1. Introduction
A large number of wireless sensor networks (WSN)-based applications typically employ numerous inexpensive tiny nodes with on-board sensor(s). They have very limited memory space, energy, and computational power and are interconnected with simplex radio where each node itself acts as a router. The communication is generally limited between a node (source) and the cluster-head/base-station (sink). Since the nodes operate at very low radio power, typically, the transmitted power being a few milli-watts, and the communication range being limited to tens of meters, they are extremely vulnerable to jamming attacks at the physical and data link layers. However, this extreme vulnerability of the WSN to jamming is only one side of the coin. The other side is that, because it is so vulnerable, it is malleable too, and can take the imprint of the jammed area on itself, owing to its high density, spread, and synergy. WSN are, therefore, very suitable for hunting jammers, i.e., detecting, localizing and tracking the jammers for the latter’s eventual liquidation in an information war, which otherwise, is a very costly and difficult task.
1.1. Motivation
The authors have chequered experiences of more than twenty-eight years as information warriors, teachers, and researchers and find that detecting the jamming conditions and using it to localize the jammer is a complex and costly affair with the existing technology. WSN have vast military applications for tactical battle field surveillance. However, the same cannot be done effectively because of its high vulnerability to jamming. The authors are motivated to convert this weakness of the WSN into its unique strength of detecting and localizing the jammer. We, therefore, take on the problem of jamming detection in this paper, as our first effort, towards exploiting the potential of WSN in hunting for the jammer in an information war.
There is a special motivation to the approach to the problem too. The existing methods [
1–
6] of detecting the jamming conditions are node-centric, where the complete data collection, processing and decision making is done by individual nodes to arrive at a crisp decision of ‘jammed’ or ‘not jammed’. This approach is not suitable in a hostile environment because, like wounded soldiers and damaged equipment who/which are graded according to the severity of the casualty/damage, the nodes too must be graded with different jamming indices as per the severity of jamming affecting them. This would make the employment and deployment of the WSN nodes, like any other battle resource, economic and flexible to suit different stages of the information warfare. The other serious drawback of the existing approaches is that the complete processing and decision making is done at the node level. This is not practicable as the WSN nodes are resource-starved and that because nodes may not be able to communicate with others during jamming. Therefore, the authors are motivated to change the approach from decision-making being node-centric to base-station-centric and from the decision being crisp-centric to fuzzy-centric.
1.2. Paper Layout
We begin with the discussion of various types of existing jamming attack models in Section 2, such as those from Xu [
1], Muraleedharan [
2], and Cakiroglu [
3]. We then discuss the military classification of jammers, and finally, select our own models relevant to our study from the plethora of existing ones. Section 3 is the study of different possible metrics used for jamming detection and selection of some of them for our work. In Section 4, we analyze the effectiveness and suitability of the existing jamming detection methods, as relevant to the WSN in an information war environment. Section 5 is the description of our proposed mechanism for detecting jamming as well as the type of jammer, followed by the description of the simulation set-up involving NS2, MATLAB, and Simulink simulators in Section 6. In Section 7, we present the performance evaluation of our model and compare it to the other existing ones. We then conclude and outline the future work with Section 8.
1.3. Contributions
Our work has a different approach to the problem of detecting jamming, facilitating other jamming related works such as jammed area mapping, jammer localization and tracking and consequent decision making for different anti-jamming actions for various tactical operations. The major contributions are listed as follows:
Contour mapping, based on different lower cut-off values of jamming indices of nodes of the WSN (akin to altitude contours on a geographical relief map) is made possible. This is a better alternative to the present trend of plotting the jammed area, as recommended by different authors such as Wood
et al. [
7], Nowak
et al. [
8], Hellerstein
et al. [
9], and others, because instead of dividing the geographical extent of the WSN into jammed and non-jammed areas, it provides a jamming gradient to the whole area.
Flexibility in extent of jammed area mapping is possible which would give more working space to the battle field commander, e.g., in a defensive battle, during the pre-contact-with-enemy stage, when the density and health of the WSN is the best, the jammed area may be bounded by a contour of jamming index of 75% (say) and the same may expand to 50% and 25% during the contact-with-enemy stage and counter-attack stage, as the battle progresses and the density and health of the WSN goes on depleting.
Holistic decision regarding the jammed condition of a node, based on the node parameters and its neighborhood conditions is taken at the base station, and not at the node level, as done in the existing methods. This not only improves the quality of the decision and survivality of the decision making process, but also takes off the extra burden of taking such decisions from the already resource-starved nodes under siege of a jammer.
3. Metrics for Jamming Attack Detection
Xu
et al. [
1] define a jammer
‘to be an entity who is purposefully trying to interfere with the physical transmission and reception of wireless communications’. This can be achieved by the jammer by attacking at the physical layer or at the data-link layer. At the physical layer, the jammer can only jam the receiver by transmitting at high power at the network frequency and lowering the signal-to-noise ratio below the receiver’s threshold; however, it cannot prevent the transmitter from transmitting, and hence it cannot jam the transmitter. At the data link layer, it can jam the receiver by corrupting legitimate packets through protocol violations, and can also jam the transmitter by preventing it to transmit by capturing the carrier through continuous transmission (another form of protocol violation). With this
modus operandi of the jammer at the background, we examine the suitability of various metrics, as suggested by different scholars, for detecting jamming attack on a WSN.
3.1. Carrier Sensing Time (CST)
In Media Access Control (MAC) protocols, such as Carrier Sense Multiple Access (CSMA), each node keeps sensing the time for the carrier to be free so that it can then send its own packets. The average, time period for which the node has to wait for the carrier (channel) to become free and available to it is called the Carrier Sensing Time (CST). It is calculated as the mean of the time duration elapsed between the instant a node is ready to send its packet and the instant at which the carrier is found free by it for sending its packet. The nodes fix a threshold value of the CST, which if exceeded, allows it to infer that there is a jamming attack aimed at capturing the carrier. The threshold can either be fixed, as in case of 1.1.1 MAC, or taken as the minimum value over a given time period, as done in case of BMAC. This metric can be applied to only those networks using a MAC protocol based on carrier sensing. Also, this metric is incapable of indicating a physical layer power attack. It also suffers from the problem of fixing thresholds, which is an imprecise process and is computationally taxing on the scarce resources of the WSN node. We therefore, do not find it suitable for our system.
3.2. Packet Send Ratio (PSR)
Xu
et al. [
1] define PSR of a node as the ratio of the number of packets actually sent by the node during a given time period to the number of packets intended to be sent by the node during that given period. ‘The number of packets intended to be sent during a given time period’ is found by calculating the time of the channel’s availability to the node during the given period, much in the same way as in the case of CST, and then by multiplying this available time with the packet transmission rate. Finally, the PSR is calculated as defined above. The PSR-calculation is cumbersome and accordingly, we do not find it suitable for our system either.
3.3. Packet Delivery Ratio (PDR)
Both, Xu
et al. [
1] and Cakiroglu
et al. [
3] define PDR as the ratio of the number of packets successfully sent out by the node (
i.e., the number of packets for which the node has got the acknowledgement from the destination) to the total number of packets sent out by the node. Xu
et al. [
1], however, define two types of PDR: firstly, one to be measured by the transmitter (source), and secondly, one to be measured at the receiver (sink). We, while talking of the PDR, mean only the first one,
i.e., the one measured at the transmitter-end, and shall discuss the second type,
i.e., the one to be measured at the receiver-end, separately. The PDR is calculated by keeping counts of the acknowledgements of the successfully delivered packets and the total number of packets sent by the node and then by finding their ratio as a percentage. PDR is a very good metric which is capable of being measured accurately by the node without much of computational overhead, and can indicate the presence of all types of jamming attacks at the physical or data-link/MAC layer. However, the necessary condition is that the network must follow a protocol, like TCP, where the system of acknowledgement of packets exists. We feel that a resource- starved network, like the WSN, cannot afford the luxury of acknowledgements, and hence reject it from our choice.
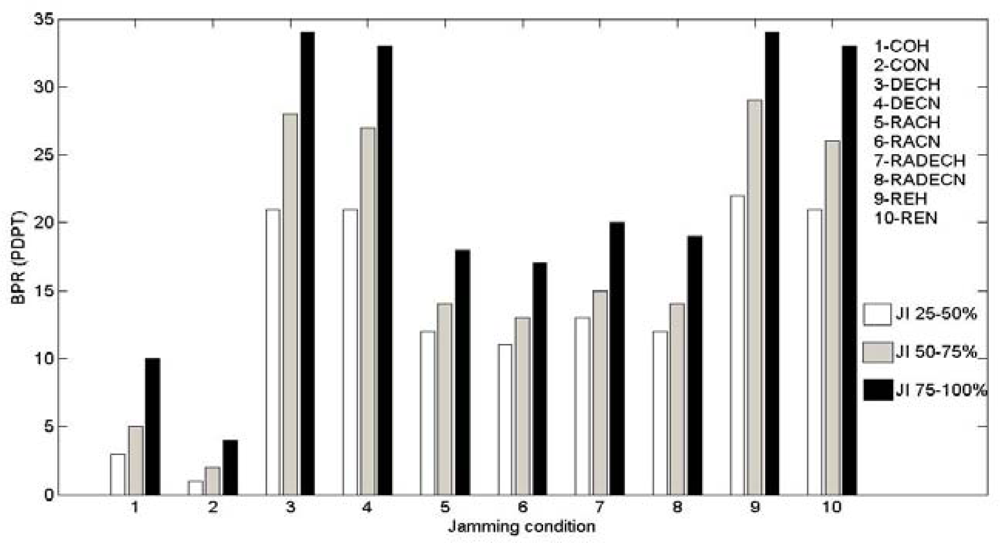
3.4. Bad Packet Ratio (BPR)
BPR is same as that PDR which is to be measured at the receiver-end, as suggested by Xu
et al. [
1]. However, Cakiroglu
et al. [
3] call it BPR and define BPR as the ratio of the number of bad packets received by a node (
i.e., the number of received packets which have not passed the Cyclic Redundancy Check (CRC) carried out by the node) to the total number of packets received by the node over a given period of time. We find BPR to be a very effective metric which can indicate all types of jamming, is easily calculable, and is fit for WSN where the system of acknowledgements is not required. The CRC is a normal procedure which nodes have to do under most of the existing protocols to check whether a received packet is correct or erroneous. If the packet is correct (good packet), it is received or queued for further transmission, and if the packet is erroneous (bad packet), it is dropped and their count is maintained. Therefore, both values, the number of bad packets and the number of total received packets, are readily available for computing the BPR without imposing any significant burden on the system. Also, there is no sampling or fixing of thresholds involved here. We find this metric suitable for our system.
3.5. Standard Deviation in Received Signal Strength (SDRSS)
Reese
et al. [
4] have suggested a system where the node samples its received legitimate signal, called the clean signal, over a period of time and finds its standard deviation (σ) during the period. It then samples the abnormal signal, called the jammed signal, and finds its mean deviation (đ) from the clean signal over the same period of time. The calculation of σ and đ are done as per formulae [
4]. If đ ≤ σ, then there is no jamming; else, there is jamming. Although we will discuss SDRSS subsequently under the method suggested by Reese
et al. [
4], we do not find it suitable for the WSN due to: (1) it cannot work if the jammer is transmitting at a power level equal to the normal transmitted power level of the nodes, as it would do during many types of jamming attacks, like deceptive jamming, as discussed above, (2) it involves sampling at the node level, and (3) it is computationally taxing for a WSN node.
3.6. Bit Error Rate (BER)
Strasser
et al. [
5] have recommended the use of BER in combination with the received signal strength (RSS), as it is not only a very effective metric for detecting jamming attack, but is also capable of identifying the reactive jamming attack, which otherwise is very difficult to identify. The BER is calculated as the ratio of the number of corrupted bits to the number of total bits received by a node during a transmission session. We concur with the authors as far as the effectiveness of this metric is concerned, but find the calculation of the BER heavily taxing for a WSN node, especially in a networking environment where the node will have to keep track of the BER of all radio links with its one-hop neighbors. Calculation and updating of BER, even at the base station level, is not feasible because it involves collection of voluminous data regarding every bit of a valid and invalid packet from the nodes leading to over-taxing of the WSN.
3.8. Signal-to-Noise Ratio (SNR) or Signal-to Jammer Power Ratio (SJR)
Although there is a subtle difference between SNR and SJR, we have considered these to be the same because, in our model jammer is the predominant noise source, and have used these terms interchangeably. SNR is calculated as the ratio of the received signal power at a node to the received noise power (or jammer power) at the node. It is almost an effective metric to identify a jamming attack at the physical layer as there can be no jamming at the physical layer without the SNR dropping low. However, some other metrics like PDR, BPR, or BER which can identify a data-link/MAC layer attack should be used with SNR for making it almost full- proof to detect jamming.
3.9. Energy Consumption Amount (ECA)
Cakiroglu
et al. [
3] define ECA as the
approximated energy amount consumed in a specified time for a sensor network. It can be calculated by measuring the drop in the battery (power-supply) voltage (
v) of the node and multiplying its squared value with the time duration and then by dividing the result with the average electrical load (resistance) of the node. The authors argue that certain jammers force sensor nodes to remain in BACKOFF period even if they should have switched to IDLE mode, causing them to consume more energy than the normal. They suggest that this consequence can be used to distinguish the normal and jamming scenarios from each other. This metric has two pit falls: firstly, the sampling of the threshold energy consumptions of the node by itself under different traffic-load conditions is a tall order, and secondly, there may not be any perceptible energy consumption differential when the jammer is attacking in a way which does not involve the carrier capture, or when the jammer is resorting to simple power attack.
3.10. Selected Metrics for the Proposed System—SNR and BPR
We select SNR and BPR as the jamming attack metrics for our system. However, we prefer to call the BPR as Packets Dropped per Terminal (PDPT) because our PDPT is the average BPR of a node during a simulation cycle. The reasons for this choice have been discussed above, and the same are summarized as follows:
The received radio power at a node is easily measurable as nodes are/can be provided with RF power meter.
In our system, the node simply keeps the base station informed about the received radio power, at a time interval as decided by the base station. The base station calculates the jammer (noise) power by subtracting the average legitimate signal power of the node from the current power. The ratio of the two powers is then calculated by the base to get the SNR. Thus there are no over-heads involved at the node level.
The node keeps the base station informed about the number of good packets and total packets received by it during a time interval, as decided by the base station, in a normal routine way. The base station calculates the BPR (or, PDPT) for each node. Thus, the nodes are not burdened additionally.
The combination of SNR and BPR (or, PDPT) is capable of detecting any form of jamming attack, as discussed in the previous sections.
4. Existing Jamming Attack Detection Methods and Their Analysis
Several scholars have suggested different mechanisms to detect jamming attacks. All of these suggested mechanisms are to be implemented at the individual node level to crisply conclude whether the node is jammed or not. Their technique is either based on threshold values of some of the metrics, as discussed before, or to use digital signal processing techniques to differentiate between a legitimate signal and an illegitimate (jamming) signal and thus conclude about the presence or absence of the jammer. Few of the methods use comparison of the node conditions with those of its neighbors to fine-tune their findings. We discuss the existing solutions, as proposed by different scholars in the following sub-sections.
4.1. Studies by Xu et al. [1]
Xu
et al. [
1] carried out intense study of the jamming attack detection mechanism with experiments using the MICA2 Mote platform. Firstly, they collected data about various percentages of the PSR and PDR (measured at the transmitter end) for constant, deceptive, random, and reactive jammers for BMAC and 1.1.1 MAC protocols for varying distances between the transmitting-node and the jammer. They considered additional jammer parameters like on-off periods for the random jammer and different packet sizes for the reactive jammer. The results show that although the PSR and the PDR vary for different jammers under different conditions, it is difficult to conclude about jamming and its type by these parameters alone. They then studied the levels of carrier sensing time, energy consumption, and the received signal strength as well as the received signal spectrum under normal and jamming conditions for two application layer protocols: Constant Bit Rate (CBR) and Maximum Traffic and tried to identify the jammer type through spectral discrimination using the Higher Order Crossing (HOC) method [
14]. They conclude through these experiments that it is not always possible to use simple statistics, such as average signal strength, energy, or carrier sensing time to discriminate jamming condition from the normal traffic, because it is difficult to devise thresholds. They also conclude that the HOC method can distinguish the constant and deceptive jamming from the normal traffic, but cannot distinguish the random and reactive jamming from the normal traffic. Finally, they conclude that if PDR is used with consistency checks like, checking own PDR and signal strength and comparing the same with those of the neighbors, and/or ascertaining own distances from the neighbors, then the combination can very effectively detect and discriminate various forms of jamming.
The study is rigorous and the suggested methodology is sound. Its limitations are: (1) the complete process has to be done by the WSN node which is taxing, and (2) that the node may not be able to communicate with its neighbors during jamming to get the required statistics for comparison, as required in the method.
4.2. Method Suggested by Rajani et al. [2]
Rajani et al. use ‘the swarm intelligence and ant system’ wherein they create an agent (ant) which proactively uses the WSN node’s information (key performance parameters), as it traverses a route from node to node, to predict or anticipate jamming, and accordingly, changes the route to avoid jamming. They suggest a decision threshold, called probability of selecting a link between nodes i and j, called Pij, to be calculated at node i. They describe that if the calculated Pij is within the acceptable limits then the agent selects the link for its travel, else, it rejects it and selects that link whose Pij is within the acceptable limits. Pij, as suggested by them, is to be calculated using complicated formulae.
Although, the approach to the problem is novel, it is obvious that it is not workable for detecting a jamming attack, especially in an information warfare environment, because: (1) some of the data, e.g., packet delivery ratio and the packet loss on a link will not be readily available normally, and if they are to be kept readily available, they will be at the cost of memory space of the node, (2) some of the data, like BER,are extremely complicated to be ascertained (as already mentioned and to be described in detail later) and involve communicating with other nodes, which may not be possible under jamming, (3) it is computation-intensive and taxes the resource-starved WSN node, (4) it involves of fixing threshold of the decision parameter for each node under different conditions, which is fraught with pit-falls, as discussed earlier, and (5) it is based on evolutionary algorithms whose complexities in terms of time and space is difficult to ascertain; but are important to be minimized for any resource-constrained network, like the WSN.
4.3. Method Suggested by Cakiroglu et al. [3]
Cakiroglu
et al. [
3] have proposed two algorithms for detecting a jamming attack. The first algorithm is based on threshold values of three detection parameters: Bad Packet Ratio (BPR), Packet Delivery Ratio (PDR), and Energy Consumption Amount (ECA). If all three parameters are below the thresholds, or if only the PDR exceeds the threshold, then it is concluded that there is no jamming; otherwise, there is jamming. The second algorithm is an improvement over the first one where the neighboring nodes’ conditions, ascertained through queries to be raised and replies there-to to be received within the threshold time periods, are also taken into account to enhance the jamming detection rate. The results of the simulations are very encouraging, thus establishing the effectiveness of the algorithms. However, the suggested models suffer from fixing of too many thresholds and processing at the node levels, which have their own problems, as discussed earlier. In addition, the PDR, measured at the transmitter-end, as in the instant case, is not suitable for the resource-constrained WSN because it imposes the avoidable burden of acknowledgements.
4.4. Method Suggested by Reese et al. [4]
Reese
et al. [
4] have proposed a method to differentiate a legitimate received signal, called clean signal,
c(t) from a signal received from a jammer, called jammed signal,
j(t) based on the standard deviation of the clean signal,
σ and the mean difference between the clean and jammed signals,
d̄, averaged over a period of time
t from
t = a to
t = b, where,
a and b are chosen constants. They first compute the root mean square value of the clean signal,
Crms, and then use it for other computations.
If d̄ is greater than σ, they conclude that it is a jamming signal; else, it is a clean signal. As evident, the calculations have to be done by the WSN node over a period of time (from t = a to t = b), very frequently, almost all the time, to keep differentiating the clean and jammed signals. This is a great disadvantage of this method, if used for jamming detection in the WSN scenario. Also, it cannot discriminate a jamming signal, if the jammer uses the same power in the jamming signal as that in the clean signal.
4.5. Method Suggested by Strasser et al. [5]
Strasser
et al. [
5] have suggested a very effective method of detecting a reactive jammer (which otherwise is so difficult to be detected) through Received Signal Strength (RSS) and Bit Error Rate (BER) samplings and inferring the presence of the reactive jammer in the event of high BER despite the RSS being normal or better than the normal. The method involves three steps: (1) error sample acquisition, (2) interference detection, and (3) sequential jamming test to infer presence or absence of reactive jamming.
Error sample acquisition is done in two sub-steps: (a) packet reception and RSS recording, i.e., forming the tuple (m, s), where, m is the sampled message packet and s is the corresponding RSS, and (b) identifying the BER.
They have suggested three methods for ascertaining whether a bit is correct or erroneous: (i) by XOR-ing the instant bit, m(i) with the predetermined value of the bit, m’(i) and concluding that the instant bit is faulty if the XOR result is true, (ii) using Error Correcting Codes (ECC), and (iii) through wired node chain (n-tuples) system, in which they generate error sample, e(i) as the result of theXOR of the bit received on the wireless link, wl(i) and the bit received by the same node from the same transmitter, transmitted simultaneously on a wired link, w(i), i.e., e(i) = wl(i) XOR w(i), and take the minimum of the RSSs received on the wireless and the wired links as the corresponding RSS, i.e., s(i) = min [swl(i), sw(i)] and form tuple [e(i), s(i)].
In the second step, interference detection, they confirm the presence of interference if e (i) = 1 (true) and s (i) > S, where S is a predetermined threshold value of the RSS, and confirm absence of interference otherwise.
In the third step, sequential jamming test, they take decision regarding presence or absence of jamming based on the values of three decision parameters: likelihood ratio η(k), targeted probability of false alarm being true TFP, and targeted probability of false alarm being not true TFN.
The method has a sound mathematical foundation and is capable of detecting all types of jamming attacks, including reactive jamming, but it cannot discriminate different types of jamming attacks. It also involves of sampling/fixing thresholds and values like those for pc, TFN, TFP, and S, the RSS threshold, which have peculiar problems, as discussed before. Besides, it is taxing on a WSN node in terms of computational and memory-space resources.
4.6. Comparison of Existing Methods
A comparative study of the existing jamming detection methods is as given in
Table 1.
4.7. Conclusions from Study of Existing Methods
Some major deductions from the discussion of various jamming-detection methods and their comparative study are: that none of the methods, except Xu’s method, is capable of discriminating various types of jamming; that they all tax the scarce resources of the nodes; that the decision is taken by the nodes based on only its own parameters and those of its neighbors (if spared by the jammer to get these) without being aware of the global scenario, and that their detection-quality is highly dependent on the ability of the victim nodes to continue communicating with their neighbors or the base station despite adverse jamming conditions. The existing methods are capable of detecting all jammers, including military warfare jammers; yet they are not suitable for information war because they are unable to grade the intensity of jamming experienced by different victim nodes, which is vital for further decision making by the battle field commander (or the base station). These inferences lead us to conclude that the existing methods are vulnerable to different jamming attacks under organized information warfare and, as such, there is a need to devise a method to obviate the vulnerabilities and improve the detection quality with the added ability of quantifying the intensity of jamming at different nodes.
5. Proposed Method
5.1. Description
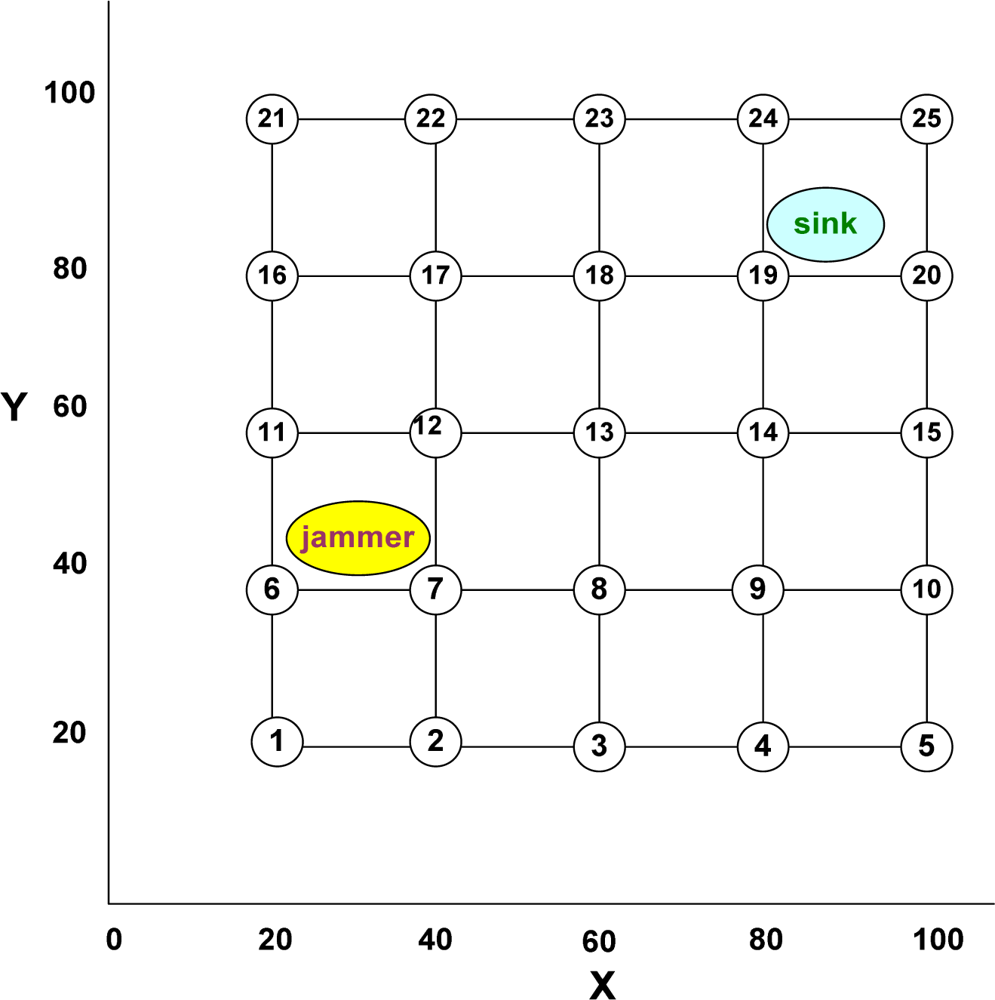
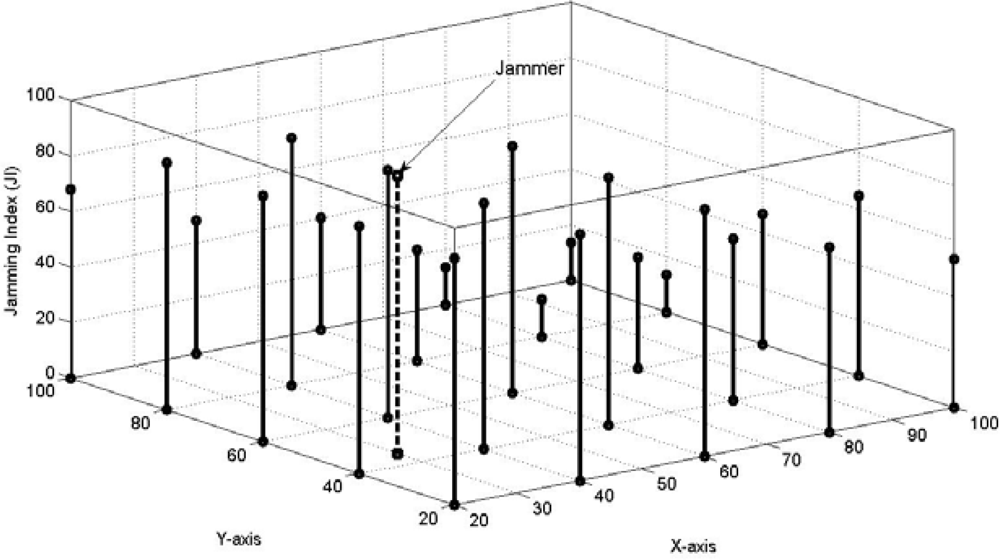
We now propose a fuzzy inference system-based jamming detection method which follows a centralized approach, wherein the jamming detection is done by the base station based on the input values of the jamming detection metrics received by it from the respective nodes. There are three inputs required to be sent by the nodes to the base station: 1) the number of total packets received by it during a specified time period, 2) the number of packets dropped by it during the period, and 3) the received signal strength (RSS). The former two metrics are normally sent to the base as part of the network health monitoring traffic at a pre-decided frequency, as part of most of the existing network management protocols. The third metric, RSS has to be additionally sent to the base station in our scheme. This can be preferably sent packaged with the former two parameters, or else, sent independently. The base station computes the ‘power received by the node from the jammer’, if any, by finding the differential between the current RSS and normal RSS values. Thereafter, the base station computes the PDPT and SNR from these values, as discussed before. Then the base station uses the values of PDPT and SNR as inputs to a fuzzy inference system (Mamdani’s Fuzzy Inference System’) to get ‘Jamming Index’ (JI) as output of the system. The JI value varies from 0 to 100, signifying ‘No Jamming’ to ‘Absolute Jamming’ respectively. In this way, the base station is able to grade the intensity of jamming being experienced by each node through the JI parameter, and thus build an overall picture.
The base station, through the overall picture that it has, is now able to do a confirmatory check through neighborhood study of any node to ascertain the correctness of the JI grade allotted to that node, as compared to the JI allotted to its neighbor nodes. This is done in our method through an algorithm called ‘2-Means Clustering of node Neighborhood’. The elegance of the method lies in doing away with the requirement of communicating with the neighbor nodes for neighborhood check. This enhances the survivality of the system during jamming.
Now, depending upon the overall picture and the battle field conditions, the battle field commander (or the base station) can decide the lower cut-off value of JI to conclude that all nodes whose JIs are greater than the lower cut-off value are ‘Jammed’ while the others are ‘Not Jammed’. The further details are described in the sub-sections that follow.
5.1.1. Detection of Jamming Attack on a Node Using Fuzzy Inference System
Definition: Fuzzy Sets and Membership Functions
Jang
et al. [
17] define fuzzy sets and membership functions as below.
If
X is a collection of objects, called the universe of discourse (uod) denoted generically by
x, then a fuzzy set
A in
X is defined as a set of ordered pairs:
where
μA (
x) is called the membership function (MF) for the fuzzy set
A. The MF maps each element of
X to a membership grade (or membership value) between 0 and 1.
In simple terms, fuzzy means one which cannot be quantified crisply, e.g., the set ‘Tall’ defined over the universe of discourse, ‘Height’ (measurable in cm), may mean different things for different people. Some may consider persons of height 180 cm or more to be tall, while for others a person of height 175 cm may also be tall. Therefore, the set ‘Tall’ is a fuzzy set. It must be noted that while the set ‘Tall’ defined over universe of discourse ‘Height’ (which may generically be denoted by h), is fuzzy, the universe of discourse ‘Height’ is a crisp set because its members will assume crisp quantifiable values in cm.
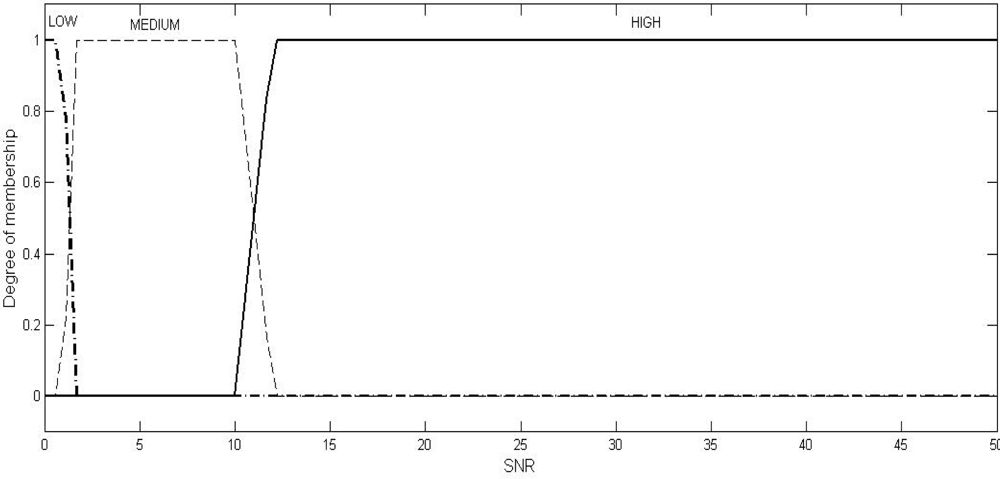
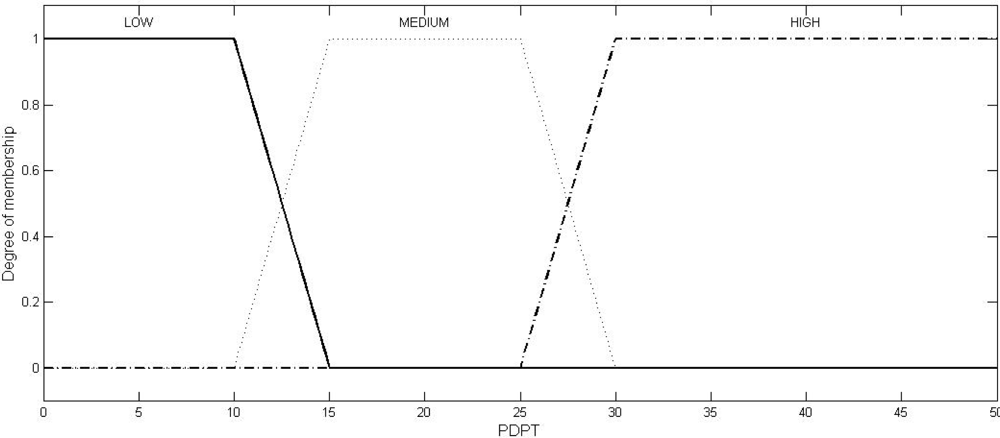
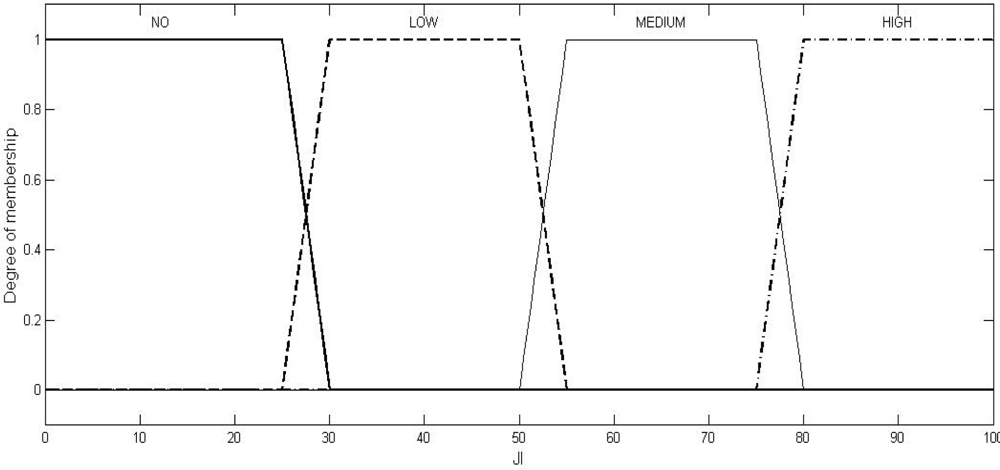
Fuzzy logic is a computational paradigm that provides a mathematical tool for representing and manipulating information in a way that resembles human communication and reasoning process [
15]. We define three fuzzy sets each over the two universes of discourse (inputs), SNR and PDPT: LOW, MEDIUM, and HIGH. Four fuzzy sets are defined over the universe of discourse, JI: NO (meaning normal), LOW, MEDIUM, and HIGH. We use Mamdani model [
16], where SNR and BPR (or, PDPT) are the crisp inputs to the system and JI is the crisp output obtained from the system after defuzzification using the centroid method.
5.1.1.1. Fuzzification Process
Multiple sets of two crisp inputs, SNR and PDPT, as generated through NS2 simulations (the simulation set up will be described in Section 6) are first mapped into fuzzy membership functions. A trapezoid shape is chosen to define fuzzy membership functions, because of two reasons: firstly, it can be mathematically manipulated to be very close to the most natural function, the Gaussian or Bell function, and secondly, it can be easily manipulated to be an unsymmetrical function (as required in the instant case) where the same cannot be done so easily with the Gaussian or Bell functions.
We define the membership functions below:
where the different values of the variables are as given in
Table 2. The values of the variables, as shown in
Table 2, have been fixed through two stages: firstly, as per the mean of the values obtained from the experts, and secondly, by the correction of these values through a feed-back factor generated by comparing the actual result (the output, JI of the system) and the expected result (the JI value, as expected by the experts). The graphical representations of these trapezoidal functions in respect of SNR, PDPT, and JI are shown in
Figures 1,
2, and
3, respectively.
5.1.1.2. Fuzzy Inference
The second step in fuzzy logic processing is fuzzy inference. A rule base, comprising of the range of rules consisting of fuzzy outputs corresponding to SNR and PDPT fuzzy inputs, was formed using the opinion of experts with rich theoretical and practical experience in jamming and counter jamming disciplines of information warfare. The rule base was further refined by vetting the system outputs by the experts. The rule base is given as follows:
If SNR is LOW and PDPT is LOW then JI is HIGH.
If SNR is LOW and PDPT is MEDIUM then JI is HIGH.
If SNR is LOW and PDPT is HIGH then JI is HIGH.
If SNR is MEDIUM and PDPT is LOW then JI is LOW.
If SNR is MEDIUM and PDPT is MEDIUM then JI is MEDIUM.
If SNR is MEDIUM and PDPT is HIGH then JI is HIGH.
If SNR is HIGH and PDPT is LOW then JI is NO.
If SNR is HIGH and PDPT is MEDIUM then JI is LOW.
If SNR is HIGH and PDPT is HIGH then JI is MEDIUM.
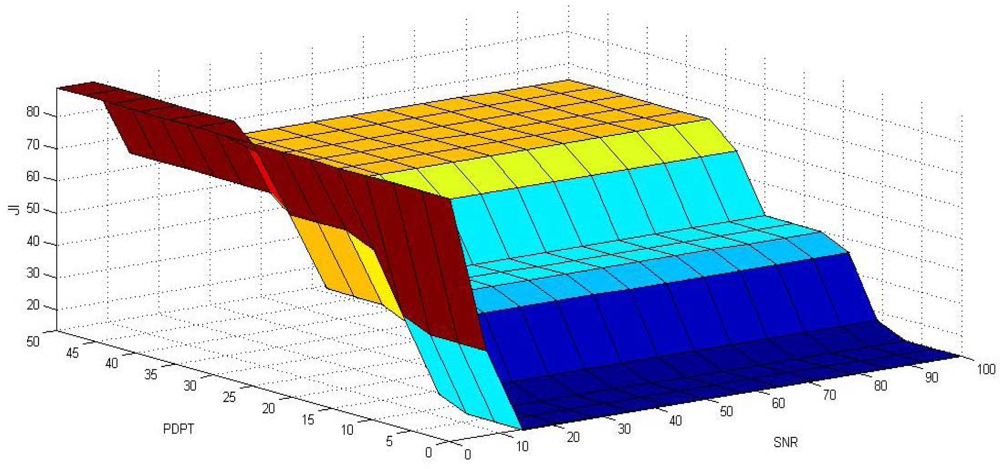
Relations obtained from the rule base are interpreted using the minimum operator ‘and’. The outputs obtained from the rule base are interpreted using maximum operator ‘or’. The overall input-output surface corresponding to the above membership functions, values of variables, and rule base is depicted in
Figure 4.
5.1.1.3. Defuzzification
The outputs of the inference mechanism are fuzzy output variables. The fuzzy logic controller must convert its internal fuzzy output variables into crisp values, through the defuzzification process, so that the actual system can use these variables. Defuzzification can be performed in several ways. We choose the Centroid of Area (COA) method [
17]. In this method, the centroid of each membership function for each rule is first evaluated. The final output, JI which is equal to COA, is then calculated as the average of the individual centroid weighted by their membership values as follows:
where,
JI or
COA is the defuzzification output,
uad and
μset(uad) are input variables and their corresponding minimum/maximum values of membership degrees. The complete process of calculating the crisp value of jamming index (JI) from input values of SNR and PDPT for every WSN node is done with MATLAB-7.
5.1.2. Confirmation of Jamming Attack on a Node Through ‘2-Means Clustering’ of Node Neighborhood
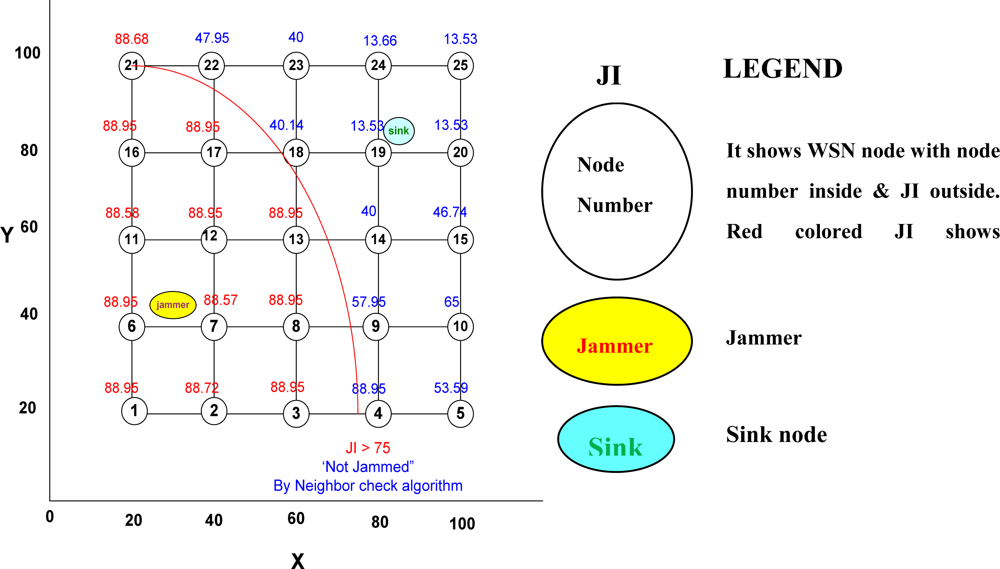
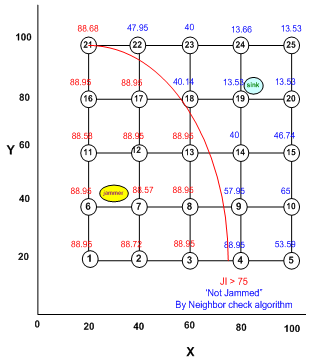
After each node has been assigned a crisp jamming index (JI) as per its SNR and PDPT values by the base station through the aforesaid method, the base station now confirms whether a node can be declared jammed or not jammed by looking at the jamming indices of neighboring nodes. This is done by the base station as follows:
Depending upon the information war conditions, it decides the lower cut-off value of JI, LC for declaring all nodes with JI ≥ LC, as jammed nodes, i.e., jamming detected at these nodes.
It makes a list of all jammed nodes, i.e., of nodes having JI ≥ LC and finds the number, t of such nodes.
For each of the
t jammed nodes, it does the following:
Identifies and counts the number of one-hop neighbors, n.
Out of the n neighbors, it identifies those neighbors who are in the list of jammed nodes and counts their number, nj and names the group of these nodes as jammed neighbors cluster.
Out of the n neighbors, it identifies those neighbors who are not in the list of jammed nodes and counts their number (n- nj) and names the group of these nodes as non-jammed neighbors cluster.
We thus have a total of n nodes divided into 2 clusters in neighborhood of a node under consideration. Therefore, the deciding figure is n/2. If the number of nodes (nj) in the jammed neighbors cluster is more than n/2 then majority of the neighbors are jammed and hence it is confirmed that the node under consideration is also jammed. If nj is less than or equal to n/2, further examination is required for taking any decision. The subsequent steps of the algorithm proceed accordingly.
If nj > n/2, then it confirms that the node is jammed.
If
nj ≤
n/2, then it does the following:
Finds the mean jamming index of
jammed neighbors cluster,
using the formula:
Finds the mean jamming index of
non-jammed neighbors cluster,
using the formula:
Finds centroid X and Y coordinates of
jammed neighbors cluster using the formula:
Finds centroid X and Y coordinates of
non-jammed neighbors cluster using the formula:
Finds the square of the distance,
dj of the node under consideration from the centroid of the
jammed neighbors cluster using the formula:
Finds the square of the distance,
dnj of the node under consideration from the centroid of the
non-
jammed neighbors cluster using the formula:
If:
then it declares that the node is jammed; otherwise, it declares that the node is not jammed and then deletes its name from the list of jammed nodes.
8. Conclusions and Future Work
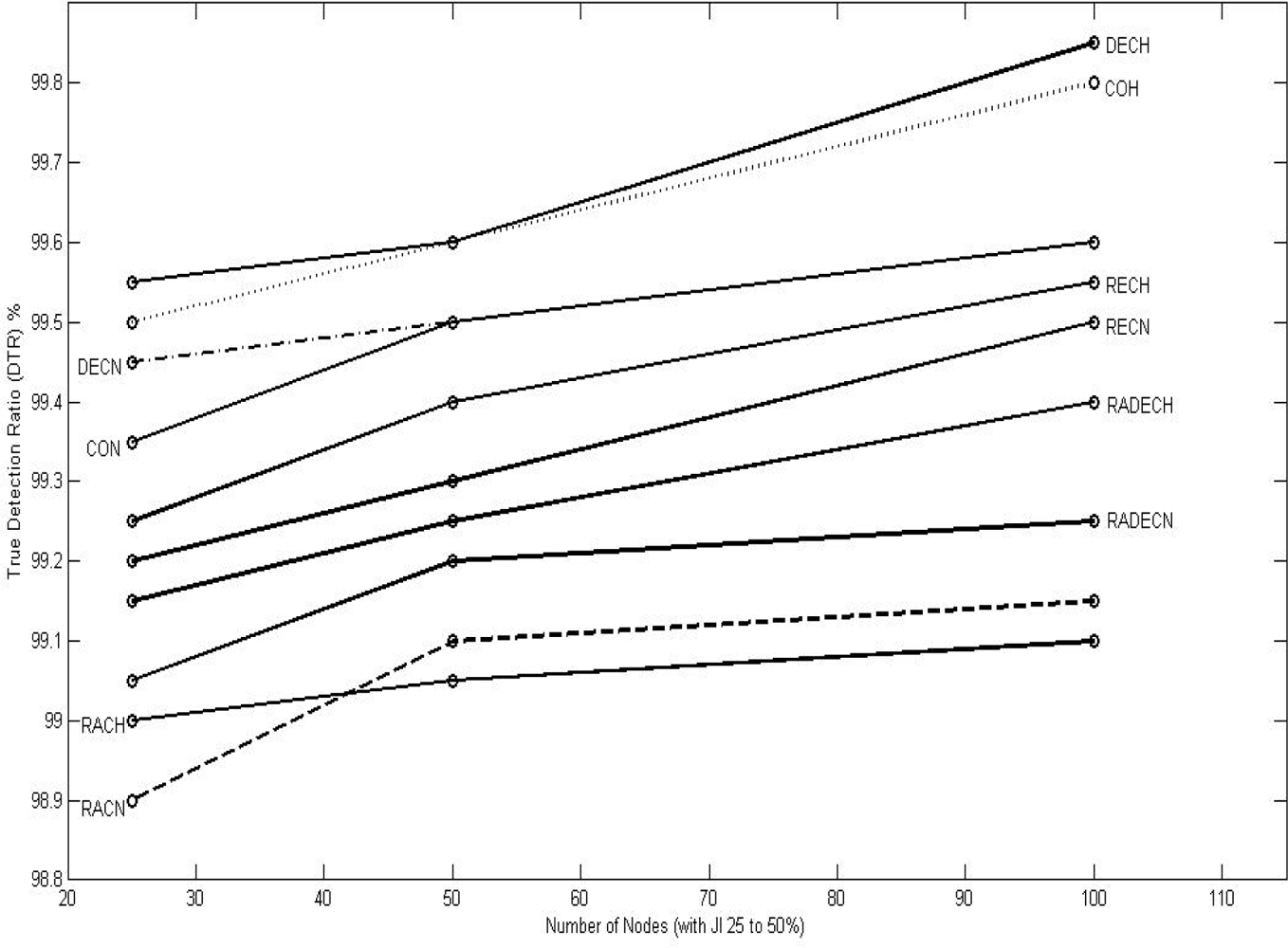
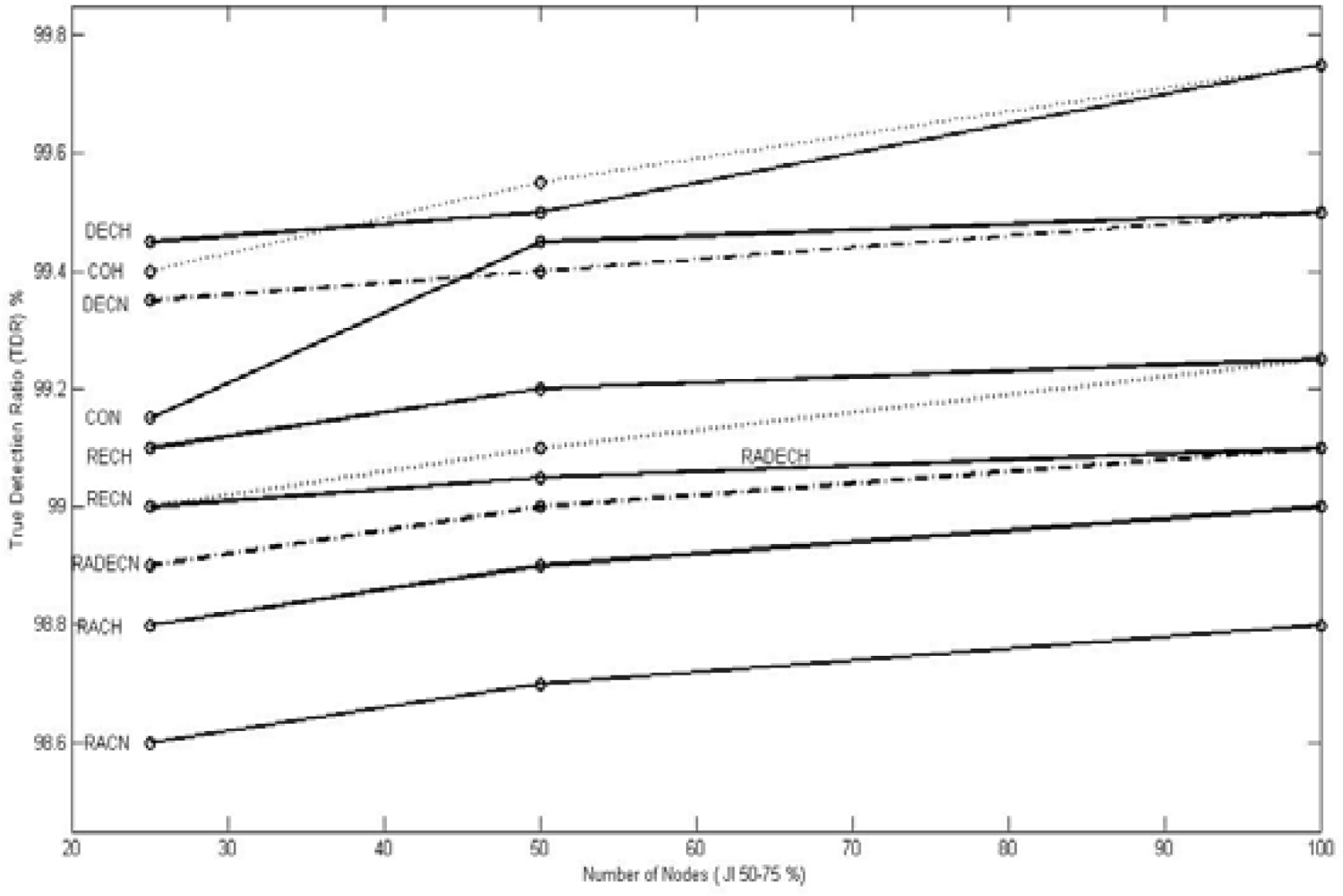
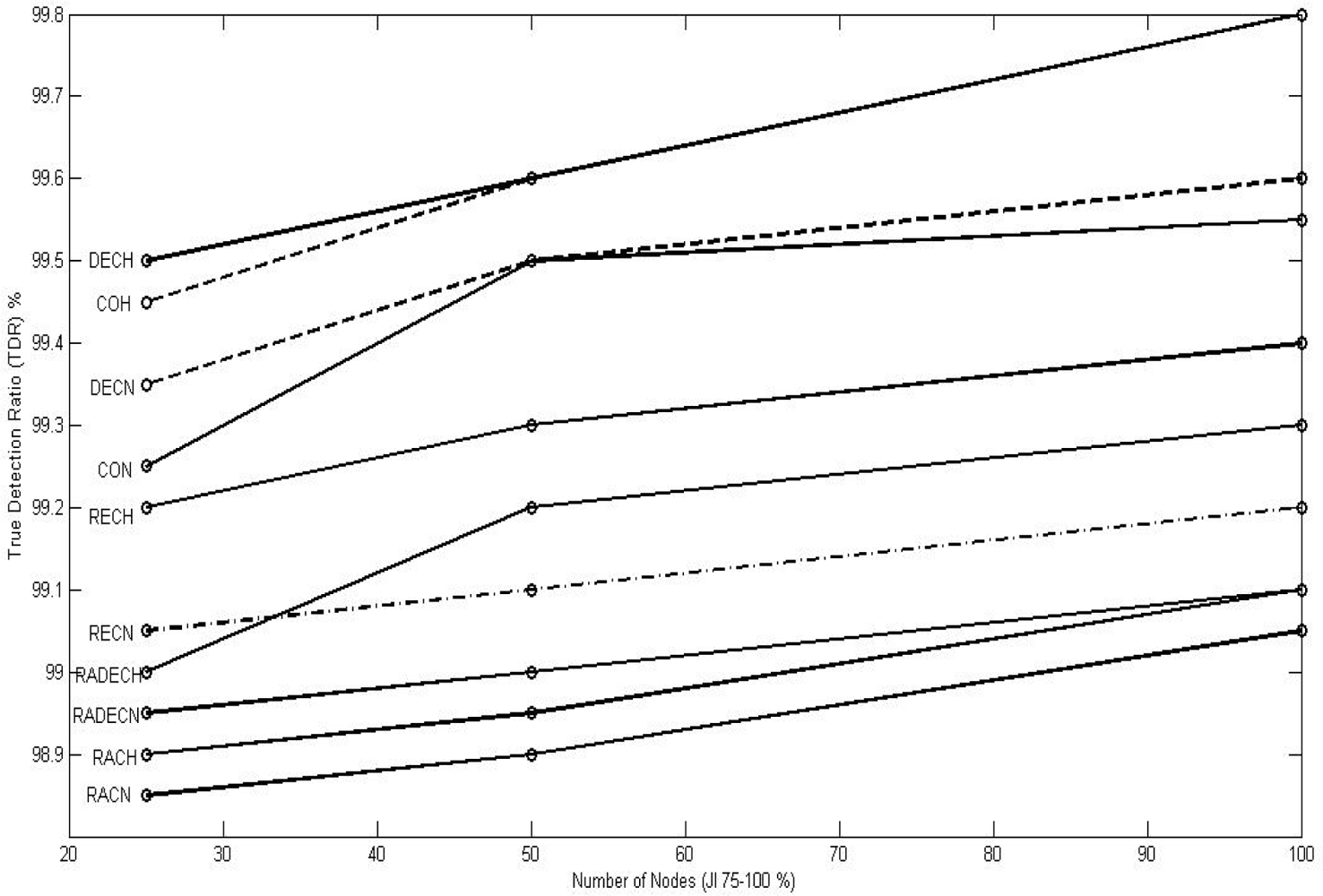
We first discussed and analyzed the various types of jamming attack models, the determinant metrics for jamming detection, and the existing methods of jamming detection as applied to the wireless sensor networks. We also discussed how our approach to the problem differed from the existing ones from three angles: (1) the scope of the lethality of the jammer being enlarged to include military jammers, (2) the existing approaches consider only two discreet levels of jamming, jammed and not jammed; where as we consider that decision about whether a node is jammed or not jammed is a fuzzy one and accordingly, aim to grade different node as per their jamming indices which suits the information war environment allowing various options to the war- zone commander (or, base station) in adopting different policies with respect to victimized nodes, and (3) the decision for jamming detection is taken by the nodes themselves in the existing methods, which we consider not feasible due to the resource constraints of the WSN nodes and their ineffectiveness in communicating with other nodes during jamming, and accordingly, we choose to do all processing and decision making at the base station on a holistic picture. Having done so, we then selected packets dropped per terminal (PDPT) and signal-to-noise ratio (SNR) as the input to our fuzzy inference system based on Mamdani model which gave the jamming index (JI) of various nodes as output. This output is further evaluated on an overall picture based on the neighborhood of the nodes. We then evaluated the system performance through the true detection ratio (TDR) and false detection ratio (FDR), and then we compared the performance with the method proposed by Cakiroglu et al. and found that our performance is better in most of the cases, matching in few cases, and not as good as the others in rare cases. We are unable to compare our performance with those of other existing models because their quantitative performance evaluation parameters are not publically available. We also analyzed the performance of the proposed approach (centralized or base-centric approach) against the existing approaches (decentralized or node-centric approach) and found that the proposed approach is matching with the existing approaches in terms of speed and energy consumption and is better in terms of accuracy. Our model has the unique advantages of providing flexibility to the battle field commander (base station) in resource (node) utilization through grading the nodes with jamming indices, and of survivality in an information war, as the model is procedure-based as against protocol-based, with the latter involving inter-node communication in a jamming environment which may not be always possible. The proposed method has the additional advantage of being able to discriminate various types of jamming attacks without getting into the complexities of digital signal processing which must be avoided as they are not practicable in the WSN scenario in an information warfare environment.
We find that our algorithm for confirmation of jamming attack on a node through ‘2-means clustering’ of node neighborhood can be refined for its performance with respect to the edge nodes, especially those in the corners. We understand that this can be done by addition of steps for discriminating edge and corner nodes from the rest and allotting various allowances to them for loss of prospective jammed or un-jammed neighbors in our algorithm. We plan to undertake this task as our future work.