Designing Labeled Graph Classifiers by Exploiting the Rényi Entropy of the Dissimilarity Representation
Abstract
:1. Introduction
2. Differential Rényi Entropy Estimators
2.1. The QRE Estimator
2.2. The MST-Based Estimator
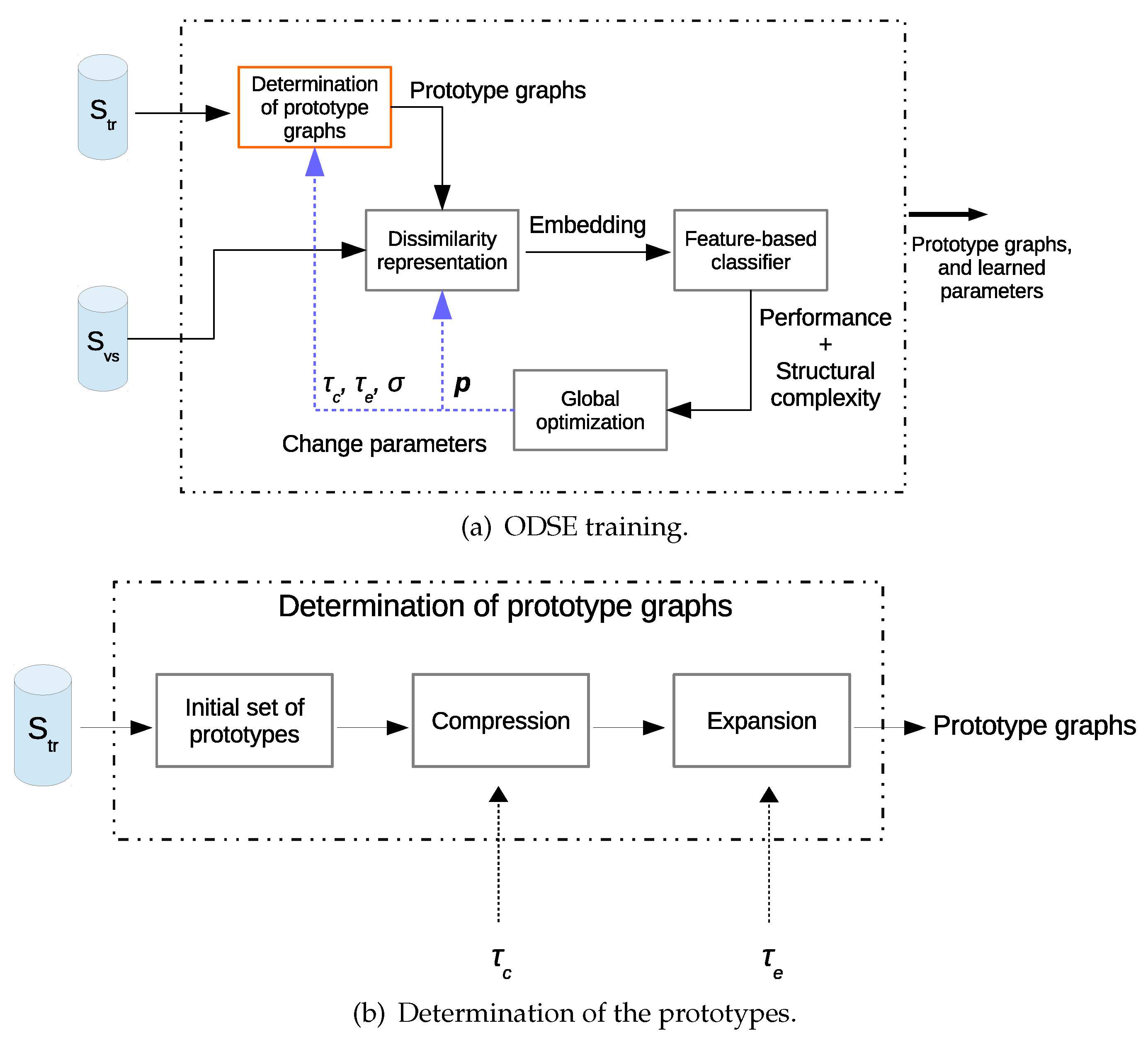
3. The Original ODSE Graph Classifier
3.1. The ODSE Objective Function
3.2. The ODSE Compression Operation
3.3. The ODSE Expansion Operation
4. The Improved ODSE Graph Classifier
4.1. ODSE with Clustering-Based Compression Operation
4.1.1. Randomized Representation Set Initialization
4.1.2. Compression by a Clustering-Based Subset Selection
| Algorithm 1 BSAS Cluster Generation Rule |
| Input: The ordered n input elements, a dissimilarity measure , the cluster radius , and the maximum number of allowed clusters Q Output: The partition 1: for do 2: if then 3: Create a new cluster in and define as the set representative 4: else 5: Get the distance value D from the closest representative modeling a cluster of the current partition 6: 7: if AND then 8: Add a new cluster in and define as the representative 9: else 10: Add in the j-th cluster and update the representative element 11: end if 12: end if 13: end for |
| Algorithm 2 Clustering-Based Compression Algorithm |
| Input: The initial set of prototype graphs , the DM , the compression threshold , and the kernel size Output: The compressed set of prototype graphs 1: Configure BSAS setting and according to Equation (17) 2: Let be the (ordered) set of dissimilarity vectors elaborated from the columns of 3: Execute the BSAS on . Let be the obtained compressible partition 4: Compute the MinSOD element of each cluster , according to Equation (18). Retrieve from the prototype graph corresponding to each dissimilarity vector 5: Define 6: return |
4.1.3. Expansion Based on Replacement with Maximum Dissimilar Graphs
4.1.4. Analysis of Computational Complexity
4.2. ODSE with Mode Seeking Initialization
Analysis of Computational Complexity
4.3. The Efficiency of the ODSE Clustering-Based Compression
5. ODSE with the MST-Based Rényi Entropy Estimator
6. Experimental Section
6.1. Datasets
6.2. Experimental Setting
6.3. Results and Discussion
7. Conclusions and Future Directions
Conflicts of Interest
Appendix A Proof of Theorem 2
Appendix B Proof of Theorem 3
References
- Livi, L.; Rizzi, A. The graph matching problem. Pattern Anal. Appl. 2013, 16, 253–283. [Google Scholar] [CrossRef]
- Dörfler, F.; Bullo, F. Kron Reduction of Graphs With Applications to Electrical Networks. IEEE Trans. Circuits Syst. 2013, 60, 150–163. [Google Scholar] [CrossRef]
- Porfiri, M.; Stilwell, D.J.; Bollt, E.M. Synchronization in random weighted directed networks. IEEE Trans. Circuits Syst. I Regul. Pap. 2008, 55, 3170–3177. [Google Scholar] [CrossRef]
- Livi, L.; Giuliani, A.; Rizzi, A. Toward a multilevel representation of protein molecules: Comparative approaches to the aggregation/folding propensity problem. Inf. Sci. 2016, 326, 134–145. [Google Scholar] [CrossRef]
- Di Paola, L.; De Ruvo, M.; Paci, P.; Santoni, D.; Giuliani, A. Protein contact networks: An emerging paradigm in chemistry. Chem. Rev. 2012, 113, 1598–1613. [Google Scholar] [CrossRef] [PubMed]
- Bianchi, F.M.; Livi, L.; Rizzi, A. Matching of Time-Varying Labeled Graphs. In Proceedings of the 2013 International Joint Conference on Neural Networks (IJCNN), Dallas, TX, USA, 4–9 August 2013; pp. 1–8. [Google Scholar]
- Serratosa, F.; Cortés, X.; Solé-Ribalta, A. Component retrieval based on a database of graphs for hand-written electronic-scheme digitalisation. Expert Syst. Appl. 2013, 40, 2493–2502. [Google Scholar] [CrossRef]
- Noma, A.; Graciano, A.B.V.; Cesar, R.M., Jr.; Consularo, L.A.; Bloch, I. Interactive image segmentation by matching attributed relational graphs. Pattern Recognit. 2012, 45, 1159–1179. [Google Scholar] [CrossRef]
- Chen, L. EM-type method for measuring graph dissimilarity. Int. J. Mach. Learn. Cybern. 2014, 5, 625–633. [Google Scholar] [CrossRef]
- Jothi, R.B.G.; Rani, S.M.M. Hybrid neural network for classification of graph structured data. Int. J. Mach. Learn. Cybern. 2015, 6, 465–474. [Google Scholar] [CrossRef]
- Livi, L.; Rizzi, A.; Sadeghian, A. Optimized dissimilarity space embedding for labeled graphs. Inf. Sci. 2014, 266, 47–64. [Google Scholar] [CrossRef]
- Bianchi, F.M.; Livi, L.; Rizzi, A.; Sadeghian, A. A Granular Computing approach to the design of optimized graph classification systems. Soft Comput. 2014, 18, 393–412. [Google Scholar] [CrossRef]
- Marfil, R.; Escolano, F.; Bandera, A. Graph-Based Representations in Pattern Recognition and Computational Intelligence. In Bio-Inspired Systems: Computational and Ambient Intelligence; Cabestany, J., Sandoval, F., Prieto, A., Corchado, J.M., Eds.; Springer: Berlin, Germany, 2009; Volume 5517, pp. 399–406. [Google Scholar]
- Bengoetxea, E.; Larrañaga, P.; Bloch, I.; Perchant, A.; Boeres, C. Inexact graph matching by means of estimation of distribution algorithms. Pattern Recognit. 2002, 35, 2867–2880. [Google Scholar] [CrossRef]
- Cesar, R.M., Jr.; Bengoetxea, E.; Bloch, I.; Larrañaga, P. Inexact graph matching for model-based recognition: Evaluation and comparison of optimization algorithms. Pattern Recognit. 2005, 38, 2099–2113. [Google Scholar] [CrossRef]
- Lozano, M.A.; Escolano, F. Protein classification by matching and clustering surface graphs. Pattern Recognit. 2006, 39, 539–551. [Google Scholar] [CrossRef]
- Bai, L.; Hancock, E.R. Graph Kernels from the Jensen–Shannon Divergence. J. Math. Imaging Vis. 2013, 47, 60–69. [Google Scholar] [CrossRef]
- Livi, L.; Sadeghian, A.; Pedrycz, W. Entropic One-Class Classifiers. IEEE Trans. Neural Netw. Learn. Syst. 2015, 26, 3187–3200. [Google Scholar] [CrossRef] [PubMed]
- Escolano, F.; Hancock, E.R.; Liu, M.; Lozano, M. Information-Theoretic Dissimilarities for Graphs. In Similarity-Based Pattern Recognition; Hancock, E., Pelillo, M., Eds.; Springer: Berlin, Germany, 2013; Volume 7953, pp. 90–105. [Google Scholar]
- Bulò, S.R.; Pelillo, M. A Game-Theoretic Approach to Hypergraph Clustering. IEEE Trans. Pattern Anal. Mach. Intell. 2013, 35, 1312–1327. [Google Scholar] [CrossRef] [PubMed]
- Shervashidze, N.; Schweitzer, P.; Leeuwen, E.J.V.; Mehlhorn, K.; Borgwardt, K.M. Weisfeiler-Lehman Graph Kernels. J. Mach. Learn. Res. 2011, 12, 2539–2561. [Google Scholar]
- Lozano, M.A.; Escolano, F. Graph matching and clustering using kernel attributes. Neurocomputing 2013, 113, 177–194. [Google Scholar] [CrossRef]
- Bai, L.; Rossi, L.; Torsello, A.; Hancock, E.R. A quantum Jensen–Shannon graph kernel for unattributed graphs. Pattern Recognit. 2015, 48, 344–355. [Google Scholar] [CrossRef]
- Bunke, H.; Riesen, K. Towards the unification of structural and statistical pattern recognition. Pattern Recognit. Lett. 2012, 33, 811–825. [Google Scholar] [CrossRef]
- Emmert-Streib, F.; Dehmer, M.; Shi, Y. Fifty years of graph matching, network alignment and network comparison. Inf. Sci. 2016, 346, 180–197. [Google Scholar] [CrossRef]
- Gibert, J.; Valveny, E.; Bunke, H. Graph embedding in vector spaces by node attribute statistics. Pattern Recognit. 2012, 45, 3072–3083. [Google Scholar] [CrossRef]
- Riesen, K.; Bunke, H. Graph Classification and Clustering Based on Vector Space Embedding; World Scientific: Singapore, 2010. [Google Scholar]
- Robles-Kelly, A.; Hancock, E.R. A Riemannian approach to graph embedding. Pattern Recognit. 2007, 40, 1042–1056. [Google Scholar] [CrossRef]
- Escolano, F.; Bonev, B.; Lozano, M. Information-Geometric Graph Indexing from Bags of Partial Node Coverages. In Proceedings of the International Workshop on Graph-Based Representations in Pattern Recognition, Münster, Germany, 18–20 May 2011; pp. 52–61. [Google Scholar]
- Luqman, M.M.; Ramel, J.Y.; LladóS, J.; Brouard, T. Fuzzy multilevel graph embedding. Pattern Recognit. 2013, 46, 551–565. [Google Scholar] [CrossRef]
- Borzeshi, E.Z.; Piccardi, M.; Riesen, K.; Bunke, H. Discriminative prototype selection methods for graph embedding. Pattern Recognit. 2013, 46, 1648–1657. [Google Scholar] [CrossRef]
- Ren, P.; Wilson, R.C.; Hancock, E.R. Graph Characterization via Ihara Coefficients. IEEE Trans. Neural Netw. 2011, 22, 233–245. [Google Scholar] [PubMed]
- Livi, L.; Del Vescovo, G.; Rizzi, A. Combining Graph Seriation and Substructures Mining for Graph Recognition. In Pattern Recognition—Applications and Methods; Latorre Carmona, P., Sánchez, J.S., Fred, A.L.N., Eds.; Springer: Berling, Germany, 2013; Volume 204, pp. 79–91. [Google Scholar]
- Jain, B.J. On the geometry of graph spaces. Discret. Appl. Math. 2016, 214, 126–144. [Google Scholar] [CrossRef]
- Jain, B.J. Statistical graph space analysis. Pattern Recognit. 2016, 60, 802–812. [Google Scholar] [CrossRef]
- Hancock, E.R.; Wilson, R.C. Pattern analysis with graphs: Parallel work at Bern and York. Pattern Recognit. Lett. 2012, 33, 833–841. [Google Scholar] [CrossRef]
- Pȩkalska, E.; Duin, R.P.W. The Dissimilarity Representation for Pattern Recognition: Foundations and Applications; World Scientific: Singapore, 2005; Volume 64. [Google Scholar]
- Schleif, F.M.; Tiňo, P. Indefinite Proximity Learning: A Review. Neural Comput. 2015, 27, 2039–2096. [Google Scholar] [CrossRef] [PubMed]
- Príncipe, J.C. Information Theoretic Learning: Renyi’s Entropy and Kernel Perspectives; Springer: Berlin, Germany, 2010. [Google Scholar]
- Livi, L.; Bianchi, F.M.; Rizzi, A.; Sadeghian, A. Dissimilarity space embedding of labeled graphs by a clustering-based compression procedure. In Proceedings of the 2013 International Joint Conference on Neural Networks (IJCNN), Turku, Finland, 17 July 2004; pp. 415–425. [Google Scholar]
- Bonev, B.; Escolano, F.; Cazorla, M. Feature selection, mutual information, and the classification of high-dimensional patterns. Pattern Anal. Appl. 2008, 11, 309–319. [Google Scholar] [CrossRef]
- Hero, A.O., III; Michel, O.J.J. Asymptotic theory of greedy approximations to minimal k-point random graphs. IEEE Trans. Inf. Theory 1999, 45, 1921–1938. [Google Scholar] [CrossRef]
- Rizzi, A.; Panella, M.; Frattale Mascioli, F.M. Adaptive resolution min-max classifiers. IEEE Trans. Neural Netw. 2002, 13, 402–414. [Google Scholar] [CrossRef] [PubMed]
- Filippone, M.; Camastra, F.; Masulli, F.; Rovetta, S. A survey of kernel and spectral methods for clustering. Pattern Recognit. 2008, 41, 176–190. [Google Scholar] [CrossRef]
- Del Vescovo, G.; Livi, L.; Frattale Mascioli, F.M.; Rizzi, A. On the Problem of Modeling Structured Data with the MinSOD Representative. Int. J. Comput. Theory Eng. 2014, 6, 9–14. [Google Scholar] [CrossRef]
- Riesen, K.; Bunke, H. IAM Graph Database Repository for Graph Based Pattern Recognition and Machine Learning. In Structural, Syntactic, and Statistical Pattern Recognition; da Vitoria Lobo, N., Kasparis, T., Roli, F., Kwok, J.T., Georgiopoulos, M., Anagnostopoulos, G.C., Loog, M., Eds.; Springer: Berlin, Germany, 2008; Volume 5342, pp. 287–297. [Google Scholar]
- Livi, L.; Del Vescovo, G.; Rizzi, A.; Frattale Mascioli, F.M. Building Pattern Recognition Applications with the SPARE Library. arXiv 2014. [Google Scholar]
- Riesen, K.; Bunke, H. Graph classification by means of Lipschitz embedding. IEEE Trans. Syst. Man Cybern. Part B 2009, 39, 1472–1483. [Google Scholar] [CrossRef] [PubMed]
- Riesen, K.; Bunke, H. Reducing the dimensionality of dissimilarity space embedding graph kernels. Eng. Appl. Artif. Int. 2009, 22, 48–56. [Google Scholar] [CrossRef]
- Bunke, H.; Riesen, K. Improving vector space embedding of graphs through feature selection algorithms. Pattern Recognit. 2011, 44, 1928–1940. [Google Scholar] [CrossRef]
- Jain, B.J.; Srinivasan, S.D.; Tissen, A.; Obermayer, K. Learning Graph Quantization. In Structural, Syntactic, and Statistical Pattern Recognition; Hancock, E.R., Wilson, R.C., Windeatt, T., Ulusoy, I., Escolano, F., Eds.; Springer: Berlin, Germany, 2010; Volume 6218, pp. 109–118. [Google Scholar]
- Jain, B.J.; Obermayer, K. Maximum Likelihood for Gaussians on Graphs. In Proceedings of the International Workshop on Graph-Based Representations in Pattern Recognition, Münster, Germany, 18–20 May 2011; Jiang, X., Ferrer, M., Torsello, A., Eds.; Volume 6658, pp. 62–71. [Google Scholar]
- Rizzi, A.; Colabrese, S.; Baiocchi, A. Low complexity, high performance neuro-fuzzy system for Internet traffic flows early classification. In Proceedings of the 2013 9th International Wireless Communications and Mobile Computing Conference (IWCMC), Sardinia, Italy, 1–5 July 2013; pp. 77–82. [Google Scholar]
- Wilson, R.C.; Hancock, E.R.; Pȩkalska, E.; Duin, R.P.W. Spherical and Hyperbolic Embeddings of Data. IEEE Trans. Pattern Anal. Mach. Intell. 2014, 36, 2255–2269. [Google Scholar] [CrossRef] [PubMed]
- Bougleux, S.; Brun, L.; Carletti, V.; Foggia, P.; Gaüzère, B.; Vento, M. Graph edit distance as a quadratic assignment problem. Pattern Recognit. Lett. 2017, 87, 38–46. [Google Scholar] [CrossRef]
| Acronym | Full Name |
|---|---|
| BSAS | Basic sequential algorithmic scheme |
| CBC | Clustering-based compression |
| DM | Dissimilarity matrix |
| DS | Dissimilarity space |
| DV | Dissimilarity value |
| IGM | Inexact graph matching |
| MinSOD | Minimum sum of distances |
| MMN | Min-max network |
| MS | Mode Seek |
| MST | Minimum spanning tree |
| MST-RE | Minimum spanning tree-Rényi entropy |
| ODSE | Optimized dissimilarity space embedding |
| QRE | Quadratic Rényi entropy |
| RS | Representation set |
| SOA | State-of-the-art |
| SVM | Support vector machines |
| TWEC | Triple-weight edit scheme |
| DS | # (tr, vs, ts) | Classes | Average | Average |
|---|---|---|---|---|
| L-L | (750, 750, 750) | 15 | 4.7 | 3.1 |
| L-M | (750, 750, 750) | 15 | 4.7 | 3.2 |
| L-H | (750, 750, 750) | 15 | 4.7 | 4.5 |
| AIDS | (250, 250, 1500) | 2 | 15.7 | 16.2 |
| P | (200, 200, 200) | 6 | 32.6 | 62.1 |
| G | (286, 286, 528) | 22 | 11.5 | 12.2 |
| M | (1500, 500, 2337) | 2 | 30.3 | 30.8 |
| C-D | (2400, 500, 1000) | 100 | 21.5 | 54.2 |
| Acronym | Init | Compression/Est. | Expansion/Est. | Obj. Func. (14) | FB Class. |
|---|---|---|---|---|---|
| ODSE2v1 | Section 4.1.1 | Section 4.1.2/QRE | Section 4.1.3/QRE | QRE | k-NN |
| ODSE2v2 | Section 4.2 | Section 4.1.2/QRE | – | QRE | k-NN |
| ODSE2v1-MST | Section 4.1.1 | Section 4.1.2/MST-RE | Section 4.1.3/QRE | MST-RE | k-NN |
| ODSE2v2-MST | Section 4.2 | Section 4.1.2/MST-RE | – | MST-RE | k-NN |
| ODSE2v1-MMN | Section 4.1.1 | Section 4.1.2/QRE | Section 4.1.3/QRE | QRE | MMN |
| ODSE2v2-MMN | Section 4.2 | Section 4.1.2/QRE | – | QRE | MMN |
| ODSE2v1-MST-MMN | Section 4.1.1 | Section 4.1.2/MST-RE | Section 4.1.3/QRE | MST-RE | MMN |
| ODSE2v2-MST-MMN | Section 4.2 | Section 4.1.2/MST-RE | – | MST-RE | MMN |
| Classifier | Dataset | Rank | |||||||
|---|---|---|---|---|---|---|---|---|---|
| L-L | L-M | L-H | AIDS | P | G | M | C-D | ||
| Reference systems | |||||||||
| RPS + TWEC + k-NN, | 98.4 | 96.0 | 95.0 | 98.5 | 45.5 | 95.0 | 69.0 | 81.0 | 15 |
| k-NN + TWEC, | 96.8 | 66.3 | 36.3 | 73.9 | 52.1 | 95.0 | 57.7 | 61.2 | 38 |
| RPS+TWEC + k-NN, | 98.6 | 97.2 | 94.7 | 98.2 | 40.5 | 92.0 | 68.7 | 63.2 | 23 |
| k-NN + TWEC, | 97.5 | 57.4 | 39.1 | 71.4 | 48.5 | 91.8 | 56.1 | 33.7 | 39 |
| RPS+TWEC + k-NN, | 98.3 | 97.1 | 95.0 | 97.6 | 35.4 | 84.8 | 68.5 | 59.7 | 32 |
| k-NN + TWEC, | 97.6 | 60.4 | 42.2 | 76.7 | 43.0 | 88.5 | 56.9 | 27.8 | 40 |
| RPS + TWEC + MMN | 98.0 | 96.0 | 93.6 | 97.4 | 49.5 | 95.0 | 66.0 | 68.4 | 28 |
| SOA systems | |||||||||
| GMM + soft all + SVM [26] | 99.7 | 93.0 | 87.8 | - | - | 99.0 | - | 98.1 | 12 |
| Fuzzy k-means+soft all + SVM [26] | 99.8 | 98.8 | 85.0 | - | - | 98.1 | - | 97.3 | 9 |
| sk + SVM [48] | 99.7 | 85.9 | 79.1 | 97.4 | - | 94.4 | 55.4 | - | 30 |
| le + SVM [48] | 99.3 | 95.9 | 92.5 | 98.3 | - | 96.8 | 74.3 | - | 7 |
| PCA + SVM [49] | 92.7 | 81.1 | 73.3 | 98.2 | - | 92.9 | 75.9 | 93.6 | 26 |
| MDA + SVM [49] | 89.8 | 68.5 | 60.5 | 95.4 | - | 91.8 | 62.4 | 88.2 | 37 |
| svm + SVM [50] | 99.2 | 94.7 | 92.8 | 98.1 | 71.5 | 92.2 | 68.3 | - | 17 |
| svm + kPCA [50] | 99.2 | 94.7 | 90.3 | 98.1 | 67.5 | 91.6 | 71.2 | - | 14 |
| lgq [51] | 81.5 | - | - | - | - | 86.2 | - | - | 35 |
| bayes1 [52] | 80.4 | - | - | - | - | 80.3 | - | - | 36 |
| bayes2 [52] | 81.3 | - | - | - | - | 89.9 | - | - | 34 |
| FMGE + k-NN [30] | 97.1 | 75.7 | 66.5 | - | - | 97.5 | 69.1 | - | 31 |
| FMGE + SVM [30] | 98.2 | 83.1 | 70.0 | - | - | 99.4 | 76.5 | - | 21 |
| d-sps-SVM [31] | 99.5 | 95.4 | 93.4 | 98.2 | 73.0 | 92.5 | 71.5 | - | 8 |
| GRALGv1 [12] | 98.2 | 75.6 | 69.6 | 99.7 | - | 97.7 | 73.0 | 94.0 | 10 |
| GRALGv2 [12] | 97.6 | 89.6 | 82.6 | 99.7 | 64.6 | 97.6 | 73.0 | 97.8 | 6 |
| Original ODSE | |||||||||
| ODSE, [11] | 98.6 | 96.8 | 96.2 | 99.6 | 61.0 | 96.2 | 73.4 | - | 1 |
| Improved ODSE with QRE | |||||||||
| ODSE2v1, [40] | 99.0 | 97.0 | 96.1 | 99.1 | 61.2 | 98.1 | 68.2 | 78.1 | 4 |
| ODSE2v2, [40] | 98.7 | 97.1 | 95.4 | 99.5 | 51.9 | 95.4 | 68.1 | 77.2 | 5 |
| ODSE2v1, [40] | 99.0 | 97.2 | 96.1 | 99.3 | 41.4 | 90.2 | 68.7 | 64.3 | 13 |
| ODSE2v2, [40] | 98.8 | 97.4 | 95.1 | 99.4 | 31.4 | 38.0 | 69.4 | 59.0 | 24 |
| ODSE2v1, [40] | 99.1 | 96.8 | 95.2 | 99.0 | 38.9 | 85.4 | 69.0 | 58.6 | 27 |
| ODSE2v2, [40] | 98.7 | 97.0 | 95.6 | 99.4 | 31.3 | 82.5 | 70.0 | 54.0 | 25 |
| ODSE2v1-MMN | 98.3 | 95.2 | 94.0 | 99.3 | 53.1 | 94.5 | 67.9 | 62.8 | 22 |
| ODSE2v2-MMN | 97.8 | 95.6 | 93.6 | 99.6 | 48.7 | 94.8 | 68.2 | 59.2 | 29 |
| Improved ODSE with MST-RE | |||||||||
| ODSE2v1-MST, | 98.6 | 96.8 | 98.9 | 99.3 | 61.3 | 95.6 | 70.0 | 81.0 | 3 |
| ODSE2v2-MST, | 98.4 | 97.1 | 96.0 | 99.7 | 51.0 | 94.1 | 71.6 | 82.0 | 2 |
| ODSE2v1-MST, | 98.7 | 97.0 | 96.8 | 99.5 | 43.0 | 92.3 | 68.6 | 64.8 | 11 |
| ODSE2v2-MST, | 98.8 | 96.9 | 96.0 | 99.7 | 35.0 | 91.0 | 69.4 | 60.0 | 16 |
| ODSE2v1-MST, | 99.0 | 96.8 | 95.6 | 99.6 | 41.4 | 85.0 | 68.6 | 60.0 | 18 |
| ODSE2v2-MST, | 98.8 | 97.0 | 95.5 | 99.7 | 32.9 | 83.3 | 70.0 | 54.0 | 19 |
| ODSE2v1-MST-MMN | 97.9 | 95.4 | 93.6 | 99.3 | 49.9 | 95.0 | 68.3 | 62.6 | 20 |
| ODSE2v2-MST-MMN | 97.9 | 95.1 | 91.8 | 99.2 | 48.5 | 94.8 | 67.1 | 59.0 | 33 |
| Classifier | Dataset | |||||||
|---|---|---|---|---|---|---|---|---|
| L-L | L-M | L-H | AIDS | P | G | M | C-D | |
| ODSE [11] | 0.0256 | 1.2346 | 0.2423 | 0.0000 | 0.7356 | 0.4136 | 0.6586 | - |
| ODSE2v1, [40] | 0.0769 | 0.2309 | 0.1539 | 0.0000 | 2.6242 | 1.3350 | 0.5187 | 4.3863 |
| ODSE2v2, [40] | 0.0769 | 0.0769 | 0.4000 | 0.0000 | 0.2915 | 0.8021 | 0.5622 | 2.2654 |
| ODSE2v1, [40] | 0.0769 | 0.2309 | 0.2666 | 0.0000 | 1.0513 | 1.2236 | 0.0856 | 0.0577 |
| ODSE2v2, [40] | 0.0769 | 0.4618 | 5.0800 | 0.1924 | 1.1666 | 3.1540 | 0.0356 | 1.2361 |
| ODSE2v1, [40] | 0.5047 | 0.0769 | 0.9365 | 0.1924 | 0.5050 | 2.5585 | 0.3803 | 1.3279 |
| ODSE2v2, [40] | 0.1333 | 0.2309 | 0.0769 | 0.0000 | 2.7815 | 4.5220 | 1.2666 | 0.0026 |
| ODSE2v1-MMN | 0.1520 | 0.3320 | 0.3932 | 0.1861 | 1.7740 | 0.7315 | 1.1300 | 1.0001 |
| ODSE2v2-MMN | 0.2022 | 0.2022 | 0.7682 | 0.0000 | 2.7290 | 1.3584 | 1.4080 | 0.3896 |
| ODSE2v1-MST, | 0.0730 | 0.0730 | 0.1115 | 0.2772 | 1.5500 | 0.1055 | 1.0786 | 0.4163 |
| ODSE2v2-MST, | 0.0596 | 0.2231 | 0.0730 | 0.0000 | 1.1660 | 0.2943 | 0.9534 | 0.2146 |
| ODSE2v1-MST, | 0.1192 | 0.1520 | 0.0942 | 0.6982 | 1.0940 | 0.0000 | 0.5926 | 1.7088 |
| ODSE2v2-MST, | 0.1460 | 0.2022 | 0.0730 | 0.0000 | 0.0000 | 0.1112 | 0.2365 | 0.5655 |
| ODSE2v1-MST, | 0.1115 | 0.0942 | 0.2190 | 0.0596 | 0.4748 | 0.0000 | 0.0547 | 1.2356 |
| ODSE2v2-MST, | 0.0730 | 0.0596 | 0.9933 | 0.0000 | 0.0000 | 0.1112 | 1.0023 | 0.9563 |
| ODSE2v1-MST-MMN | 0.1115 | 0.4216 | 0.7624 | 0.3217 | 2.5735 | 0.3067 | 0.7926 | 0.9899 |
| ODSE2v2-MST-MMN | 0.0596 | 0.7636 | 0.7477 | 0.0000 | 2.7290 | 0.5828 | 0.8911 | 1.2020 |
| Classifier | Dataset | |||||||
|---|---|---|---|---|---|---|---|---|
| L-L | L-M | L-H | AIDS | P | G | M | C-D | |
| ODSE [11] | 63274 | 52285 | 28938 | 394 | 8460 | 601 | 43060 | - |
| ODSE2v1 [40] | 284 (222) | 329 (158) | 328 (88) | 38 (10) | 3187 (3) | 210 (3) | 3494 (12) | 2724 |
| ODSE2v2 [40] | 126 (502) | 268 (195) | 183 (158) | 110 (3) | 1683 (5) | 96 (6) | 10326 (4) | 8444 |
| ODSE2v1-MMN | 129 (490) | 284 (184) | 263 (110) | 17 (23) | 3638 (2) | 170 (4) | 8837 (5) | 5320 |
| ODSE2v2-MMN | 195 (324) | 422 (124) | 183 (158) | 86 (5) | 1444 (6) | 77 (8) | 28511 (2) | 20301 |
| ODSE2v1-MST | 213 (297) | 231 (226) | 225 (129) | 18 (22) | 3860 (2) | 168 (4) | 2563 (17) | 3261 |
| ODSE2v2-MST | 145 (463) | 160 (327) | 107 (270) | 93 (4) | 2075 (4) | 74 (8) | 7675 (6) | 10092 |
| ODSE2v1-MST-MMN | 201 (315) | 249 (210) | 205 (141) | 15 (26) | 3450 (2) | 155 (4) | 5496 (8) | 7135 |
| ODSE2v2-MST-MMN | 117 (541) | 176 (292) | 118 (245) | 83 (5) | 1380 (6) | 75 (8) | 28007 (2) | 16599 |
| Classifier | Dataset | |||||||
|---|---|---|---|---|---|---|---|---|
| L-L | L-M | L-H | AIDS | P | G | M | C-D | |
| ODSE [11] | 435 | 750 | 750 | 250 | 200 | 283 | 1500 | - |
| ODSE2v1 [40] | 146 | 449 | 449 | 8 | 197 | 283 | 760 | 615 |
| ODSE2v2 [40] | 183 | 431 | 338 | 7 | 82 | 126 | 801 | 770 |
| ODSE2v1-MM | 136 | 192 | 144 | 6 | 190 | 163 | 563 | 555 |
| ODSE2v2-MM | 197 | 546 | 80 | 2 | 93 | 115 | 815 | 740 |
| ODSE2v1-MST | 597 | 595 | 597 | 6 | 198 | 283 | 687 | 618 |
| ODSE2v2-MST | 551 | 574 | 447 | 61 | 122 | 129 | 813 | 775 |
| ODSE2v1-MST-MMN | 600 | 606 | 500 | 5 | 190 | 184 | 424 | 549 |
| ODSE2v2-MST-MMN | 550 | 580 | 411 | 61 | 93 | 115 | 456 | 733 |
| Classifier | Datasets | |||||||
|---|---|---|---|---|---|---|---|---|
| L-L | L-M | L-H | AIDS | P | G | M | C-D | |
| ODSE2v1-MST, | 0.740 | 0.740 | 0.740 | 0.130 | 0.020 | 0.060 | 9.020 | 9.700 |
| ODSE2v1-MST-MMN | 0.105 | 0.105 | 0.105 | 0.005 | 0.014 | 0.045 | 6.600 | 5.250 |
| Classifier | Dataset | |||||||
|---|---|---|---|---|---|---|---|---|
| L-L | L-M | L-H | AIDS | P | G | M | C-D | |
| ODSE2v1-MMN | 15 | 39 | 34 | 5 | 43 | 27 | 164 | 357 |
| ODSE2v2-MMN | 15 | 28 | 41 | 4 | 48 | 28 | 159 | 368 |
| ODSE2v1-MST-MMN | 15 | 27 | 38 | 3 | 48 | 28 | 168 | 348 |
| ODSE2v2-MST-MMN | 15 | 27 | 34 | 4 | 43 | 27 | 175 | 365 |
© 2017 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Livi, L. Designing Labeled Graph Classifiers by Exploiting the Rényi Entropy of the Dissimilarity Representation. Entropy 2017, 19, 216. https://doi.org/10.3390/e19050216
Livi L. Designing Labeled Graph Classifiers by Exploiting the Rényi Entropy of the Dissimilarity Representation. Entropy. 2017; 19(5):216. https://doi.org/10.3390/e19050216
Chicago/Turabian StyleLivi, Lorenzo. 2017. "Designing Labeled Graph Classifiers by Exploiting the Rényi Entropy of the Dissimilarity Representation" Entropy 19, no. 5: 216. https://doi.org/10.3390/e19050216






