models in the cloud.
In the simulation, the indoor Wi-Fi access points are presumed to have malfunctioned due to hazards or the outage of the power supply. Hence, the portable devices can only communicate with the cloud severs through UMTS. To maintain the 3G communication between the cloud and smart handsets, we hypothesise that during an emergency, a few cloud access points can be quickly deployed in the vicinity of the building. We also assume that smart phones provide the Bluetooth communication mode to conduct short-range communications. The size of the image taken by smart phones is set to 100 kilobytes, and the header of the AHCPN packets is 12 bytes [8]. The smart phone identification uses a IP address space which is four bytes. The initial battery power of smart phones yields a normal distribution, and the battery capacity of smart phones is set to 16,000 joules.
The energy consumption model of smart phones is based on the previous literature [54–57]. We assume that smart phones have three states: suspended state, idle states and high-power state. When in a suspended state, the application processor of smart handsets is idle and the communications processor performs a low level of activity [54]. When in an idle case, the smart phone is fully awake, but no application is active. Finally, the high-power case is the state when the portable device interacts with the cloud. The power utilisation of different states with regard to the elapsed time can be seen in Table 3, which is based on the average system power of specific smart phones for a selection of benchmarks in [55].
The energy utilization of different communication modes with respect to the amount of transferred data, as well as the associated transmission rate are shown in Table 4. This model is based on the energy consumption ratios presented in [57] and the measurement study of energy consumption over 3G and Wi-Fi in [56].
6. Results and Discussion
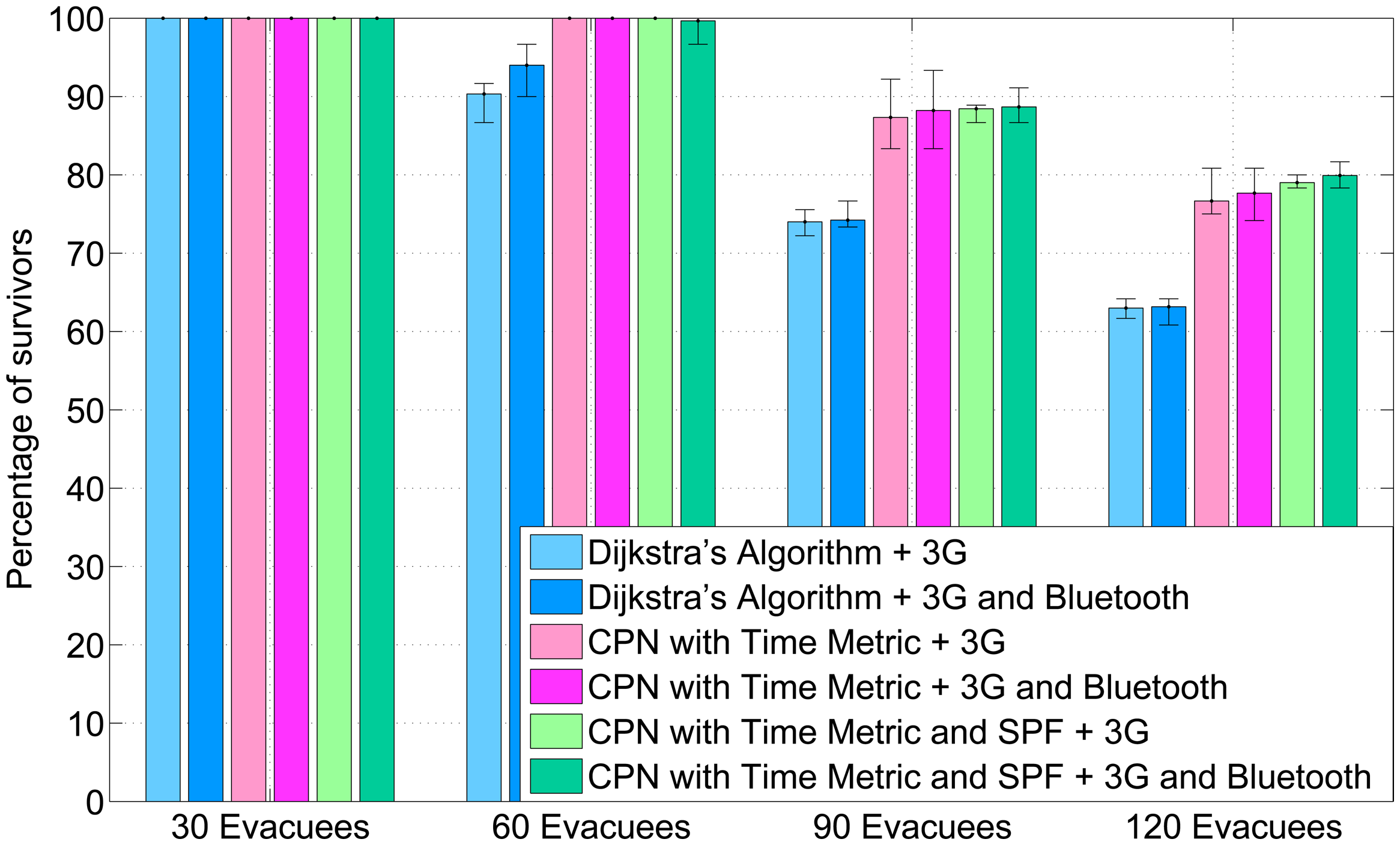
To evaluate the navigation algorithm that combines CPN and SPF (CPN&SPF) as well as the AHCPN-based energy-efficient protocol, we design an experiment that involves four scenarios with 30, 60, 90, 120 evacuees, respectively. Dijkstra's shortest path algorithm and CPN-based algorithm with a time metric (CPNST) [45] are performed for comparison purpose. Evacuees can communicate with the cloud through UMTS directly or use Bluetooth to relay data to other smart phones with a higher percentage of remaining energy and then transmitting to cloud severs through 3G.
The percentage of survivors of five randomised experiments is shown in Figure 3. Owing to the benefit of wide paths in the shopping mall, all civilians are able to evacuate at a low occupancy rate (30 evacuees). However, in relatively high population densities, both CPNST and CPN&SPF result in more survivors than Dijkstra's shortest path algorithm. This is due to the congestion-ease mechanism in CPNST. Meanwhile, SPF can also ease congestion, because it can generate large repulsive forces for the evacuees in proximity. In comparison with CPNST, CPN&SPF performs slightly better in densely-populated scenarios (90 and 120 evacuees). This is because CPN&SPF organises evacuees as loose clusters and, therefore, increases the likelihood for an evacuee to upload data through other smart phones with more remaining battery power. As a result, the probability of being trapped due to the depletion of the smart phone is decreased. Furthermore, the coordinated behaviour increases the probability of an evacuee with a depleted smart phone to follow other evacuees rather than wandering in the building. This can be confirmed by the fact that the outcome of experiments using the AHCPN energy-efficient protocol is better than for the counterparts that use UMTS directly. The AHCPN protocol can reduce the likelihood of depleting a smart phone and, therefore, decreases the possibility of an evacuee being trapped in the built environment. The results we present are numerical in nature, while it would be interesting also to discuss detailed simulations in a virtual reality environment [58].
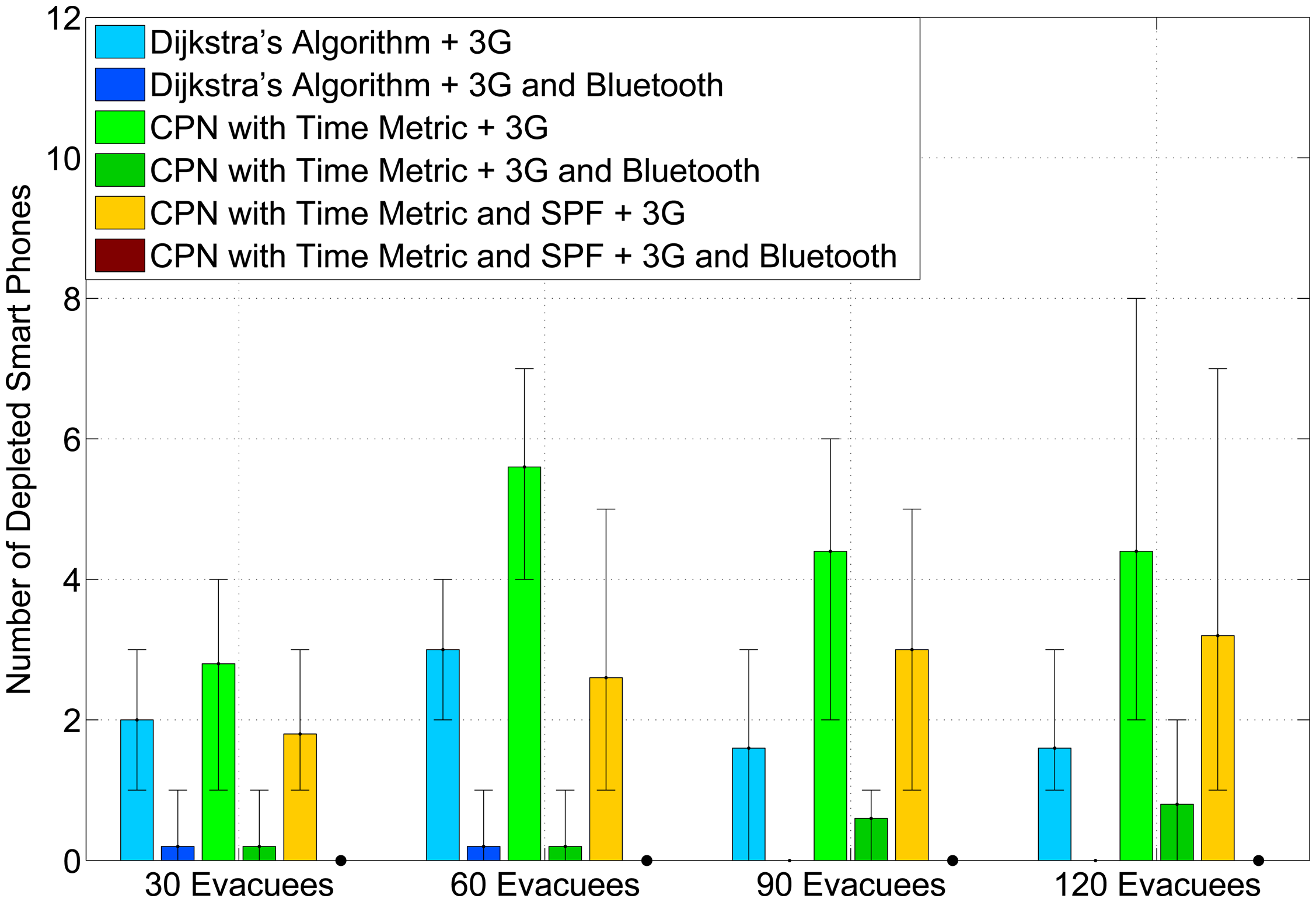
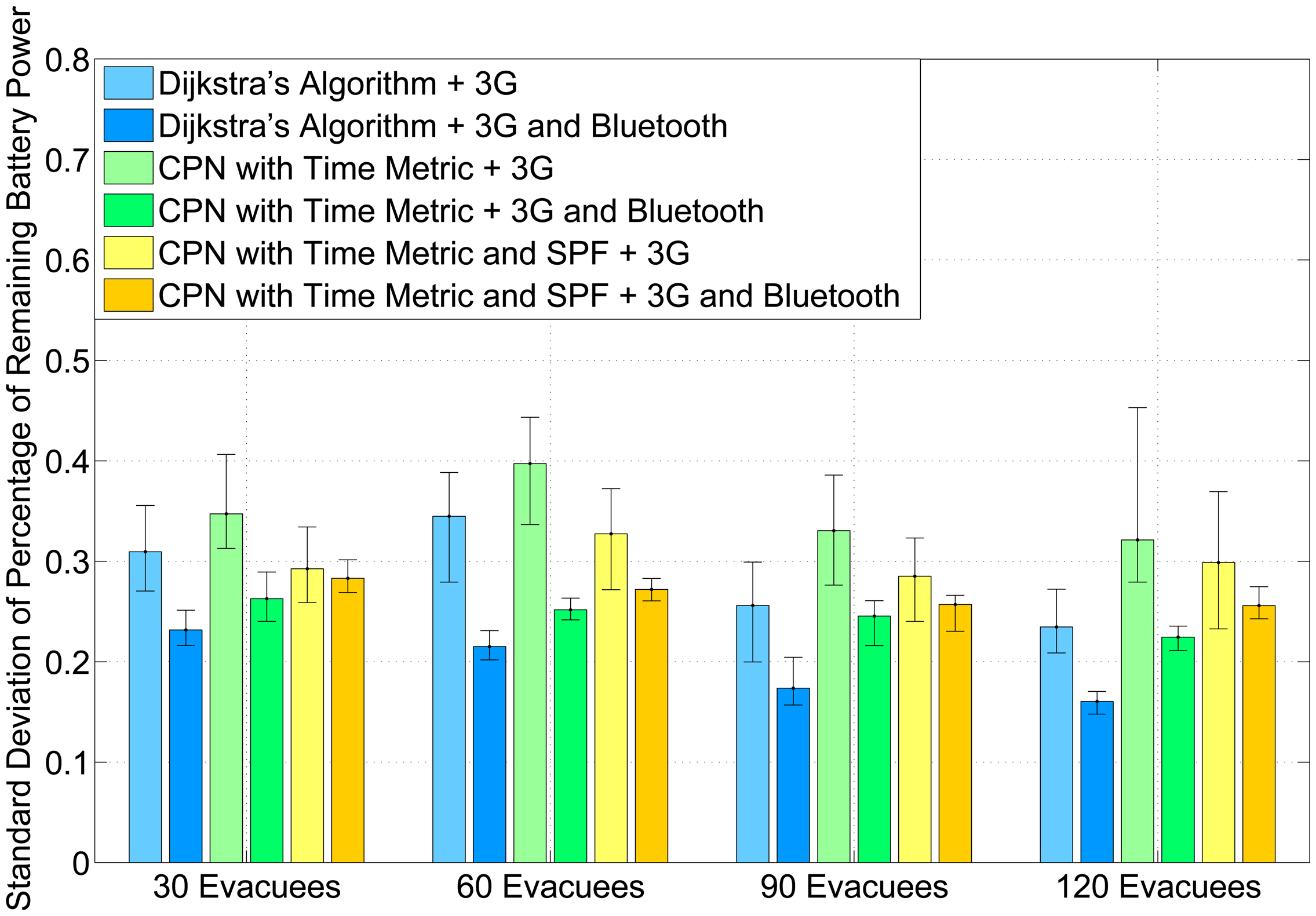
Figure 4 presents the average number of drained smart phones in the experiments. When using 3G mode to communicate with the cloud, Dijkstra's algorithm achieves the least number of drained smart phones, especially at a high occupancy rate. This is because both the CPNST and CPN&SPF and do not follow the shortest path. Hence, evacuees will traverse more landmarks and upload more photos to the cloud. However, by employing the AHCPN protocol, the number of depleted smart phones decreases significantly for all three algorithms. Moreover, there is no drained smart phone when combining the CPN&SPF algorithm with the AHCPN protocol. This confirms that routing evacuees in loose groups can contribute to the power-balancing of smart phones.
Figure 5 shows the standard deviation of the remaining percentage of battery power for smart handsets. The remaining percentage of battery power Pr in a smart handset is defined as follows:
7. Conclusions and Future Work
In this paper, we propose an infrastructure-less, indoor emergency response system to evacuate civilians with the aid of smart handsets and cloud servers. A coordinated emergency navigation algorithm is proposed to guide evacuees in loose groups. The experimental results prove that the algorithm can increase the survival rate by reducing the number of drained smart phones in an evacuation process and raising the likelihood for an evacuee with a depleted mobile device to encounter other evacuees in the line of sight and follow them to egresses. Due to the considerable energy consumption between the cloud and smart phones during the communication processes, an AHCPN-based energy-efficient protocol is also presented to prolong the lifetime of smart handsets. Simulations indicate that the protocol can significantly decrease the number of drained smart phones in an evacuation process and balance the remaining battery power among portable devices. Future research will be directed to improve the flexibility of the system by leveraging the mobile agent technology, because current cloud-based emergency response systems that are based on the client-sever paradigm demand pre-installed services in participating devices [59]. Moreover, since mobile agents can migrate seamlessly through multiple clouds and different portable devices, a mobile agent-based emergency response system has the potential to reduce communication costs and ease network congestion in large-scale emergency evacuations by dynamically optimising the locations of mobile agents. We also think that cloud-based techniques can benefit systematic and repetitive issues, such as the clearance of improvised explosive devices (IOD) and land mines [60].
Conflicts of Interest
The authors declare no conflict of interest.
Author Contributions
Erol Gelenbe invented the RNN model, its learning algorithm, the CPN routing algorithm, and developed the AHCPN algorithm for energy savings in ad-hoc networks; he designed the distributed agent based simulation environment that is used here for emergency management. Huibo Bi used these methods to develop the specific emergency evacuation algorithm described in this paper, and ran the simulation experiments. Huibo Bi drafted the paper, and Erol Gelenbe edited and corrected the paper.
References
- Gelenbe, E. A diffusion model for packet travel time in a random multi-hop medium. ACM Trans. Sensor Netw. 2007. [Google Scholar] [CrossRef]
- Gelenbe, E.; Wu, F.J. Large scale simulation for human evacuation and rescue. Comput. Math. Appl. 2012, 64, 3869–3880. [Google Scholar]
- Gelenbe, E.; Wu, F.J. Future research on cyber-physical emergency management systems. Future Internet 2013, 5, 336–354. [Google Scholar]
- Gelenbe, E.; Hey, L. Quality of information: An empirical approach. Proceedings of the 5th IEEE International Conference on Mobile Ad Hoc and Sensor Systems, Atlanta, GA, USA, 29 September-2 October 2008; pp. 730–735.
- Gelenbe, E.; Xu, Z.; Seref, E. Cognitive packet networks. Proceedings of the 11th IEEE International Conference on Tools with Artificial Intelligence, Chicago, IL, USA, 8–10 November 1999; pp. 47–54.
- Gelenbe, E.; Schmajuk, N.; Staddon, J.; Reif, J. Autonomous search by robots and animals: A survey. Robot. Auton. Syst. 1997, 22, 23–34. [Google Scholar]
- Gelenbe, E.; Morfopoulou, C. A Framework for Energy-Aware Routing in Packet Networks. Comput. J. 2011, 54, 850–859. [Google Scholar]
- Gelenbe, E.; Lent, R. Power-aware ad hoc cognitive packet networks. Ad Hoc Netw. 2004, 2, 205–216. [Google Scholar]
- Gelenbe, E. Sensible decisions based on QoS. Comput. Manag. Sci. 2003, 1, 1–14. [Google Scholar]
- Gelenbe, E. Probabilistic Models of Computer Systems. Acta Inform. 1979, 12, 285–303. [Google Scholar]
- Gelenbe, E.; Hussain, K.; Kaptan, V. Simulating autonomous agents in augmented reality. J. Syst. Softw. 2005, 74, 255–268. [Google Scholar]
- Filippoupolitis, A.; Gelenbe, E. A distributed decision support system for building evacuation. Proceedings of the 2nd Conference on Human System Interactions, Catania, Italy, 21–23 May 2009; pp. 323–330.
- Dimakis, N.; Filippoupolitis, A.; Gelenbe, E. Distributed Building Evacuation Simulator for Smart Emergency Management. Comput. J. 2010, 53, 1384–1400. [Google Scholar]
- Li, J.; Li, Q.; Khan, S.U.; Ghani, N. Community-based cloud for emergency management. Proceedings of the 2011 6th International Conference on System of Systems Engineering, Albuquerque, NM, USA, 27–30 June 2011; pp. 55–60.
- Alazawi, Z.; Altowaijri, S.; Mehmood, R.; Abdljabar, M.B. Intelligent disaster management system based on cloud-enabled vehicular networks. Proceedings of the 2011 11th International Conference on ITS Telecommunications, St. Petersburg, Russia, 23–25 August 2011; pp. 361–368.
- Chu, L. A RFID-Based Hybrid Building Fire Evacuation System on Mobile Phone. Proceedings of the 2010 Sixth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Darmstadt, Germany, 15–17 October 2010; pp. 155–158.
- Chu, L.; Wu, S.J. A real-time decision support with cloud computing based fire evacuation system. Proceedings of the 2011 15th North-East Asia Symposium on Nano, Information Technology and Reliability, Macao, China, 24–26 October 2011; pp. 45–48.
- Ahn, J.; Han, R. RescueMe: An Indoor Mobile Augmented-Reality Evacuation System by Personalized Pedometry. Proceedings of the 2011 IEEE Asia-Pacific Services Computing Conference, Jeju, Korea, 12–15 December 2011; pp. 70–77.
- Gelenbe, E.; Görbil, G.; Tzovaras, D.; Liebergeld, S.; Garcia, D.; Baltatu, M.; Lyberopoulos, G.L. NEMESYS: Enhanced Network Security for Seamless Service Provisioning in the Smart Mobile Ecosystem. Lect. Notes Electr. Eng. 2013, 264, 369–378. [Google Scholar]
- Gelenbe, E.; Gorbil, G.; Tzovaras, D.; Liebergeld, S.; Garcia, D.; Baltatu, M.; Lyberopoulos, G. Security for Smart Mobile Networks: The NEMESYS Approach. Proceedings of the 2013 IEEE Global High Tech Congress on Electronics, Shenzhen, China, 17–19 November 2013.
- Abdelrahman, O.H.; Gelenbe, E. Signalling Storms in 3G Mobile Networks. Proceedings of the IEEE International Conference on Communications, Sydney, Australia, 10–14 June 2014.
- Horling, B.; Lesser, V. A survey of multi-agent organizational paradigms. Knowl. Eng. Rev. 2004, 19, 281–316. [Google Scholar]
- Cao, Y.; Gelenbe, E. Autonomous search for mines. Eur. J. Oper. Res. 1998, 108, 319–333. [Google Scholar]
- Zheng, X.; Zhong, T.; Liu, M. Modeling crowd evacuation of a building based on seven methodological approaches. Build. Environ. 2009, 44, 437–445. [Google Scholar]
- Yang, L.; Zhao, D.; Li, J.; Fang, T. Simulation of the kin behavior in building occupant evacuation based on cellular automaton. Build. Environ. 2005, 40, 411–415. [Google Scholar]
- Li, Q.; De Rosa, M.; Rus, D. Distributed algorithms for guiding navigation across a sensor network. Proceedings of the 9th Annual International Conference on Mobile computing and networking, San Diego, CA, USA, 14–19 September 2003; pp. 313–325.
- Vahdat, A.; Becker, D. Epidemic Routing for Partially Connected ad hoc Networks; Technical Report CS-200006; Duke University: Durham, NC, USA, 2000. [Google Scholar]
- Jiang, P.; Bigham, J.; Bodanese, E. Adaptive service provisioning for emergency communications with DTN. Proceedings of the 2011 IEEE Wireless Communications and Networking Conference, Cancun, Mexico, 28–31 March 2011; pp. 2125–2130.
- Bruno, R.; Conti, M.; Passarella, A. Opportunistic networking overlays for ICT services in crisis management. Proceedings of International Conference on Information Systems for Crisis Response and Management, Seattle, WA, USA, 2–5 May 2008.
- Gelenbe, E.; Gorbil, G. Wireless networks in emergency management. Proceedings of the first ACM international workshop on Practical issues and applications in next generation wireless networks, Istanbul, Turkey, 22–26 August 2012; pp. 1–6.
- Gorbil, G.; Gelenbe, E. Opportunistic communications for emergency support systems. Proced. Comput. Sci. 2011, 5, 39–47. [Google Scholar]
- Gorbil, G.; Gelenbe, E. Resilient emergency evacuation using opportunistic communications. In Computer and Information Sciences III; Springer: London, UK, 2013; pp. 249–257. [Google Scholar]
- Pelusi, L.; Passarella, A.; Conti, M. Opportunistic networking: Data forwarding in disconnected mobile ad hoc networks. IEEE Commun. Mag. 2006, 44, 134–141. [Google Scholar]
- Pentico, D.W. Assignment problems: A golden anniversary survey. Eur. J. Oper. Res. 2007, 176, 774–793. [Google Scholar]
- Gelenbe, E.; Timotheou, S.; Nicholson, D. Random neural network for emergency management. Proceedings of the Workshop on Grand Challenges in Modeling, Simulation and Analysis for Homeland Security, Arlington, MA, USA, 17–18 March 2010.
- Ahuja, R.K.; Kumar, A.; Jha, K.C.; Orlin, J.B. Exact and heuristic algorithms for the weapon-target assignment problem. Oper. Res. 2007, 55, 1136–1146. [Google Scholar]
- Gelenbe, E.; Lent, R.; Xu, Z. Towards networks with cognitive packets. In Performance and QoS of Next Generation Networking; Springer: London, UK, 2001; pp. 3–17. [Google Scholar]
- Gelenbe, E.; Lent, R.; Nunez, A. Self-aware networks and QoS. Proc. IEEE 2004, 92, 1478–1489. [Google Scholar]
- Gelenbe, E. Steps toward self-aware networks. Commun. ACM 2009, 52, 66–75. [Google Scholar]
- Gelenbe, E. Stability of the random neural network model. Neural comput. 1990, 2, 239–247. [Google Scholar]
- Gelenbe, E.; Timotheou, S. Random neural networks with synchronized interactions. Neural Comput. 2008, 20, 2308–2324. [Google Scholar]
- Gelenbe, E.; Seref, E.; Xu, Z. Simulation with learning agents. Proc. IEEE 2001, 89, 148–157. [Google Scholar]
- Gelenbe, E. Natural Computation. Comput. J. 2012, 55, 848–851. [Google Scholar]
- Bi, H.; Desmet, A.; Gelenbe, E. Routing Emergency Evacuees with Cognitive Packet Networks. Proceedings of the 28th International Symposium on Computer and Information Sciences, Paris, France, 28–29 October 2013.
- Bi, H.; Gelenbe, E. Routing Diverse Evacuees with Cognitive Packets. Proceedings of the 4th International Workshop on Pervasive Networks for Emergency Management, Budapest, Hungary, 24–28 March 2014; pp. 1–6.
- Gelenbe, E.; Timotheou, S.; Nicholson, D. Fast distributed near-optimum assignment of assets to tasks. Comput. J. 2010, 53, 1360–1369. [Google Scholar]
- Gelenbe, E.; Timotheou, S.; Nicholson, D. A random neural network approach to an assets to tasks assignment problem. Proc. SPIE 2010. [Google Scholar] [CrossRef]
- Gelenbe, E.; Han, Q. Near-Optimal Emergency Evacuation with Rescuer Allocation. Proceedings of the 4th International Workshop on Pervasive Networks for Emergency Management, Budapest, Hungary, 24–28 March 2014; pp. 314–319.
- Gelenbe, E. A Software Defined Self-Aware Network: The Cognitive Packet Network. Proceedings of the 2014 IEEE 3rd Symposium on Network Cloud Computing and Applications, Rome, Italy, 5–7 February 2014; pp. 9–14.
- Gorbil, G.; Gelenbe, E. Resilience and security of opportunistic communications for emergency evacuation. Proceedings of the 7th ACM workshop on Performance monitoring and measurement of heterogeneous wireless and wired networks, Paphos, AA, Cyprus, 21–25 October 2012; pp. 115–124.
- Reif, J.H.; Wang, H. Social potential fields: A distributed behavioral control for autonomous robots. Robot. Auton. Syst. 1999, 27, 171–194. [Google Scholar]
- Shearer, F. Power Management in Mobile Devices, 1st ed; Newnes: Newton, MA, USA, 2011. [Google Scholar]
- Perrucci, G.P.; Fitzek, F.H.; Widmer, J. Survey on energy consumption entities on the smartphone platform. Proceedings of the 2011 IEEE 73rd Vehicular Technology Conference, Yokohama, Japan, 15–18 May 2011; pp. 1–6.
- Carroll, A.; Heiser, G. An analysis of power consumption in a smartphone. Proceedings of the 2010 USENIX conference on USENIX annual technical conference, Boston, MA, USA, 22–25 June 2010; pp. 21–21.
- Haas, C.; Wilke, J.; Stöhr, V. Realistic simulation of energy consumption in wireless sensor networks. In Wireless Sensor Networks; Springer: Berlin, Germany, 2012; pp. 82–97. [Google Scholar]
- Balasubramanian, N.; Balasubramanian, A.; Venkataramani, A. Energy consumption in mobile phones: a measurement study and implications for network applications. Proceedings of the 9th ACM SIGCOMM conference on Internet measurement conference, New York, NY, USA, 4–6 November 2009; pp. 280–293.
- Kalic, G.; Bojic, I.; Kusek, M. Energy consumption in android phones when using wireless communication technologies. Proceedings of the 35th International Convention MIPRO, Opatija, Croatia, 21–25 May 2012; pp. 754–759.
- Gelenbe, E.; Hussain, K.; Kaptan, V. Autonomous search for mines. J. Syst. Softw. 2005, 74, 255–268. [Google Scholar]
- Aversa, R.; Di Martino, B.; Rak, M.; Venticinque, S. Cloud agency: A mobile agent based cloud system. Proceedings of the 2010 International Conference on Complex, Intelligent and Software Intensive Systems, Krakow, Poland, 15–18 February 2010; pp. 132–137.
- Gelenbe, E.; Kocak, T. Area based results for mine detection. IEEE Trans. Geosci. Remote Sens. 2000, 38, 12–24. [Google Scholar]
| Notation | Definition |
|---|---|
| a | A constant between 0 and 1, typically close to 1 |
| n | The number of neurons in a RNN |
| j | The neuron which is associated with the neighbour node that corresponds to the returned ACK |
| k | The other neurons in the RNN except the neuron j |
| w+(i,j) | Rate at which neuron i emits excitation spikes to neuron j when i is excited |
| w−(i,j) | Rate at which neuron i emits inhibition spikes to neuron j when i is excited |
| Λi | Rate at which external excitation spikes arrive at neuron i |
| λi | Rate at which external inhibition spikes arrive at neuron i |
| λ+(i) | Rate at which neuron i receives excitatory spikes |
| λ−(i) | Rate at which neuron i receives inhibitory spikes |
| qi | The excitation probability of neuron i |
| Rl | l-th reward determined by a goal function |
| Tl | l-th decision threshold that keeps track of the historical value of rewards |
| Notation | Definition |
|---|---|
| RNNnew | A Boolean value to indicate if a RNN is newly constructed or reset |
| R | A random generated value between 0 and 1 |
| Nm | The total number of SPs that can be emitted before sending a photo |
| Nc | The number of SPs that has been emitted in a cycle |
| Hm | The maximum number of hops a SP can traverse before being dropped |
| Hc | Current traversed number of hops |
| VDrift | Probability to choose the neighbour associated with the most excited neuron as the next hop |
| VSPN | Probability to choose the SPN-based algorithm |
| Path availability (calculated by Formula 3) of transmitting a snapshot via the current route | |
| Path availability of conveying a snapshot via 3G mode |
| States | Energy Model |
|---|---|
| Suspended | 0.3394x |
| Idle | 0.1049x |
| High power | 0.1049x + y |
| Communication Mode | Download | Upload | Signal Rate |
|---|---|---|---|
| 3G | 0.001224x | 0.0003375x | 2 Mb/s |
| Bluetooth | 0.0001377x | 0.00012012x | 1 Mb/s |
| Wi-Fi | 0.0003057x | 0.0001586x | 54 Mb/s |
| ZigBee | 0.0002861x | 0.0003164x | 250 Kb/s |
© 2014 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license ( http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Gelenbe, E.; Bi, H. Emergency Navigation without an Infrastructure. Sensors 2014, 14, 15142-15162. https://doi.org/10.3390/s140815142
Gelenbe E, Bi H. Emergency Navigation without an Infrastructure. Sensors. 2014; 14(8):15142-15162. https://doi.org/10.3390/s140815142
Chicago/Turabian StyleGelenbe, Erol, and Huibo Bi. 2014. "Emergency Navigation without an Infrastructure" Sensors 14, no. 8: 15142-15162. https://doi.org/10.3390/s140815142




