NEURON: Enabling Autonomicity in Wireless Sensor Networks
Abstract
:1. Introduction
2. Background—Related Work
2.1. Autonomic Characteristics and IP Integration
- Self-configuration: change configuration parameters (e.g., data acquisition rate) according to the conditions in the sensor environment,
- Self-optimisation: fine-tune each sensor entity in order to achieve pre-determined goals, while low energy consumption and optimal quality of service have to be guaranteed based on corrective actions,
- Self-healing: detect system malfunctions or failures and start corrective actions based on defined policies and cooperation among neighbouring nodes to recover the network or a node,
- Self-protection: recognize possible sources of problems or threats in the sensor network and take proactive measures,
- Self-awareness: sense network changes in the sensor environment and be aware of the capabilities and the status of your neighbours.
2.2. Clustering and Routing Algorithms for WSNs
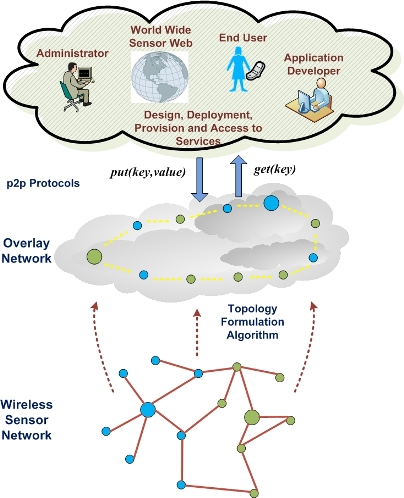
2.3. Overlay Networking in WSNs and DHTs
3. Proposed Protocol
- Support autonomic functionalities in a WSN: sensors deployed in the sensor field, establish independently communication with their neighbours, become part of the WSN and gain access to the provided data and services without human intervention.
- Self-organize the nodes into clusters: clusters are self-formulated according to the current conditions in the network, while cluster heads rotation extends the network lifetime.
- Achieve fault tolerance and avoid dependence from specific purpose nodes: clusters are formulated automatically in case of failures, since each node may be elected as CH.
- Reduce energy consumption through hierarchical routing based on an overlay among the CHs: information about the current CHs is disseminated among the WSN and routing is provided through them.
- Achieve scalability by taking advantage of autonomicity, decentralization and probabilistic techniques: there is no performance degradation as the size of the sensor network increases.
3.1. Autonomic Estimation Algorithm
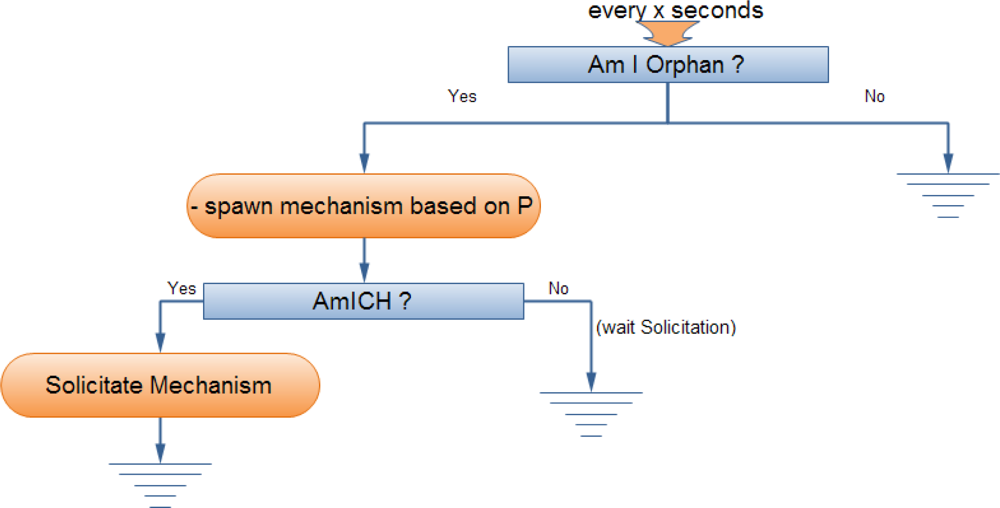
3.2. Cluster Formulation, Maintenance and Update
Cluster Formulation, Maintenance and Update Mechanisms
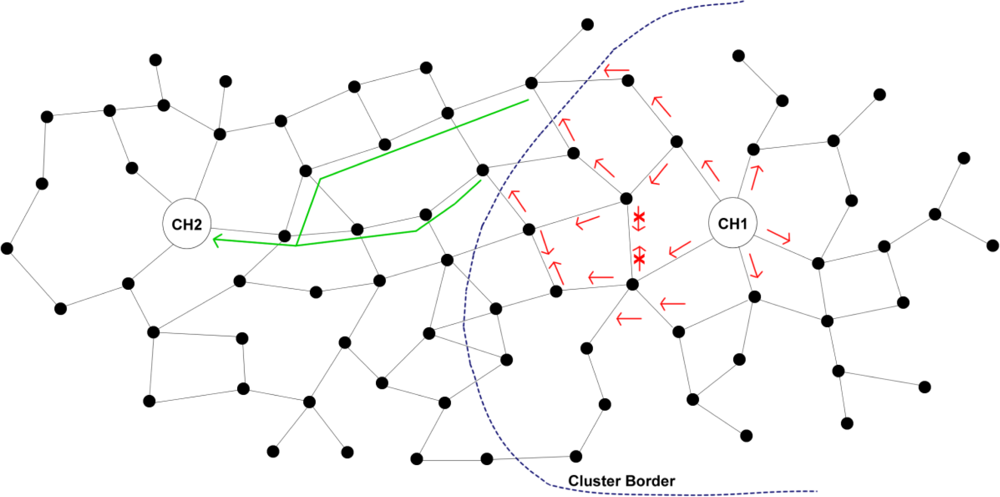
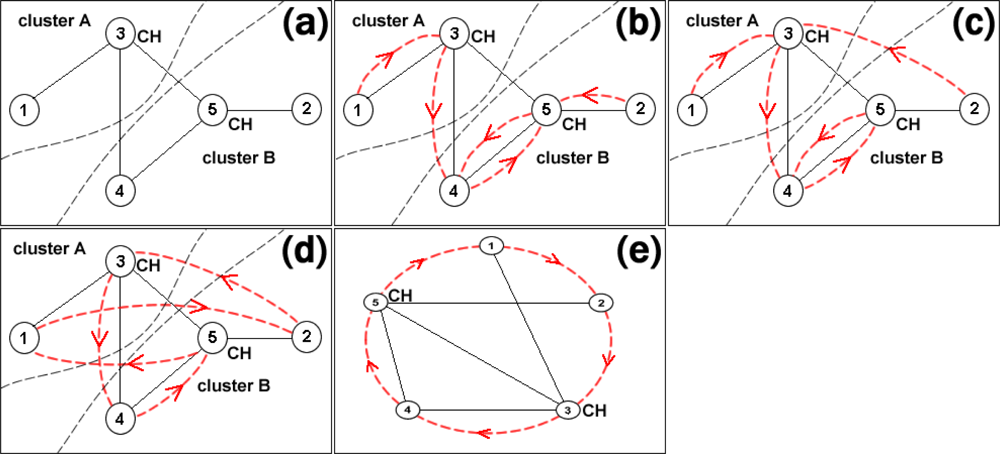
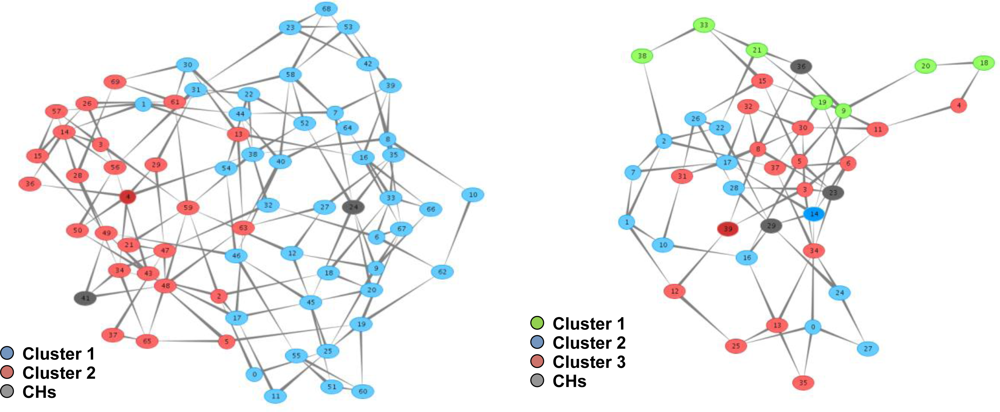
- Cluster Formulation & Maintenance: Upon the receipt of a MSolicitateCH message by a node not registered to a CH, a MRegisterNode2CH response message is send to the CH. The latter updates its routing cache and then the node automatically becomes a member of the broadcasted cluster. If the node belongs to the cluster controlled by the CH generating the message, the node forwards it to its neighbours. In addition, it stores the message to a local cache in order to avoid serving the same message again. Otherwise, if the node does not belong to the cluster controlled by the CH generating the message, the node belongs to the borderline between two clusters, as shown in Figure 1. In this case, the node does not forward the message to its neighbour but instead forwards it directly to its CH. This process is very critical as it prevents the unnecessary flooding out of the scope of a cluster and allows CHs to be aware of their neighbouring CHs. The routing information, collected to the CHs’ caches during the clusters formulation, facilitates the hierarchical routing mechanism, as discussed in Section 2.3. The cluster formulation and maintenance process is also shown in Figure 2.
- Routing Cache Maintenance: Each MSolicitateCH message—broadcasted by a CH and flooded within the cluster—contains a list of the MAC addresses of the nodes that have already forwarded it since each node that serves this message appends its MAC to this list (only once due to cycle preventive mechanism). This information allows cluster nodes to learn (or update) the shortest path towards their CH and store this information in their local routing cache.
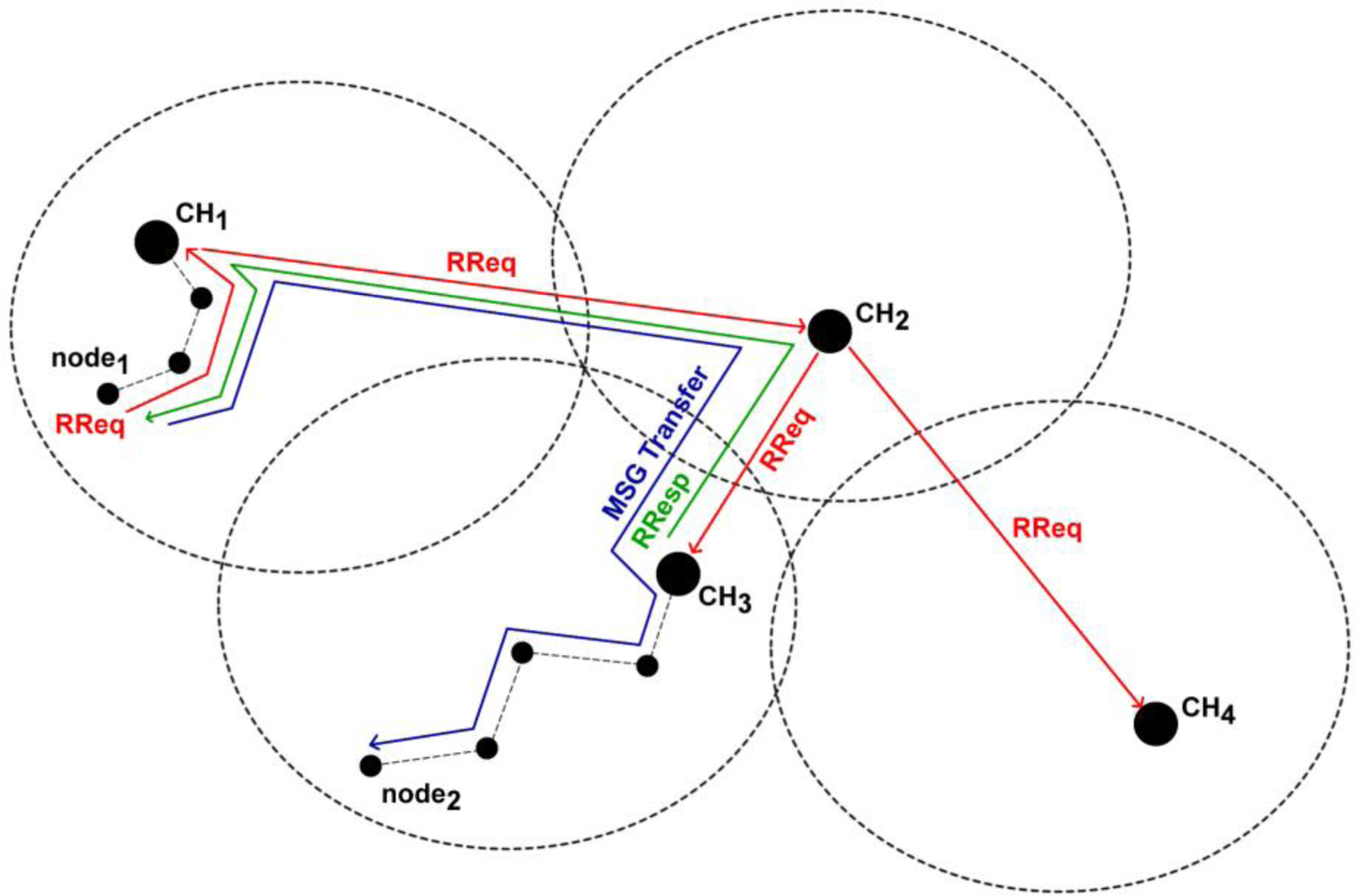
- Cluster Formulation Update: The MSolicitateCH message allows nodes to be dynamically distributed among the existing clusters according to the CHs KPIs. In case that a node receives a MSolicitateCH message from a neighbouring CH, it compares the received KPI with the KPI of its current CH. When this comparison overcomes a specified threshold, the node unregisters from its current CH and registers to the new CH. These tasks are accomplished with the usage of a MRegisterNode2CH and MUnRegisterNodefromCH message, accordingly. This approach allows CHs to extend their lifetime since the load is re-distributed among the more powerful CHs.
3.3. Hierarchical Routing
3.4. Requirements from Sensor Node Platforms
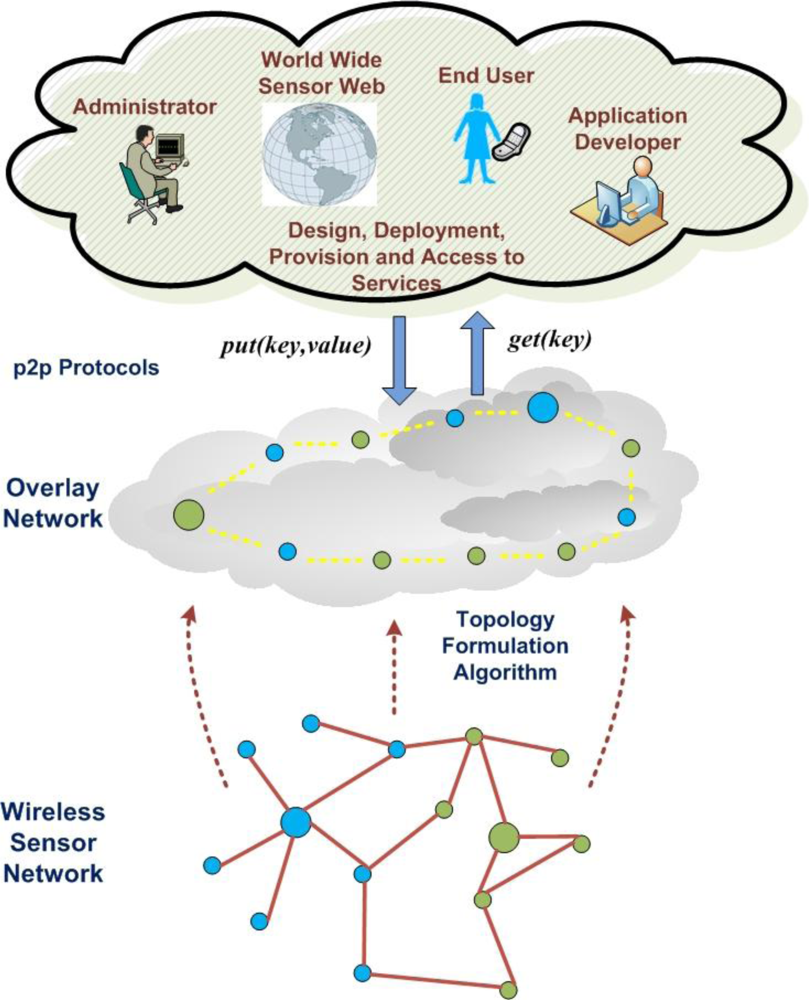
4. Service Provisioning Over NEURON
5. Experimental Evaluation
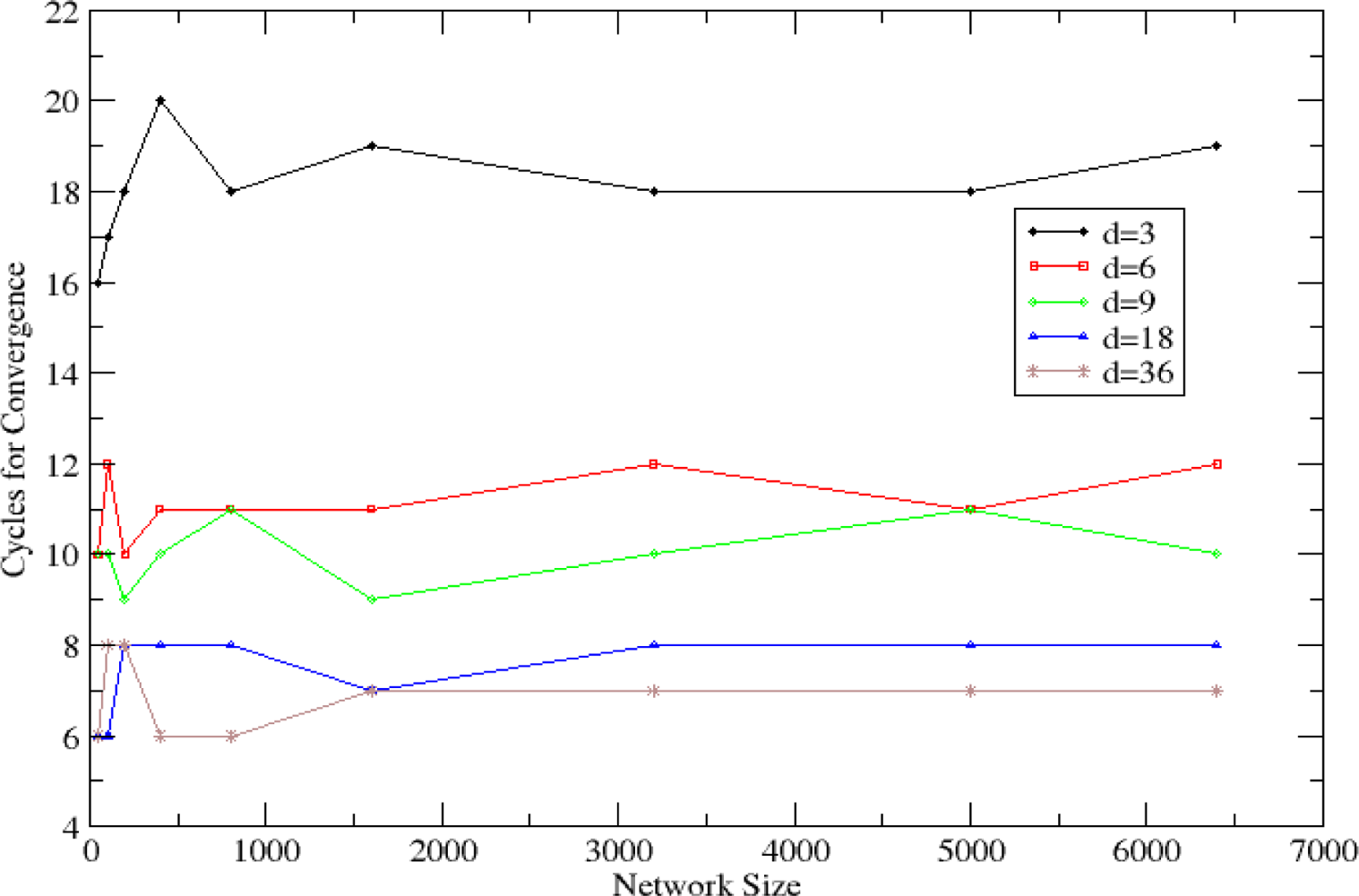
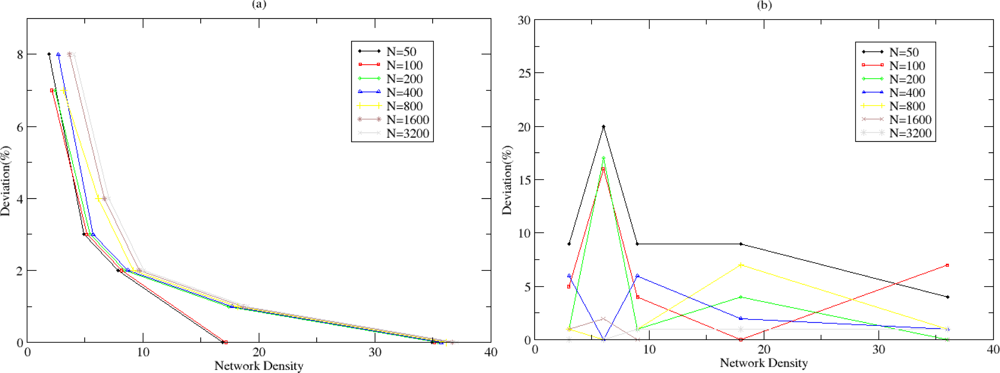
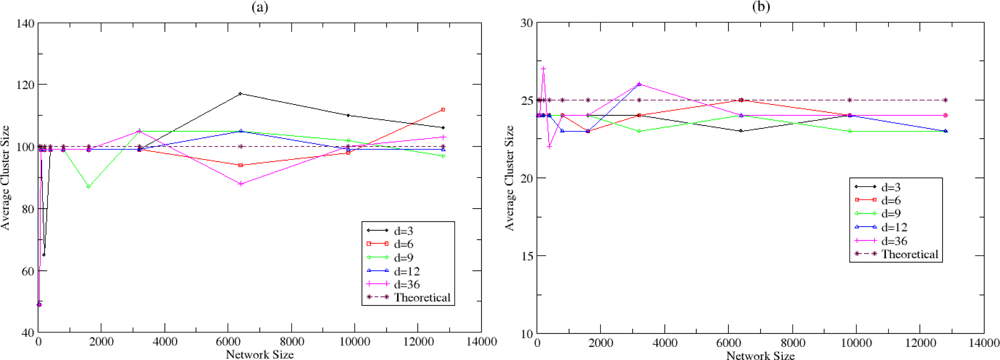
5.1. Evaluation of the Autonomic Estimation Algorithm
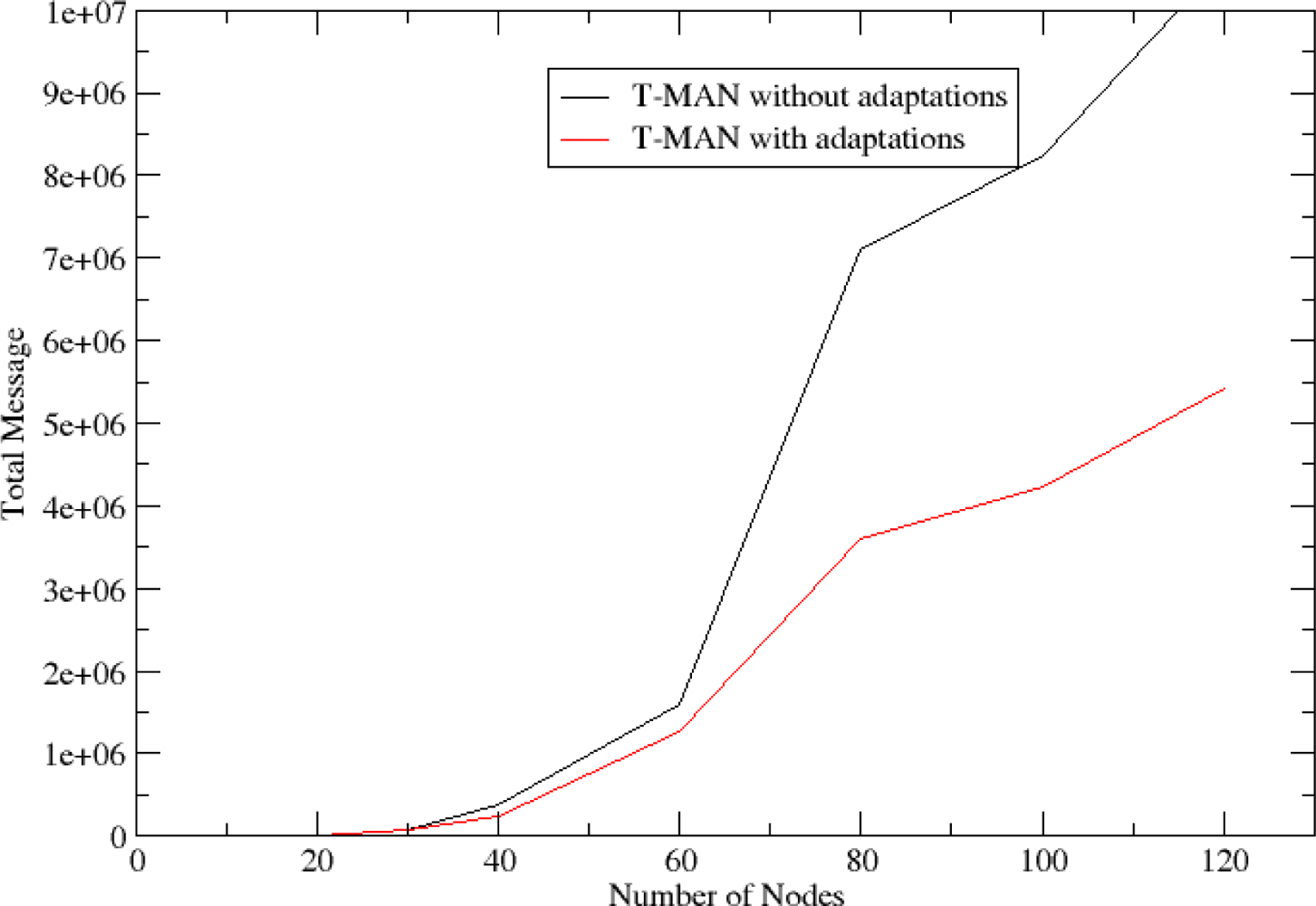
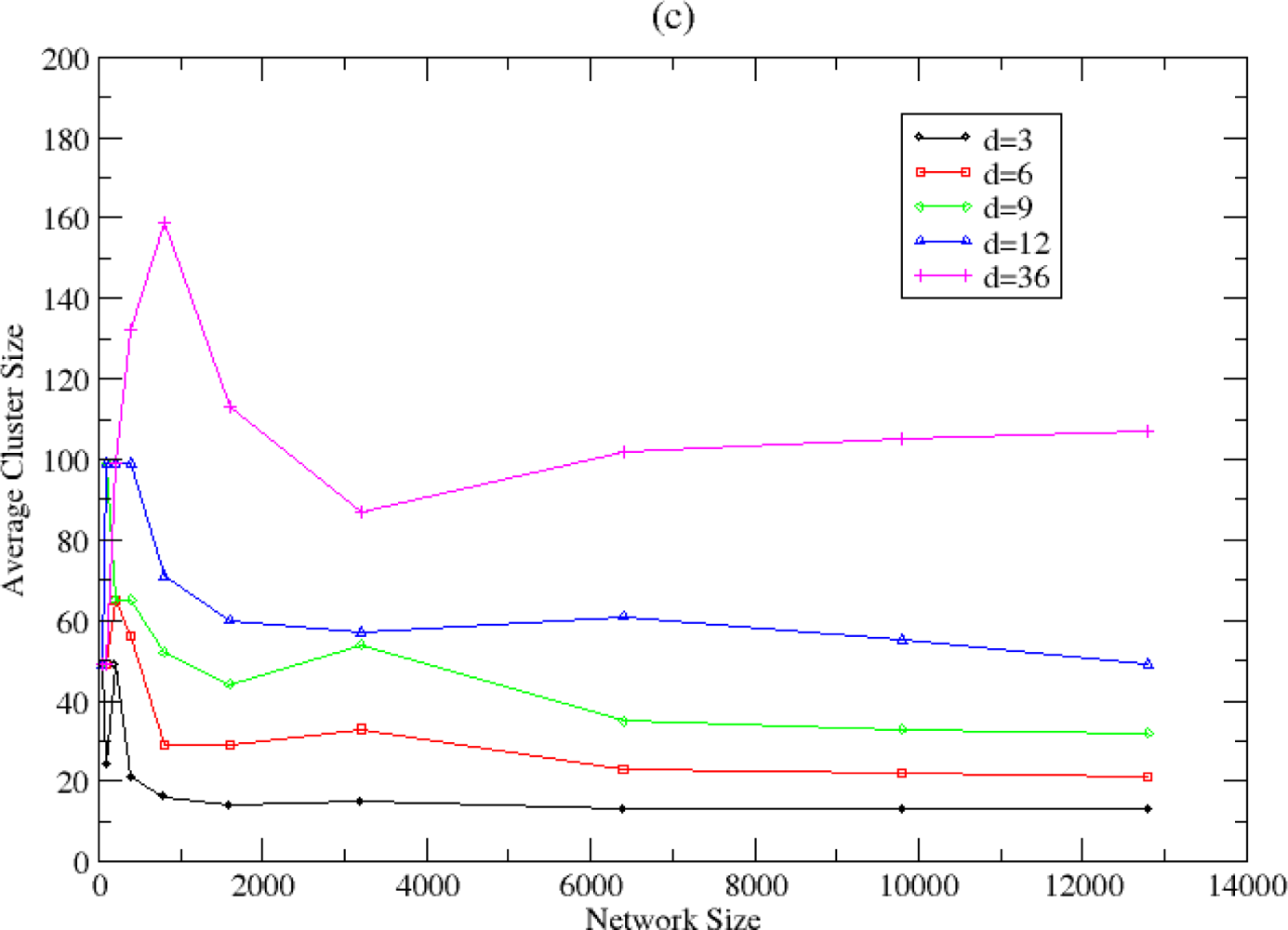
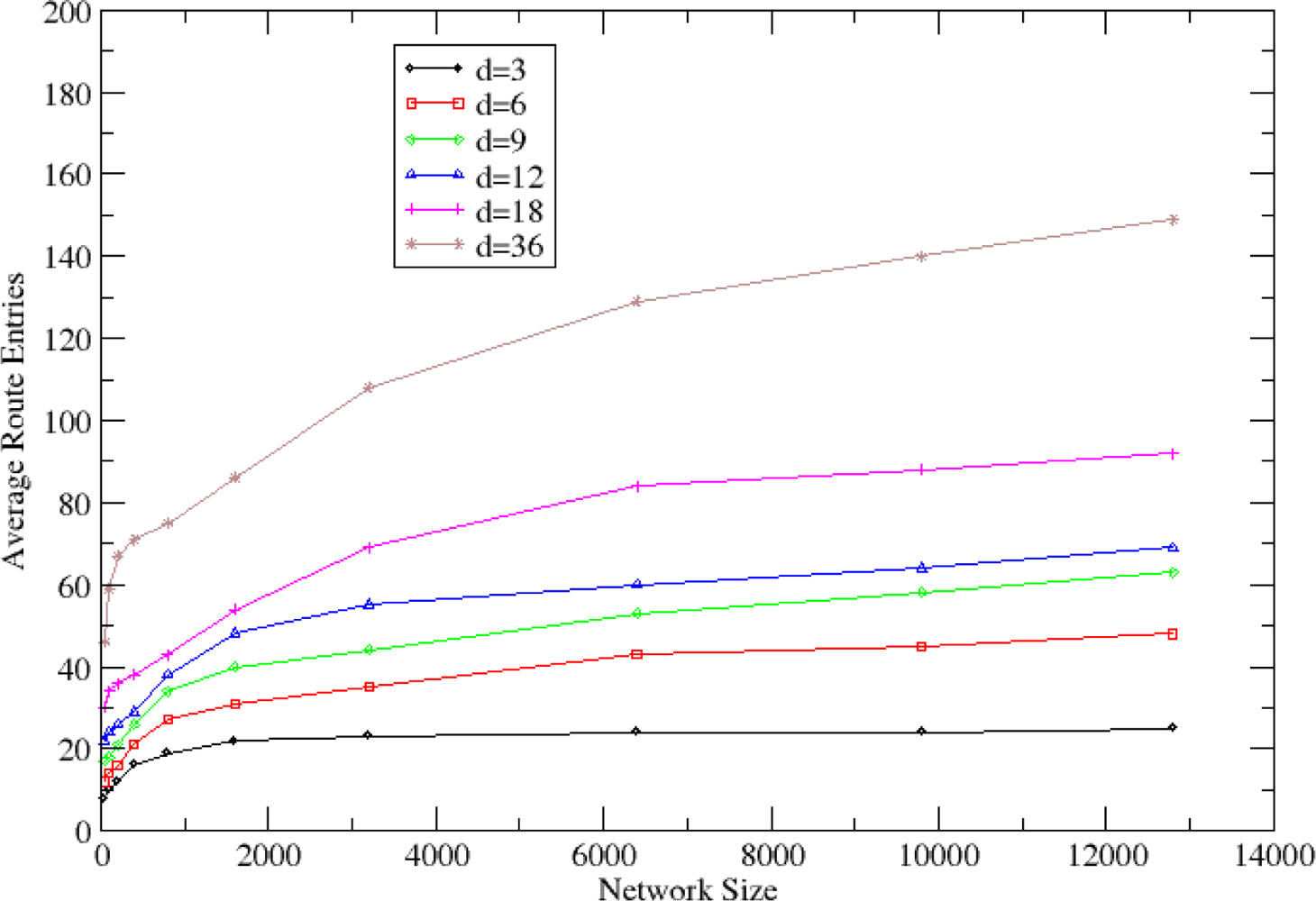
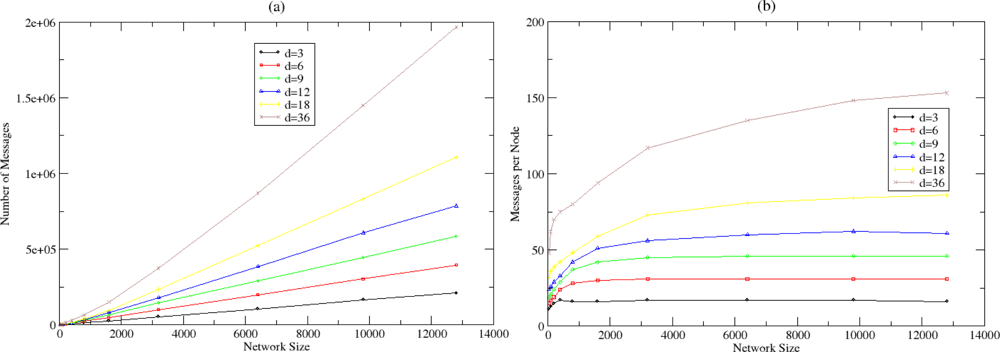
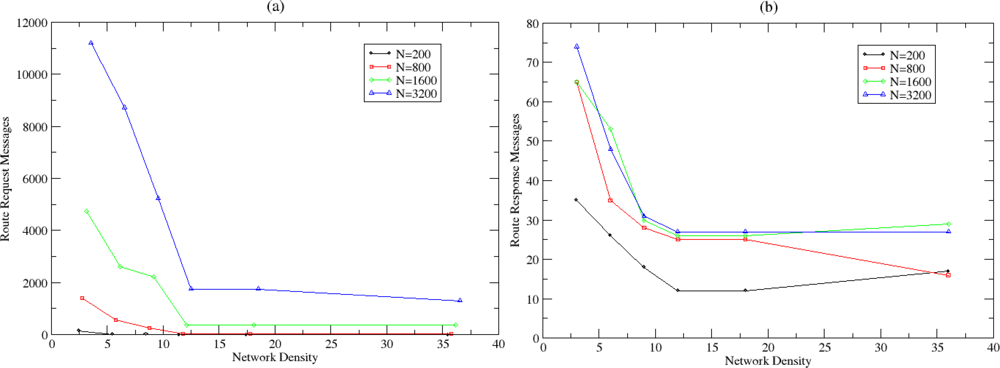
5.2. Clustering and Routing Mechanism Evaluation
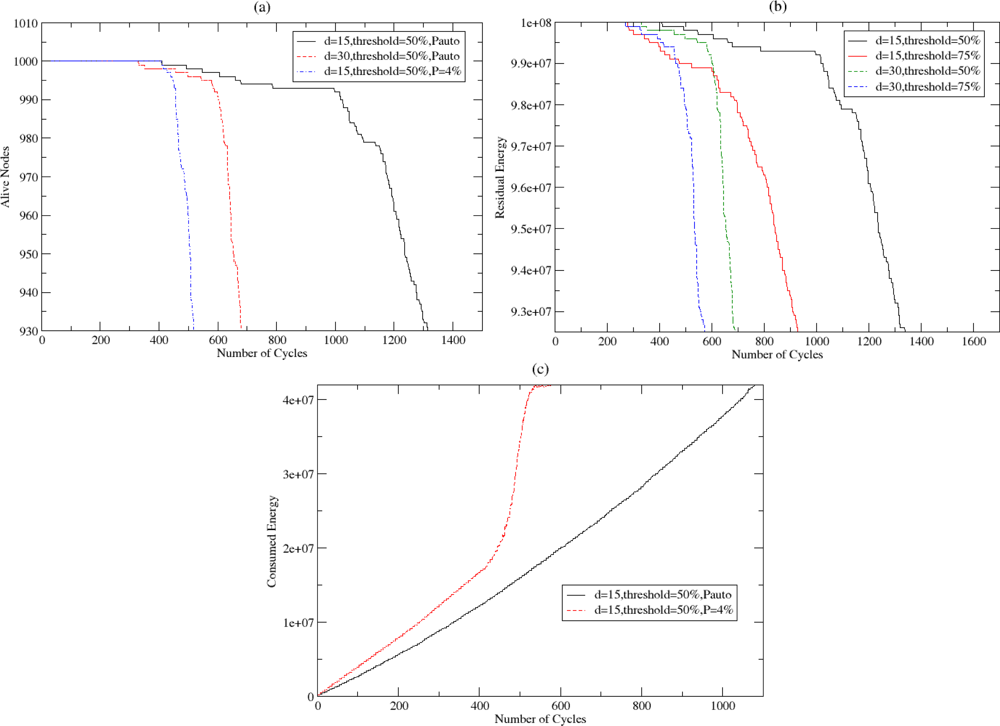
5.3. Energy Efficiency in NEURON
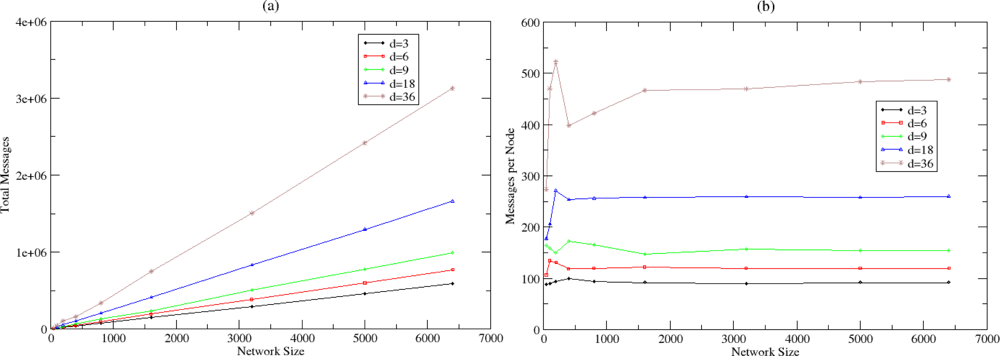
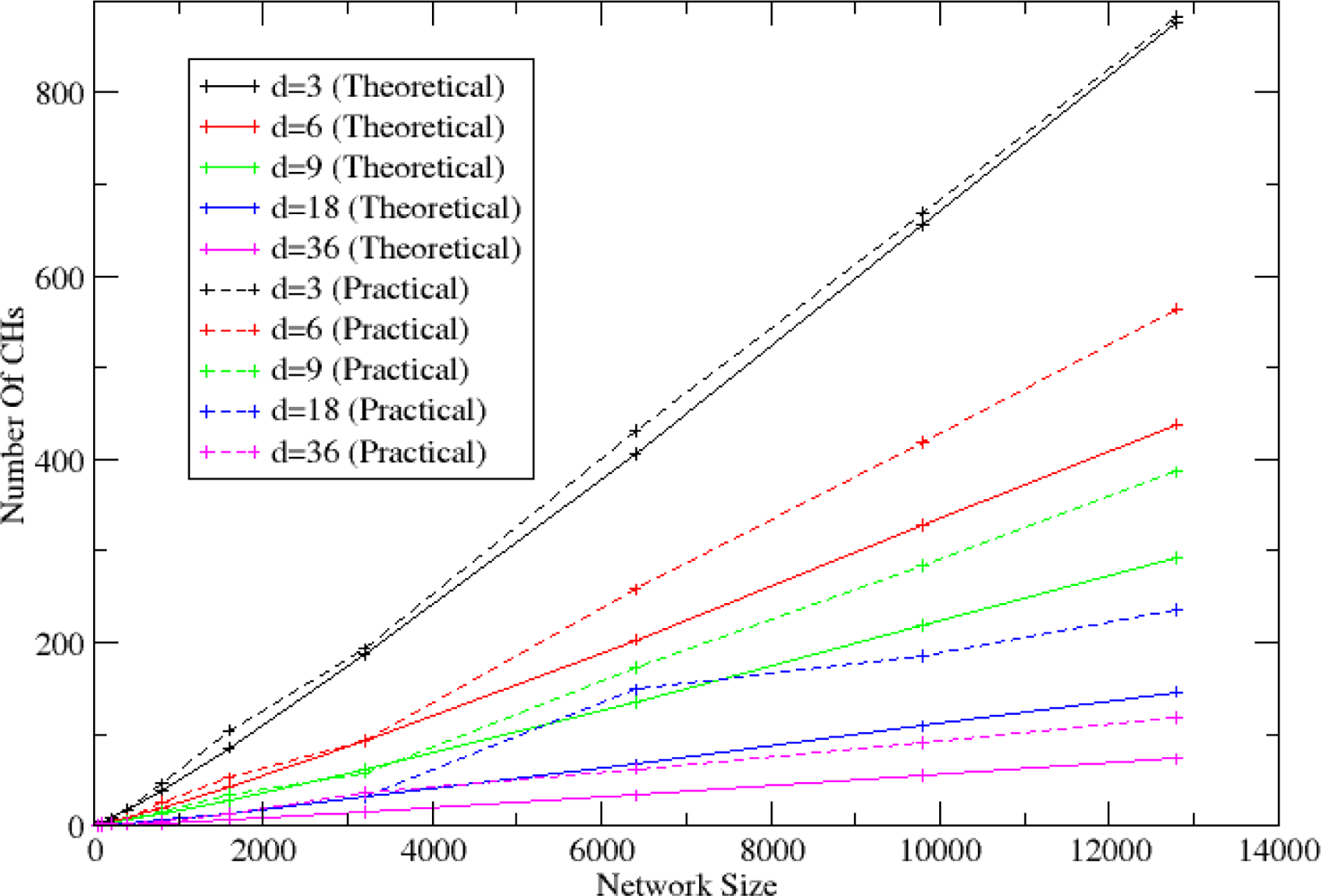
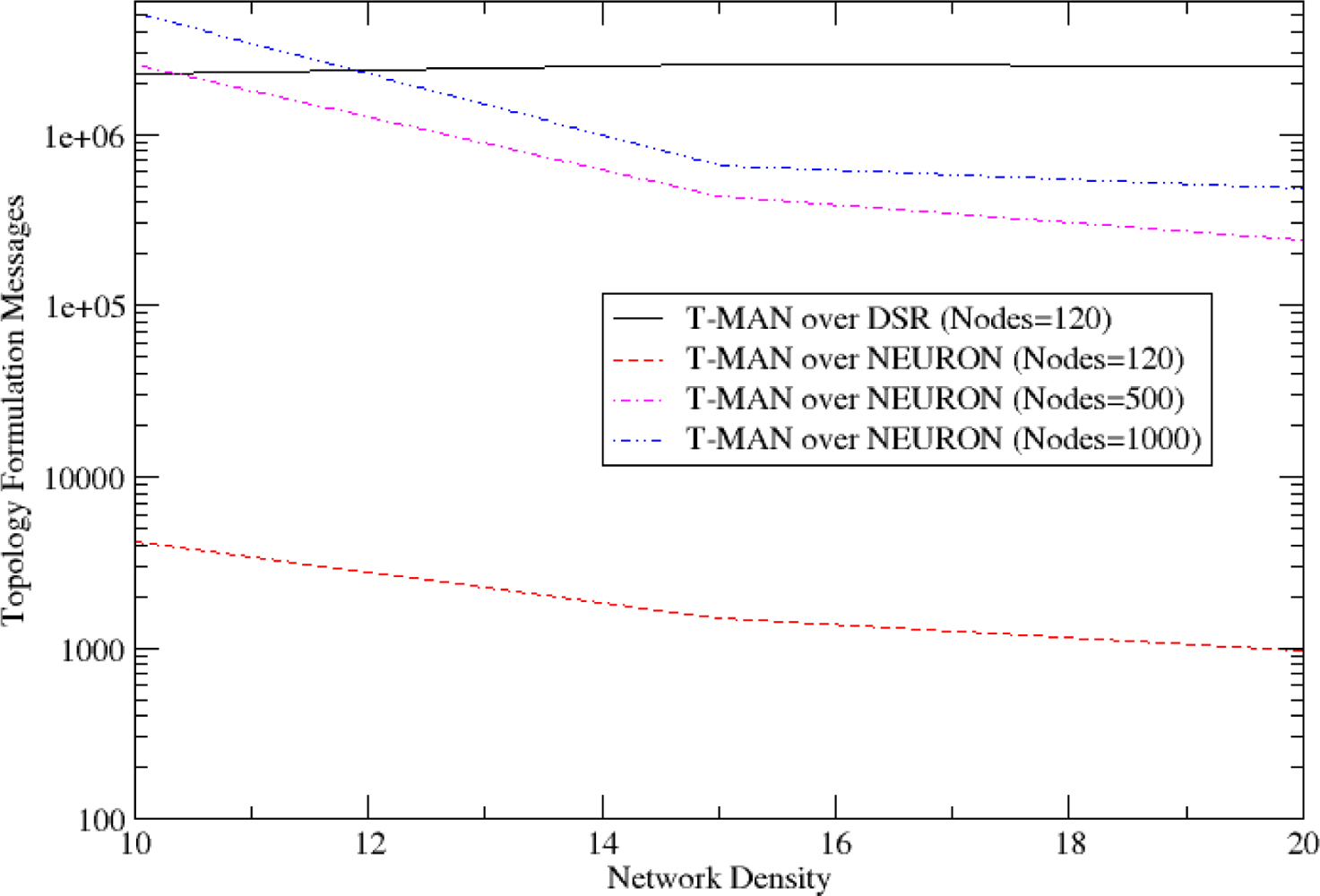
5.4. Topology Formulation Mechanism Evaluation
6. Conclusions
Acknowledgments
References
- Brasche, G. Trends and Challenges of Wireless Sensor Networks. Proceedings of the Eighth International Workshop on Applications and Services in Wireless Networks, Kassel, Germany, October 26–30, 2008; p. 7.
- Rajeev, S.; Ananda, A.; Choon, C.M.; Tsang, O.W. Mobile, Wireless, and Sensor Networks—Technology, Applications, and Future Directions; John Wiley & Sons: Hoboken, NJ, USA, 2006. [Google Scholar]
- Hui, J.W.; Culler, D.E. Extending IP to Low-Power, Wireless Personal Area Networks. IEEE Internet Comput 2008, 12, 37–45. [Google Scholar]
- Ali, M.; Langendoen, Z.K. A Case for Peer-to-Peer Network Overlays in Sensor Networks. Proceedings of the Workshop on Wireless Sensor Network, Delft, The Netherlands, January 2007.
- Dressler, F. A Study of Self-Organization Mechanisms in Ad Hoc and Sensor Networks. Comput. Commun 2008, 31, 3018–3029. [Google Scholar]
- Mills, K.L. A Brief Survey of Self-Organization in Wireless Sensor Networks. Wireless Commun. Mob. Comput 2007, 7, 823–834. [Google Scholar]
- Diaz, G. Autonomic Networks and Management of Dynamic Services Deployment—A Study of Approaches by Using Overlay Networks. Proceedings of the IEEE Global Telecommunications Conference, New Orleans, LA, USA, December 2008.
- Chatterjea, S.; Nieberg, T.; Meratnia, N.; Havinga, P. A Distributed and Self-Organizing Scheduling Algorithm for Energy-Efficient Data Aggregation in Wireless Sensor Networks. ACM Trans. Sen. Netw 2008, 4, 1–41. [Google Scholar]
- Jin, S.; Li, K. LBCS: A Load Balanced Clustering Scheme in Wireless Sensor Networks. Proceedings of the Third International Conference on the Multimedia and Ubiquitous Engineering, Qingdao, Shandong, China, June 2009; pp. 221–225.
- Lua, E.K.; Crowcroft, J.; Pias, M.; Sharma, R.; Lim, S. A Survey and Comparison of Peer-to-Peer Overlay Network Schemes. IEEE Commun. Surv. Tutorials 2005, 7, 72–93. [Google Scholar]
- Biskupski, B.; Dowling, J.; Sacha, J. Properties and Mechanisms of Self-Organising MANET and P2P Systems. ACM Trans. Auton. Adapt. Syst 2007, 2, 1–34. [Google Scholar]
- Hora, D.N.; Macedo, D.F.; Oliveira, L.B.; Siqueira, I.G.; Loureiro, A.A.; Nogueira, J.M.; Pujolle, G. Enhancing Peer-to-Peer Content Discovery Techniques Over Mobile Ad Hoc Netw. Comput. Commun 2009, 32, 1445–1459. [Google Scholar]
- Hu, Y.C.; Das, S.M.; Pucha, H. Peer-to-Peer Overlay Abstractions in Manets. In Theoretical and Algorithmic Aspects of Sensor, Ad Hoc Wireless and Peer-to-Peer Networks; CRC Press: Boca Raton, FL, USA, 2005. [Google Scholar]
- Hu, Y.; Li, W.; Kang, Z. Study on Energy Efficient Hierarchical Routing Protocols of Wireless Sensor Network. Proceedings of the International Conference on Information Engineering, Taiyuan, Shanxi, China, July 2009; pp. 325–328.
- Chamam, A.; Pierre, S. A Distributed Energy-Efficient Cluster Formation Protocol for Wireless Sensor Networks. Proceedings of the 6th IEEE Conference on Consumer Communications and Networking Conference, Las Vegas, NV, USA, January 2009.
- Chaudhry, S.A.; Jung, W.D.; Akbar, A.; Kim, K.H. Proxy-Based Service Discovery and Network Selection in 6LoWPAN. Lect. Notes Comput. Sci 2006, 4208, 525–534. [Google Scholar]
- Marsh, D.; Tynan, R.; O’Kane, D.; O’Hare, G.M.P. Autonomic Wireless Sensor Networks. Eng. Appl. Artif. Intell 2004, 17, 741–748. [Google Scholar]
- Rabiner, W.; Chandrakasan, A.; Balakrishnan, H. Energy-Efficient Communication Protocol for Wireless Microsensor Networks. Proceedings of the IEEE International Conference on System Sciences, Maui, HI, USA, January 4–7, 2000.
- Kochhal, M.; Schwiebert, L.; Gupta, S. Role-based Hierarchical Self Organization for Wireless Ad hoc Sensor Networks. Proceedings of the 2nd ACM International Conference on Wireless Sensor Networks and Applications; ACM Press: San Diego, CA, USA, 2003; pp. 98–107. [Google Scholar]
- Estrin, D.; Girod, L.; Pottie, G.; Srivastava, M. Instrumenting the World with Wireless Sensor Networks. Proceedings of the International Conference on Acoustics, Speech, and Signal Processing, Salt Lake City, UT, USA, May 7–11, 2001; pp. 2033–2036.
- Heinzelman, W.R.; Chandrakasan, A.; Balakrishnan, H. An Application-Specific Protocol Architecture for Wireless Microsensor Networks. IEEE Trans. Wireless Commun 2002, 1, 660–670. [Google Scholar]
- Huang, G.; Li, X.; He, J. Energy-Efficiency Analysis of Cluster-Based Routing Protocols in Wireless Sensor Networks. Proceedings of the IEEE Aerospace Conference, Big Sky, MT, USA, March 4–11, 2006.
- Fonseca, R.; Ratnasamy, S.; Zhao, J.; Culler, D.; Shenker, S.; Stoica, I. Beacon Vector Routing: Scalable Point-to-Point Routing in Wireless Sensornets. Proceedings of the 2nd Symposium on Networked Systems Design and Implementation, Boston, MA, USA, May 2005.
- Mao, Y.; Wang, F.; Qiu, L.; Lam, S.S.; Smith, J.M. Small State and Small Stretch Routing Protocol for Large Wireless Sensor Networks. Proceedings of the 2nd Symposium on Networked Systems Design and Implementation, Cambridge, MA, USA, April 2007.
- Iwanicki, K.; Van Steen, M. On Hierarchical Routing in Wireless Sensor Networks. Proceedings of the International Conference on Information Processing in Sensor Networks, San Francisco, CA, USA, April 2009; pp. 133–144.
- Ibriq, J.; Mahgoub, I. Cluster-Based Routing in Wireless Sensor Networks: Issues and Challenges. Proceedings of the 2004 Symposium on Performance Evaluation of Computer Telecommunication Systems, San Jose, CA, USA, July 2004; pp. 759–766.
- Jiang, C.; Yuan, D.; Zhao, Y. Towards Clustering Algorithms in Wireless Sensor Networks—A Survey. Proceedings of the IEEE Wireless Communications and Networking Conference, Budapest, Hungary, April 2009.
- Abbasi, A.; Younis, M. A Survey on Clustering Algorithms for Wireless Sensor Networks. Comput. Commun 2007, 30, 2826–2841. [Google Scholar]
- Al-Karaki, J.; Kamal, A. Routing Techniques in Wireless. Sensor Networks: A Survey. IEEE Wireless Commun 2004, 11, 6–28. [Google Scholar]
- Younis, M.; Munshi, P.; Gupta, G.; Elsharkawy, S.M. On Efficient Clustering of Wireless Sensor Networks. Proceedings of the 2nd IEEE Workshop on Dependability and Security in Sensor Networks and Systems, Pisa, Italy, April 2006; pp. 78–91.
- Younis, O.; Fahmy, S. HEED: A Hybrid, Energy-Efficient, Distributed Clustering Approach for Ad Hoc Sensor Networks. IEEE Trans. Mob. Comput 2004, 3, 366–379. [Google Scholar]
- Wang, Y.; Zhao, Q.; Zheng, D. Energy-Driven Adaptive Clustering Data Collection Protocol in Wireless Sensor Networks. Proceedings of the International Conference on Intelligent Mechatronics and Automation, Chengdu, Sichuan, China, August 26–31, 2004; pp. 599–604.
- Wu, Y.; Chen, Z.; Jing, Q.; Wang, Y. LENO: LEast Rotation Near-Optimal Cluster Head Rotation Strategy in Wireless Sensor Networks. Proceedings of the 21st International Conference on Advanced Information Networking and Applications, Niagara Falls, ON, Canada, May 2007; pp. 195–201.
- Lindsey, S.; Raghavendra, C.S. PEGASIS: Power Efficient Gathering in Sensor Information System. Proceedings of the IEEE Conference on Aerospace, Big Sky, MT, USA, March 2002; pp. 1125–1130.
- Ye, M.; Li, C.; Chen, G.; Wu, J. EECS: An Energy Efficient Clustering Scheme in Wireless Sensor Networks. Proceedings of the 24th IEEE International Performance, Computing, and Communications Conference, Phoenix, AZ, USA, April 2005; pp. 535–540.
- Lee, H.; Lee, K.; Lee, Y. A Self-Organized Head Selection for Hierarchical Routing in Wireless Sensor Networks. Proceedings of the 3rd International Workshop on Self-Organizing Systems, Vienna, Austria, December 2008.
- Wang, Y.H.; Tsai, C.H.; Mao, H.J. HMRP: Hierarchy-Based Multipath Routing Protocol for Wireless Sensor Networks. In Embedded and Ubiquitous Computing; Springer Berlin/Heidelberg: Taipei, Taiwan, 2007; pp. 452–459. [Google Scholar]
- Simón Carbajo, R.; Huggard, M.; McGoldrick, C. An End-to-End Routing Protocol for Peer-to-Peer Communication in Wireless Sensor Networks. Proceedings of the 6th Workshop on Middleware for Network Eccentric and Mobile Applications, Glasgow, Scotland, April 2008.
- Jayakumar, G.; Gopinath, G. Ad Hoc Mobile Wireless Networks Routing Protocols—A Review. J. Comput. Sci 2007, 3, 574–582. [Google Scholar]
- Johnson, D.; Maltz, D.; Broch, J. Ad Hoc Networking; Addison-Wesley: Upper Saddle River, NJ, USA, 2001; pp. 139–172. [Google Scholar]
- Bicocchi, N.; Mamei, M.; Zambonelli, F. Self-Organizing Overlay Knowledge Networks for Future Pervasive Computing Applications; American Scientific Publishers: Valencia, CA, USA, 2007. [Google Scholar]
- Stoica, I.; Morris, R.; Liben-Nowell, D.; Karger, D.R.; Kaashoek, M.F.; Dabek, F.; Balakrishnan, H. Chord: A Scalable Peer-to-Peer Lookup Protocol for Internet Applications. IEEE/ACM Trans. Networking 2003, 11, 17–32. [Google Scholar]
- Rowstron, A.; Druschel, P. Pastry: Scalable, Distributed Object Location and Routing for Large-Scale Peer-to-Peer Systems. Proceedings of the 18th IFIP/ACM International Conference on Distributed Systems Platforms, Heidelberg, Germany, November 2001.
- Jung, J.; Lee, S.; Kim, N.; Yoon, H. Efficient Service Discovery Mechanism for Wireless Sensor Networks. Comput. Commun 2008, 31, 3292–3298. [Google Scholar]
- Muneeb, A.; Zartash, A. CSN: A Network Protocol for Serving Dynamic Queries in Large-Scale Wireless Sensor Networks. Proceedings of the Annual Conference on Communication Networks and Services Research, Fredericton, NB, Canada, May 2004; pp. 165–174.
- Friedman, R.; Gavidia, D. Gossiping on MANETs: The Beauty and the Beast. ACM SIGOPS Oper. Syst. Rev 2007, 41, 67–74. [Google Scholar]
- Ding, W.; Iyengar, S.S. Bootstrapping Chord over MANETs—All Roads Lead to Rome. Proceedings of the IEEE Wireless Communications and Networking Conference, Hong Kong, China, March 2007.
- Jelasity, M.; Montresor, A.; Babaoglu, O. Gossip-Based Aggregation in Large Dynamic Networks. ACM Trans. Comput. Syst 2005, 23, 219–252. [Google Scholar]
- Samsudin, A.T.; Suryana Herman, N.; Unger, H.; Awang, M.K. The Searching Scalability of Peer-to-Peer System. Proceedings of the 10th International Conference on Advanced Communication Technology, Gangwon-Do, Korea, February 17–20, 2008; pp. 1891–1896.
- Jelasity, M.; Montresor, A.; Babaoglu, O. T-Man: Gossip-Based Fast Overlay Topology Construction. Comput. Networks 2009, 53, 2321–2339. [Google Scholar]
- Kang, E.; Kim, M.J.; Lee, E.; Kim, U. DHT-Based Mobile Service Discovery Protocol for Mobile Ad Hoc Networks. Proceedings of the 4th International Conference on Intelligent Computing, Shanghai, China, September 2008; pp. 610–619.
- Jelacity, M.; Montresor, A.; Jesi, G.; Voulgaris, S. The Peersim simulator. Available online: http://peersim.sf.net (accessed on May 2010).



| converged=false; neighbconverged=false; do forever{ if (cycle mod resetcycle ==0){ converged=false; neighbconverged=false; paramvalue = CountNeighbors(); ReceivedMSG=0; } if (ReceivedMSG!=0){ oldparamvalue= paramvalue; paramvalue=(paramvalue) / ReceivedMSG; if (Abs (oldparamvalue- paamvalue) <threshold){ converged=true; } } if (neighbconverged==false){ for (i=0;i<Neighbors.size();i++){ Send Frame[paramvalue,coverged] to Nodei } neighbconverged=true; } } | On_Message_Receive_Event{ paramvalue+=ReceivedFrame [paramvalue]; if (ReceivedFrame [converged]==false) neighbconverged=false; ReceivedMSG++; } |
| active thread | passive thread |
| do forever{ Node_To_Sentp ← selectCloserNode() buffer ← merge (view,{myNodeDescriptor}) send buffer to Node_To_Sentp receive bufferp from Node_To_Sentp buffer ← merge (bufferp ,view) view ← Reevaluate(buffer) } | do forever{ receive bufferq from Senderq buffer ← merge (view,{myNodeDescriptor}) send buffer to Senderq buffer ← merge (bufferq ,view) view ← Reevaluate (buffer) } |
| active thread | passive thread |
© 2010 by the authors; license MDPI, Basel, Switzerland. This article is an Open Access article distributed under the terms and conditions of the Creative Commons Attribution license ( http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Zafeiropoulos, A.; Gouvas, P.; Liakopoulos, A.; Mentzas, G.; Mitrou, N. NEURON: Enabling Autonomicity in Wireless Sensor Networks. Sensors 2010, 10, 5233-5262. https://doi.org/10.3390/s100505233
Zafeiropoulos A, Gouvas P, Liakopoulos A, Mentzas G, Mitrou N. NEURON: Enabling Autonomicity in Wireless Sensor Networks. Sensors. 2010; 10(5):5233-5262. https://doi.org/10.3390/s100505233
Chicago/Turabian StyleZafeiropoulos, Anastasios, Panagiotis Gouvas, Athanassios Liakopoulos, Gregoris Mentzas, and Nikolas Mitrou. 2010. "NEURON: Enabling Autonomicity in Wireless Sensor Networks" Sensors 10, no. 5: 5233-5262. https://doi.org/10.3390/s100505233