Exploring the Key Risk Factors for Application of Cloud Computing in Auditing
Abstract
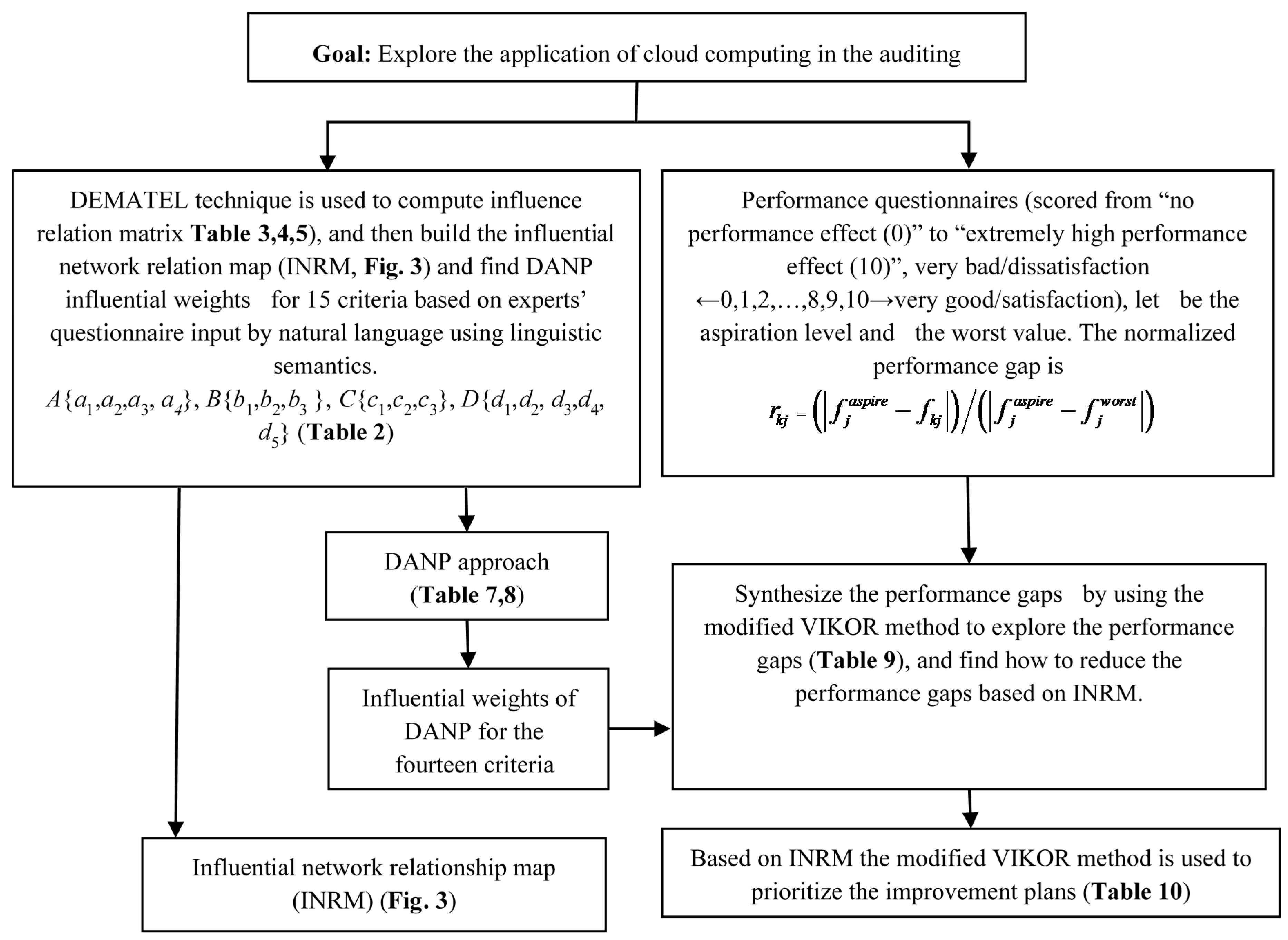
:1. Introduction
- Which risk factors should be considered by CPA firms when cloud computing?
- When are these risk factors in the mutual influence and conflict and which are those are the key factors?
- When based on domain experts’ cognition, those risk factors affect the executive performance?
2. Related Literature
2.1. Protection System
2.2. Technology Risks
2.3. Automating User Provisioning
2.4. Operations
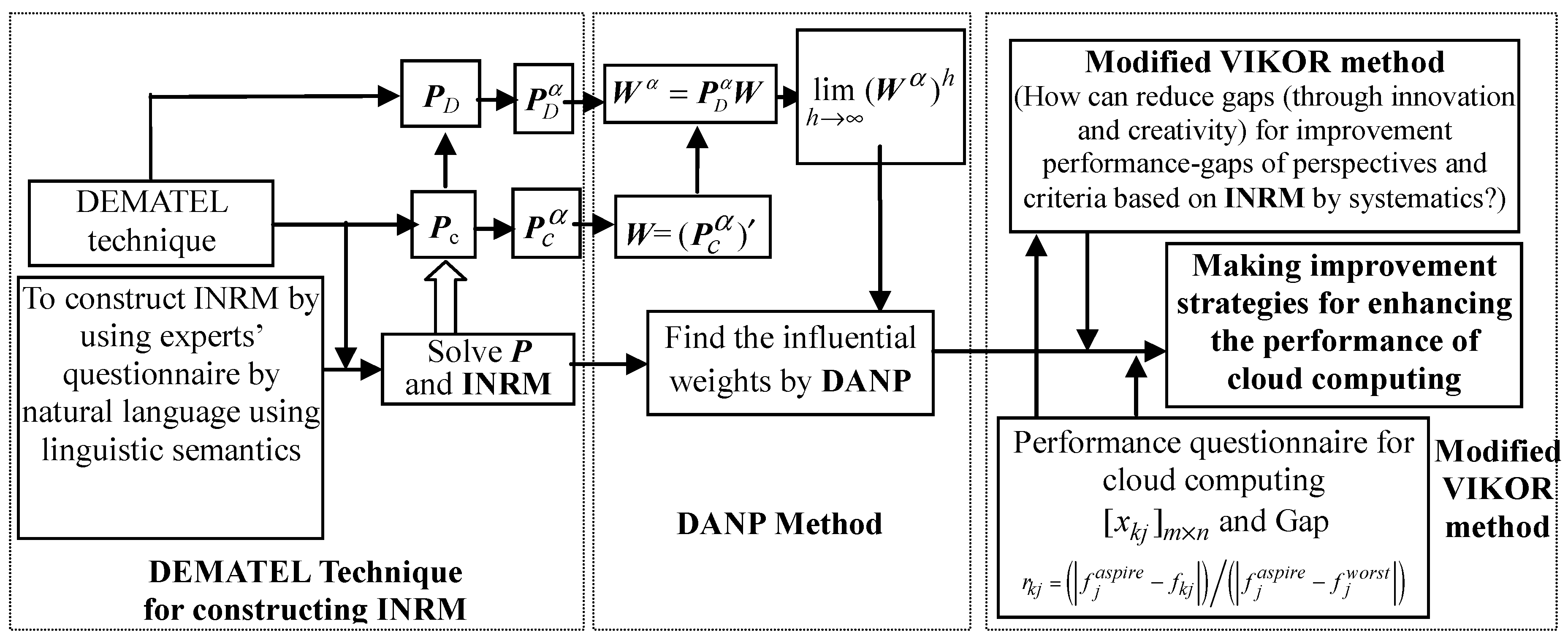
3. Building a New MADM Model to Identify the Key Risk Factors for Application of Cloud Computing in the Auditing
3.1. Building an Influential Network Relation Map by DEMATEL
3.2. Identifying the Weights by DANP
3.3. Measuring the Performance by Modified VIKOR
3.4. Data Collection
4. Empirical Analysis
4.1. Background and Problem Description
4.2. Analysis of Empirical Result
4.2.1. DEMATEL Verification of the Analysis of Interactions between Dimensions and Criteria
4.2.2. Using the DANP to Determine Factor Weight
4.2.3. Implementation Performance of each Dimension and Standard
4.3. Management Implication
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Appendix A. A novel hybrid MADM model combined with DEMATEL, ANP, and modified VIKOR
Appendix A.1. Building an Influential Network Relation Map by DEMATEL
- Step 1:
- Calculate the direct influence-relation average matrix G. Assume the number of experts F and the number of criteria n are asked to propose that the pairwise comparisons between any two criteria are denoted by, and are given, an integer score of 0, 1, 2, 3, or 4, expressing the range from “absolutely no influence (0)” to “very high influence (4)” by natural language in linguistics (e.g., semantics), and showing the degree that each criterion i affects each criterion j. The answers by each expert form a n × n non-negative matrix where are the answer matrices by the P experts in practical experience, and the elements of are denoted by from expert p. Thus, an n × n average matrix P of all experts given can be built by Equation (A1):The average scores of the P experts are . The average matrix is called the initial direct relation matrix G, and represents the degree of influence one criterion exerts on another, as well as the degree of influence it receives from other criteria.
- Step 2:
- Normalize the initial direct-influence relation matrix. The normalized initial direct influence relation matrix Z is acquired by normalizing the average matrix G. The matrix Z is easily derived from Equations (A2) and (A3), whereby all principal diagonal criteria are equal to zero:
- Step 3:
- Derive the total influence-relation matrix. A continuous decrease of the indirect effects of problems moves with the powers of the matrix Z, e.g., and for , where is a unit matrix. The total influence relation matrix P is a matrix, and is defined by as shown in Equation (A4):The total influence relation matrix P of INRM can be acquired by Equation (A4). Equations (A5) and (A6) are used to generate each row sum and column sum in the matrix P, respectively:where di is the sum of a row in the total influence relation matrix P, which represents the total effects (both direct and indirect) of criterion/perspective i on the all other criteria/perspectives . Similarly, rj is the column sum in the total influence relation matrix P, which represents the total effects (both direct and indirect) of criterion/perspective j received from the all other criteria/perspectives . Thus, when i = j, offers an index of the strength of the total influences given and received, that is indicates the degree of importance that criterion/perspective i plays in the system. In addition, provides an index of the degree of the cause of total influence. If is positive, then criterion/perspective i is a net causer, and if is negative, then criterion/perspective i is a net receiver.
Appendix A.2. Based on the DEMATEL Technique to Find the Influential Weights of DANP
- Step 4:
- Find the normalized total influence relation matrix Pc. DEMATEL is used to build total influence relation matrix from each perspective (dimension or cluster), with different degrees of influence relation for the criteria, as shown in Equation (A7):where is the nth cluster; is the mth criterion in the nth dimension; and is a submatrix of the influence relation by the criteria from a comparison of the ith dimension and the jth dimension. In addition, if the ith dimension has no influence on the jth dimension, then submatrix , shows independence (no influence relation) in each other criterion.
- Step 5:
- Form an un-weighted super-matrix . Normalize the total influence relation matrix as shown in Equation (A8):where denotes the normalizing total influence relation matrix, and is derived from Equations (A9) and (A10). Similarly, can be obtained:According to the pair-wise comparisons with the criteria, and based on the basic concept of ANP, the un-weighted super-matrix W can be obtained by transposing the normalized influence-relation matrix by dimensions (clusters), i.e., , as shown in Equation (A11):
- Step 6:
- Obtain the weighted super-matrix . The total influence-relation matrix of dimensions is derived according to the DEMATEL technique, as given by Equation (A12):The normalized total influence-relation matrix of dimensions can be obtained through the total influence-relation matrix divided by , as shown in Equation (A13):The normalized and the un-weighted super-matrix W (shown as Equation (A11)), and the weighted super-matrix (normalized super-matrix) can be easily obtained by Equation (A14):
- Step 7:
- Find the limit super-matrix . Limit the weighted super-matrix by raising it to the kth power, until the super-matrix has converged and become a stable super-matrix. The global priority vectors are obtained, which are called the influential weights of DANP (DEMATEL-based ANP), such as , where z represents any number of power.
Appendix A.3. Measuring the Performance by Modified VIKOR
- Step 1:
- Determine the positive-ideal solution and negative-ideal solution replaced by the aspiration levels and the worst value to fit today’s real world situation. Define the best value (aspiration level) shown as in j criterion and the worst value for all criteria, which can be acquired from the traditional form to the modified form.
- (1)
- Traditional approach for deriving the positive-ideal solution and negative-ideal solution as follows:The positive-ideal solution: where ;The negative-ideal solution: where
- (2)
- The modified approach for replacement by the aspiration level and the worst value, as follows:The aspiration level: , where is an aspiration level; The worst values: , where is a worst value.In this study, the performance range-scores from 0 to 10 (very bad ← 0,1,2,..,9,10 → very good) are used with natural language in the linguistic/semantic questionnaire, thus, the aspiration level takes the highest score of 10 and the worst value takes the value of 0. Hence, is defined as the aspiration level and as the worst value, it can avoid choosing the best among inferior choices/options/alternatives. In other words, it avoids “picking the best apple from a barrel of rotten apples”.
- Step 2:
- Calculate the mean group utility for the gap and maximal gap for prioritizing improvement. These values can be calculated using Equations (A15) and (A16), respectively:where is defined as the normalized ratio of distance to the aspiration level, which implies the synthesized gap for the criteria. On the other hand, is defined as the normalized ratio of distance to the worst value, which implies the maximal gap in j criteria for priority improvement. Here, indicates the influential weights for the criteria obtained from DANP, and indicates the normalized gap of the distance to the aspiration level.
- Step 3:
- Obtain the comprehensive indicator for ranking and selection in the traditional VIKOR approach. The values are given by:where , , , and , where v denotes the weight on the strategy of the maximum group utility, and 1-v is the weight on the individual regret (maximal gap for priority improvement). Therefore, Equation (A17) can be rewritten as in the modified VIKOR to replace the traditional VIKOR approach, when and as well as and are set. If represents only the consideration of the average gap weighting integration, then can be regarded as the maximum gap regarding the improvement priority. Generally speaking, can be set, but can be adjusted depending on expert opinion in the value integration.
References
- Raval, V. Risk landscape of cloud computing. ISACA J. 2010, 1, 26. [Google Scholar]
- Du, H.; Cong, Y. Cloud computing, accounting, auditing, and beyond. CPA J. 2010, 80, 66–70. [Google Scholar]
- Fraser, S. The Risk Based Audit Process. Available online: http://www.charteredaccountants.com.au/ News-Media/Charter/Charter-articles/Audit-and-assurance/2011–07-The-Risk-Based-Audit-Approach.aspx2012 (accessed on 19 August 2016).
- Robson, K.; Humphrey, C.; Khalifa, R.; Jones, J. Transforming audit technologies: Business risk and the audit field. Account. Organ. Soc. 2007, 32, 409–438. [Google Scholar] [CrossRef]
- ISACA, ISACA Issues Four New Audit Programs on Cloud Computing, Crisis Management, Security and Active Directory. Available online: http://www.isaca.org/About-ISACA/Press-room/News-Releases/2010/Pages/ISACA-Issues-Four-New-Audit-Programson-Cloud-Computing-Crisis-Management-Security-and-Active-Directory.aspx2010 (accessed on 18 August 2015).
- Chou, D.C. Cloud computing risk and audit issues. Comput. Stand. Interfaces 2015, 42, 137–142. [Google Scholar] [CrossRef]
- Sookhak, M.; Talebian, H.; Ahmed, E.; Gani, A.; Khan, M.K. A review on remote data auditing in single cloud server: Taxonomy and open issues. J. Netw. Comput. Appl. 2014, 43, 121–141. [Google Scholar] [CrossRef]
- Liou, J.J.H. New concepts and trends of MCDM for tomorrow-in honor of Professor Gwo-Hshiung Tzeng on the occasion of his 70th birthday. Technol. Econ. Dev. Econ. 2013, 19, 367–375. [Google Scholar] [CrossRef]
- Liou, J.J.H.; Tzeng, G.H. Comments on “Multiple criteria decision making (MCDM) methods in economics: An overview”. Technol. Econ. Dev. Econ. 2012, 18, 672–695. [Google Scholar] [CrossRef]
- Liou, J.J.H.; Tamošaitienė, J.; Zavadskas, E.K.; Tzeng, G.H. New hybrid COPRAS-G MADM model for improving and selecting suppliers in green supply chain management. Int. J. Prod. Res. 2016, 54, 114–134. [Google Scholar] [CrossRef]
- Ondrus, J.; Pigneur, Y. Near field communication: An assessment for future payment systems. Inf. Syst. E-Bus. Manag. 2009, 7, 347–361. [Google Scholar] [CrossRef]
- Peng, K.H.; Tzeng, G.H. A hybrid dynamic MADM model for problems-improvement in economics and business. Technol. Econ. Dev. Econ. 2013, 19, 638–660. [Google Scholar] [CrossRef]
- Hwang, C.L.; Yoon, K. Multiple Attribute Decision Making: Methods and Applications a State-of-the-Art Survey; Springer Science & Business Media: New York, NY, USA, 2012. [Google Scholar]
- Bozbura, F.T.; Beskese, A.; Kahraman, C. Prioritization of human capital measurement indicators using fuzzy AHP. Expert Syst. Appl. 2007, 32, 1100–1112. [Google Scholar] [CrossRef]
- Asgari, M.; Abbasi, A. Comparing MADM and artificial neural network methods for evaluating suppliers in multiple sourcing decision. Decis. Sci. Lett. 2015, 4, 193–202. [Google Scholar] [CrossRef]
- Chen, F.H. Application of a hybrid dynamic MCDM to explore the key factors for the internal control of procurement circulation. Int. J. Prod. Res. 2015, 53, 2951–2969. [Google Scholar] [CrossRef]
- Li, X.; Wang, Y.; Chen, X. Cold chain logistics system based on cloud computing. Concurr. Comput. Pract Exp. 2012, 24, 2138–2150. [Google Scholar] [CrossRef]
- Chen, Z.; Yoon, J. IT Auditing to assure a secure cloud computing. In Proceedings of the 2010 IEEE 6th World Congress on Services, Miami, FL, USA, 5–10 July 2010.
- Zhu, Y.; Hu, H.; Ahn, G.J.; Yau, S.S. Efficient audit service outsourcing for data integrity in clouds. J. Syst. Softw. 2012, 85, 1083–1095. [Google Scholar] [CrossRef]
- Lori, M. Data security in the world of cloud computing. IEEE Secur. Priv. 2009, 7, 61–64. [Google Scholar]
- Zissis, D.; Lekkas, D. Addressing cloud computing security issues. Future Gener. Comput. Syst. 2012, 28, 583–592. [Google Scholar] [CrossRef]
- Kim, S.H.; Lee, I.Y. Block access token renewal scheme based on secret sharing in apache hadoop. Entropy 2014, 16, 4185–4198. [Google Scholar] [CrossRef]
- Choudhury, A.J.; Kumar, P.; Sain, M.; Lim, H.; Jae-Lee, H. A strong user authentication framework for cloud computing. In Proceedings of the 2011 IEEE Asia-Pacific Services Computing Conference (APSCC), Jeju, Korea, 12–15 December 2011; pp. 110–115.
- Khorshed, M.T.; Ali, A.B.M.S.; Wasimi, S.A. A survey on gaps, threat remediation challenges and some thoughts for proactive attack detection in cloud computing. Future Gener. Comput. Syst. 2012, 28, 833–851. [Google Scholar] [CrossRef]
- Patel, A.; Taghavi, M.; Bakhtiyari, K.; Júnior, J.C. An intrusion detection and prevention system in cloud computing: A systematic review. J. Netw. Comput. Appl. 2013, 36, 25–41. [Google Scholar] [CrossRef]
- Mansfield-Devine, S. A patchy response: The dangers of not keeping our systems secure. Comput. Fraud Secur. 2015, 2015, 15–20. [Google Scholar] [CrossRef]
- Rasheed, H. Auditing for standards compliance in the cloud: Challenges and directions. In Proceedings of the 2011 international Arab conference on information technology (ACIT 2011), Riyadh, Saudi Arabia, 10–13 December 2011.
- Albanese, M.; Jajodia, S.; Jhawar, R.; Piuri, V. Securing mission-centric operations in the cloud. In Secure Cloud Computing; Springer: New York, NY, USA, 2014; pp. 239–259. [Google Scholar]
- Jincui, C.; Liqun, J. Role-based access control model of cloud computing. Energy Procedia 2011, 13, 1056–1061. [Google Scholar]
- Chen, J.; Wu, G.; Shen, L.; Ji, Z. Differentiated security levels for personal identifiable information in identity management system. Expert Syst. Appl. 2011, 38, 14156–14162. [Google Scholar] [CrossRef]
- Goode, J. The importance of identity security. Comput. Fraud Secur. 2012, 2012, 5–7. [Google Scholar] [CrossRef]
- Liu, Z.; Yan, H.; Li, Z. Server-aided anonymous attribute-based authentication in cloud computing. Future Gener. Comput. Syst. 2015, 52, 61–66. [Google Scholar] [CrossRef]
- Svantesson, D.J.B. Data protection in cloud computing—The Swedish perspective. Comput. Law Secur. Rev. 2012, 28, 476–480. [Google Scholar] [CrossRef]
- Kikuchi, S.; Hiraishi, K. Improving reliability in management of cloud computing infrastructure by formal methods. In Proceedings of the 2014 IEEE Network Operations and Management Symposium (NOMS), Krakow, Poland, 5–9 May 2014.
- Hwang, C.L.; Yoon, K.S. Multiple Attribute Decision Making: Method and Applications; Springer-Verlag: New York, NY, USA, 1981. [Google Scholar]
- Yoon, K.P.; Hwang, C.L. Multiple Attribute Decision Making: An Introduction; Sage Publications: Thousand Oaks, CA, USA, 1995. [Google Scholar]
- Cebi, S. A quality evaluation model for the design quality of online shopping websites. Electron. Commer. Res. Appl. 2013, 12, 124–135. [Google Scholar] [CrossRef]
- Keramati, A.; Shapouri, F. Multidimensional appraisal of customer relationship management: Integrating balanced scorecard and multi criteria decision making approaches. Inf. Syst. E-Bus. Manag. 2016, 14, 217–251. [Google Scholar] [CrossRef]
- Chen, F.H.; Chi, D.J. Application of a new DEMATEL to explore key factors of China’s corporate social responsibility: Evidence from accounting experts. Qual. Quant. 2015, 49, 135–154. [Google Scholar] [CrossRef]
- Saaty, T.L. Decision Making with Dependence and Feedback: The Analytic Network Process: The Organization and Prioritization of Complexity; RWS Publications: Pittsburgh, PA, USA, 1996. [Google Scholar]
- Chen, F.H.; Tzeng, G.H.; Chang, C.C. Evaluating the enhancement of corporate social responsibility websites quality based on a new hybrid MADM model. Int. J. Inf. Technol. Decis. Mak. 2015, 14, 697–724. [Google Scholar] [CrossRef]
- Lee, W.H.; Hwang, K.P.; Lin, W.J.; Shieh, J.L. An analysis of trusted service manager development modes by mobile operating system designers in Taiwan. Electron. Commer. Res. Appl. 2015, 14, 592–602. [Google Scholar] [CrossRef]
- Opricovic, S. Multicriteria Optimization of Civil Engineering Systems. Fac. Civ. Eng. Belgrade 1998, 2, 5–21. [Google Scholar]
- Opricovic, S.; Tzeng, G.H. Extended VIKOR method in comparison with outranking methods. Eur. J. Oper. Res. 2007, 178, 514–529. [Google Scholar] [CrossRef]
- Saaty, T.L. The Analytic Hierarchy Process; McGraw-Hill: New York, NY, USA, 1980. [Google Scholar]
- Li, H.; King, G.; Ross, M.; Staples, G. BS7799: A suitable model for information security management. In Proceedings of the Americas Conference on Information Systems (AMCIS), California, CA, USA, 13–15 August 2000.
- Calder, A. ISO27001/ISO27002: A Pocket Guide; IT Governance: Cambridgeshire, UK, 2013. [Google Scholar]
- Ruan, K.; Carthy, J. Cloud computing reference architecture and its forensic implications: A preliminary analysis. In Digital Forensics and Cyber Crime; Springer: Berlin/Heidelberg, Germany, 2013; pp. 1–21. [Google Scholar]
- Pearson, S. Taking account of privacy when designing cloud computing services. In Proceedings of the 2009 ICSE Workshop on Software Engineering Challenges of Cloud Computing; IEEE Computer Society: Washington, DC, USA, 2009; pp. 44–52. [Google Scholar]
- Scarfone, K. Guide to Security for Full Virtualization Technologies; DIANE Publishing: Collingdale, PA, USA, 2011. [Google Scholar]
- Kepczyk, R.H. Remote access cloud hosting options for CPA firms. CPA Pract. Manag. Forum 2011, 7, 10–13. [Google Scholar]
- Wu, L.; Buyya, R. Service Level Agreement (SLA) in Utility Computing Systems; IGI Global: Hershey, PA, USA, 2010. [Google Scholar]
- Cloud computing security considerations, Intelligence and security. Australian Government Department of Defence. Available online: http://www.asd.gov.au/publications/protect/cloud_computing_security_considerations.htm (accessed on 18 August 2016).
- Allen, M.J. Cloud computing heavenly solution or pie in the sky? Pa. CPA J. 2011, 82, 1–4. [Google Scholar]
- Badger, L.; Grance, T.; Patt-Corner, R.; Voas, J. Draft Cloud Computing Synopsis and Recommendations; NIST special publication: Washington, DC, USA, 2011. [Google Scholar]
- Hogan, M.; Liu, F.; Sokol, A.; Tong, J. Nist Cloud Computing Standards Roadmap; NIST Special Publication: Gaithersburg, MD, USA, 2011. [Google Scholar]
- Pan, L.; Wang, D. A cross-entropy-based admission control optimization approach for heterogeneous virtual machine placement in public clouds. Entropy 2016, 18, 95. [Google Scholar] [CrossRef]
- Duffy, H. How “cloud-ready” is your firm? CPA Pract. Manag. Forum 2012, 8, 5–6. [Google Scholar]
- Lu, M.T.; Hu, S.K.; Huang, L.H.; Tzeng, G.H. Evaluating the implementation of business-to-business m-commerce by SMEs based on a new hybrid MADM model. Manag. Decis. 2015, 3, 290–317. [Google Scholar] [CrossRef]
- Liou, J.J.H.; Chuang, Y.H.; Tzeng, G.H. A fuzzy integral-based model for supplier evaluation and improvement. Inf. Sci. 2014, 266, 199–217. [Google Scholar] [CrossRef]

| Perspectives (Dimensions) | |||
|---|---|---|---|
| Protection system | Technology risks | Automating user provisioning | Operations |
| Approval layers and controls Tangible and intangible security Network connection and data transmission Authentication method and authorization system Prevent intrusion Chain of custody process | Patchy response Supervisor Segregation of duties Software monitoring technology | Access rights administration Removal of entrance Periodic inspection of access Data backup Data recovery | Private laws Incident management Undesirable event management Service resilience Reliability and availability Supervision and management function |
| Dimensions/Criteria | Descriptions | References |
|---|---|---|
| Protection system (A) | ||
| Tangible and intangible security () | Use information assets, systems and peripherals for infrastructure and set necessary restrictions for security purposes. | [46,47,48] |
| Network connection and data transmission () | Use Internet connection and data transfer process to ensure data accuracy and authenticity | [21,46] |
| Authentication method and authorization system () | Before accessing data, users are required to verify personal password and authorized data. | [23,49] |
| Prevent intrusion () | Centralized management model provides all-weather monitoring network and analyzes intrusions. | [24,25] |
| Technology risks (B) | ||
| Patchy response () | Programs are repaired by software providers when attacked by malwares. | [26,28,48,50] |
| Supervisor () | Top management or highly authorized users. | [29] |
| Segregation of duties () | Avoid unauthorized access or excessive authorization to ensure that customer information are fully protected and not used by other customers. | [29] |
| Automating user provisioning (C) | ||
| Access rights administration () | To read or write system files, or be read or written, permission must be granted to change and obtain authorization. | [46,48,50] |
| Removal of entrance () | Remove access authorization of former employees and those in violation of level authorization. | [48] |
| Periodic inspection of access () | Periodic testing of identity management system to detect damage and ensure access security. | [30,31] |
| Operations (D) | ||
| Private laws () | Regulate customer data collection, processing and use to avoid infringement of personal rights and promote appropriate use of personal information. | [33,49] |
| Incident management () | Information log for operational errors due to incomplete information and hacked important information. | [44,46,51] |
| Undesirable event management () | Timely assistance by providers to resolve any information problems and failure. | [44,46,51] |
| Service resilience () | Simple and succinct to avoid being burdened by excessive details when updating. | [46] |
| Reliability and availability () | Authorized users can access needed information anytime and anywhere. | [34,52] |
| Perspectives | A | B | C | D | Row Sum () | Column Sum () | ||
|---|---|---|---|---|---|---|---|---|
| A | 0.8241 | 0.8330 | 0.8257 | 0.8210 | 3.064 | 3.306 | 6.370 | −0.242 |
| B | 0.7595 | 0.7650 | 0.7537 | 0.7542 | 2.979 | 3.316 | 6.114 | −0.157 |
| C | 0.8247 | 0.8314 | 0.8244 | 0.8042 | 3.067 | 3.215 | 6.282 | −0.148 |
| D | 0.7541 | 0.8312 | 0.8227 | 0.8070 | 2.995 | 1.307 | 4.302 | 1.688 |
| Criteria | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0.714 | 0.830 | 0.861 | 0.845 | 0.759 | 0.787 | 0.808 | 0.808 | 0.802 | 0.793 | 0.712 | 0.796 | 0.783 | 0.771 | 0.726 | |
| 0.805 | 0.799 | 0.894 | 0.883 | 0.807 | 0.820 | 0.840 | 0.845 | 0.837 | 0.831 | 0.727 | 0.824 | 0.813 | 0.803 | 0.754 | |
| 0.774 | 0.827 | 0.788 | 0.846 | 0.768 | 0.795 | 0.816 | 0.814 | 0.808 | 0.790 | 0.703 | 0.795 | 0.776 | 0.767 | 0.723 | |
| 0.798 | 0.861 | 0.877 | 0.799 | 0.788 | 0.804 | 0.824 | 0.833 | 0.826 | 0.821 | 0.716 | 0.824 | 0.806 | 0.794 | 0.748 | |
| 0.734 | 0.796 | 0.807 | 0.796 | 0.667 | 0.740 | 0.759 | 0.765 | 0.754 | 0.754 | 0.662 | 0.757 | 0.744 | 0.736 | 0.695 | |
| 0.786 | 0.846 | 0.865 | 0.847 | 0.764 | 0.732 | 0.825 | 0.831 | 0.824 | 0.804 | 0.709 | 0.803 | 0.785 | 0.782 | 0.727 | |
| 0.789 | 0.843 | 0.871 | 0.851 | 0.756 | 0.799 | 0.754 | 0.831 | 0.823 | 0.807 | 0.712 | 0.805 | 0.792 | 0.785 | 0.733 | |
| 0.804 | 0.866 | 0.891 | 0.876 | 0.782 | 0.813 | 0.837 | 0.777 | 0.841 | 0.827 | 0.737 | 0.818 | 0.801 | 0.805 | 0.766 | |
| 0.763 | 0.820 | 0.848 | 0.833 | 0.748 | 0.778 | 0.798 | 0.806 | 0.731 | 0.792 | 0.697 | 0.775 | 0.761 | 0.758 | 0.711 | |
| 0.799 | 0.864 | 0.886 | 0.879 | 0.793 | 0.816 | 0.836 | 0.839 | 0.833 | 0.762 | 0.734 | 0.822 | 0.811 | 0.806 | 0.760 | |
| 0.816 | 0.863 | 0.887 | 0.874 | 0.796 | 0.816 | 0.841 | 0.853 | 0.842 | 0.829 | 0.679 | 0.831 | 0.812 | 0.809 | 0.760 | |
| 0.784 | 0.846 | 0.871 | 0.859 | 0.786 | 0.793 | 0.817 | 0.821 | 0.812 | 0.807 | 0.720 | 0.748 | 0.805 | 0.798 | 0.752 | |
| 0.769 | 0.826 | 0.857 | 0.847 | 0.772 | 0.782 | 0.805 | 0.811 | 0.804 | 0.800 | 0.713 | 0.807 | 0.723 | 0.782 | 0.733 | |
| 0.762 | 0.821 | 0.843 | 0.838 | 0.759 | 0.777 | 0.801 | 0.805 | 0.797 | 0.789 | 0.700 | 0.794 | 0.778 | 0.709 | 0.727 | |
| 0.706 | 0.759 | 0.768 | 0.764 | 0.697 | 0.714 | 0.731 | 0.735 | 0.727 | 0.727 | 0.649 | 0.737 | 0.723 | 0.711 | 0.613 |
| Perspectives/Criteria | Row Sum (di) | Column Sum (ri) | di + ri | di – ri | Order |
|---|---|---|---|---|---|
| Protection system (A) | 3.064 | 3.306 | 6.370 | −0.242 | |
| Tangible and intangible security (a1) | 3.250 | 3.090 | 6.340 | 0.160 | 1 |
| Network connection and data transmission (a2) | 3.380 | 3.317 | 6.697 | 0.063 | 2 |
| Authentication method and authorization system (a3) | 3.235 | 3.420 | 6.655 | −0.185 | 4 |
| Prevent intrusion (a4) | 3.334 | 3.372 | 6.706 | −0.038 | 3 |
| Technology risks (B) | 2.979 | 3.136 | 6.114 | −0.157 | |
| Patchy response (b1) | 2.166 | 2.187 | 4.353 | −0.021 | 2 |
| Supervisor (b2) | 2.321 | 2.271 | 4.592 | 0.050 | 1 |
| Segregation of duties (b3) | 2.309 | 2.338 | 4.647 | −0.029 | 3 |
| Automating user provisioning (C) | 3.067 | 3.215 | 6.282 | −0.148 | |
| Access rights administration (c1) | 2.445 | 2.423 | 4.868 | 0.022 | 2 |
| Removal of entrance (c2) | 2.330 | 2.405 | 4.735 | −0.075 | 3 |
| Periodic inspection of access (c3) | 2.434 | 2.382 | 4.816 | 0.052 | 1 |
| Operations (D) | 2.995 | 1.307 | 4.302 | 1.688 | |
| Privacy laws (d1) | 3.890 | 3.461 | 7.351 | 0.429 | 1 |
| Incident Management (d2) | 3.822 | 3.917 | 7.739 | −0.095 | 3 |
| Undesirable event management (d3) | 3.758 | 3.840 | 7.598 | −0.082 | 2 |
| Service resilience (d4) | 3.707 | 3.809 | 7.516 | −0.102 | 4 |
| Reliability and availability (d5) | 3.433 | 3.585 | 7.018 | −0.152 | 5 |
| Criteria | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0.220 | 0.238 | 0.239 | 0.239 | 0.234 | 0.235 | 0.235 | 0.234 | 0.234 | 0.233 | 0.237 | 0.233 | 0.233 | 0.234 | 0.236 | |
| 0.255 | 0.236 | 0.256 | 0.258 | 0.254 | 0.253 | 0.251 | 0.252 | 0.251 | 0.252 | 0.251 | 0.252 | 0.250 | 0.252 | 0.253 | |
| 0.265 | 0.264 | 0.244 | 0.263 | 0.258 | 0.259 | 0.260 | 0.259 | 0.260 | 0.259 | 0.258 | 0.259 | 0.260 | 0.258 | 0.256 | |
| 0.260 | 0.261 | 0.261 | 0.240 | 0.254 | 0.253 | 0.254 | 0.255 | 0.255 | 0.256 | 0.254 | 0.256 | 0.257 | 0.257 | 0.255 | |
| 0.323 | 0.327 | 0.323 | 0.326 | 0.308 | 0.329 | 0.327 | 0.322 | 0.322 | 0.325 | 0.324 | 0.328 | 0.327 | 0.325 | 0.325 | |
| 0.334 | 0.332 | 0.334 | 0.333 | 0.342 | 0.316 | 0.346 | 0.334 | 0.335 | 0.334 | 0.333 | 0.331 | 0.331 | 0.332 | 0.333 | |
| 0.343 | 0.340 | 0.343 | 0.341 | 0.351 | 0.355 | 0.327 | 0.344 | 0.344 | 0.342 | 0.343 | 0.341 | 0.341 | 0.343 | 0.341 | |
| 0.336 | 0.336 | 0.338 | 0.336 | 0.337 | 0.338 | 0.338 | 0.318 | 0.346 | 0.345 | 0.338 | 0.337 | 0.336 | 0.337 | 0.336 | |
| 0.334 | 0.333 | 0.335 | 0.333 | 0.332 | 0.335 | 0.334 | 0.344 | 0.314 | 0.342 | 0.334 | 0.333 | 0.333 | 0.333 | 0.332 | |
| 0.330 | 0.331 | 0.328 | 0.331 | 0.332 | 0.327 | 0.328 | 0.338 | 0.340 | 0.313 | 0.328 | 0.331 | 0.331 | 0.330 | 0.332 | |
| 0.188 | 0.185 | 0.187 | 0.184 | 0.184 | 0.186 | 0.186 | 0.188 | 0.188 | 0.187 | 0.174 | 0.188 | 0.190 | 0.189 | 0.189 | |
| 0.210 | 0.210 | 0.211 | 0.212 | 0.211 | 0.211 | 0.210 | 0.208 | 0.209 | 0.209 | 0.214 | 0.196 | 0.215 | 0.214 | 0.215 | |
| 0.207 | 0.207 | 0.206 | 0.207 | 0.207 | 0.206 | 0.207 | 0.204 | 0.206 | 0.206 | 0.209 | 0.211 | 0.192 | 0.210 | 0.211 | |
| 0.204 | 0.205 | 0.204 | 0.204 | 0.205 | 0.205 | 0.205 | 0.205 | 0.205 | 0.205 | 0.208 | 0.209 | 0.208 | 0.191 | 0.207 | |
| 0.192 | 0.192 | 0.204 | 0.192 | 0.193 | 0.191 | 0.191 | 0.195 | 0.192 | 0.193 | 0.195 | 0.197 | 0.195 | 0.196 | 0.179 |
| Criteria | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0.060 | 0.066 | 0.066 | 0.066 | 0.066 | 0.066 | 0.066 | 0.066 | 0.066 | 0.065 | 0.066 | 0.065 | 0.065 | 0.065 | 0.066 | |
| 0.070 | 0.065 | 0.070 | 0.071 | 0.071 | 0.071 | 0.070 | 0.071 | 0.070 | 0.071 | 0.070 | 0.070 | 0.070 | 0.070 | 0.071 | |
| 0.073 | 0.073 | 0.067 | 0.072 | 0.072 | 0.073 | 0.073 | 0.073 | 0.073 | 0.073 | 0.072 | 0.072 | 0.073 | 0.072 | 0.072 | |
| 0.072 | 0.072 | 0.071 | 0.066 | 0.071 | 0.071 | 0.071 | 0.072 | 0.072 | 0.072 | 0.071 | 0.071 | 0.072 | 0.072 | 0.071 | |
| 0.065 | 0.066 | 0.065 | 0.065 | 0.060 | 0.064 | 0.064 | 0.064 | 0.064 | 0.065 | 0.065 | 0.065 | 0.065 | 0.065 | 0.065 | |
| 0.067 | 0.067 | 0.066 | 0.067 | 0.066 | 0.061 | 0.067 | 0.067 | 0.067 | 0.067 | 0.066 | 0.066 | 0.066 | 0.066 | 0.066 | |
| 0.069 | 0.068 | 0.069 | 0.068 | 0.068 | 0.069 | 0.063 | 0.069 | 0.069 | 0.068 | 0.068 | 0.068 | 0.068 | 0.068 | 0.068 | |
| 0.069 | 0.069 | 0.068 | 0.069 | 0.069 | 0.069 | 0.069 | 0.063 | 0.069 | 0.069 | 0.069 | 0.069 | 0.069 | 0.069 | 0.068 | |
| 0.068 | 0.068 | 0.068 | 0.068 | 0.068 | 0.069 | 0.069 | 0.069 | 0.063 | 0.068 | 0.068 | 0.068 | 0.068 | 0.068 | 0.068 | |
| 0.067 | 0.068 | 0.067 | 0.068 | 0.068 | 0.067 | 0.067 | 0.068 | 0.068 | 0.063 | 0.067 | 0.067 | 0.068 | 0.067 | 0.068 | |
| 0.060 | 0.059 | 0.060 | 0.059 | 0.059 | 0.060 | 0.060 | 0.060 | 0.060 | 0.060 | 0.055 | 0.060 | 0.060 | 0.060 | 0.060 | |
| 0.067 | 0.067 | 0.067 | 0.068 | 0.067 | 0.068 | 0.067 | 0.067 | 0.067 | 0.067 | 0.068 | 0.062 | 0.068 | 0.068 | 0.068 | |
| 0.066 | 0.066 | 0.066 | 0.066 | 0.066 | 0.066 | 0.066 | 0.065 | 0.066 | 0.066 | 0.066 | 0.067 | 0.061 | 0.067 | 0.067 | |
| 0.065 | 0.066 | 0.065 | 0.065 | 0.066 | 0.066 | 0.066 | 0.066 | 0.066 | 0.066 | 0.066 | 0.066 | 0.066 | 0.061 | 0.066 | |
| 0.061 | 0.062 | 0.065 | 0.062 | 0.062 | 0.061 | 0.061 | 0.062 | 0.061 | 0.062 | 0.062 | 0.062 | 0.062 | 0.062 | 0.057 |
| Criteria | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Weights (DANP) | 0.0653 | 0.0701 | 0.0721 | 0.0710 | 0.0643 | 0.0661 | 0.0680 | 0.0685 | 0.0678 | 0.0672 | 0.0595 | 0.0671 | 0.0659 | 0.0653 | 0.0617 |
| Dimensions/Criteria | Local Weights | Global Weights (by DANP) | Performance | Relative Gaps |
|---|---|---|---|---|
| Protection system (A) | 0.279 | 0.123 | 7.471 | 0.253 |
| Tangible and intangible security (a1) | 0.234 | 0.065 | 6.967 | 0.303 |
| Network connection and data transmission (a2) | 0.252 | 0.070 | 7.133 | 0.287 |
| Authentication method and authorization system (a3) | 0.259 | 0.072 | 7.800 | 0.220 |
| Prevent intrusion (a4) | 0.255 | 0.071 | 7.933 | 0.207 |
| Technology risks (B) | 0.199 | 0.123 | 7.440 | 0.256 |
| Patchy response (b1) | 0.324 | 0.064 | 7.800 | 0.220 |
| Supervisor (b2) | 0.333 | 0.066 | 7.233 | 0.277 |
| Segregation of duties (b3) | 0.343 | 0.068 | 7.300 | 0.270 |
| Automating user provisioning (C) | 0.203 | 0.123 | 7.899 | 0.210 |
| Access rights administration (c1) | 0.337 | 0.069 | 7.767 | 0.223 |
| Removal of entrance (c2) | 0.333 | 0.068 | 7.800 | 0.220 |
| Periodic inspection of access (c3) | 0.330 | 0.067 | 8.133 | 0.187 |
| Operations (D) | 0.320 | 0.123 | 7.644 | 0.236 |
| Privacy laws (d1) | 0.186 | 0.060 | 8.333 | 0.167 |
| Incident Management (d2) | 0.210 | 0.067 | 7.433 | 0.257 |
| Undesirable event management (d3) | 0.206 | 0.066 | 7.367 | 0.263 |
| Service resilience (d4) | 0.205 | 0.065 | 7.367 | 0.263 |
| Reliability and availability (d5) | 0.193 | 0.062 | 7.800 | 0.220 |
| Total performances | - | - | 7.607 | - |
| Total gap (Sk) | - | - | - | 0.239 |
| Items | Strategy (Sequence of Improvement Priority) |
|---|---|
| F1: Influential network of dimensions of DEMATEL | D _ C _ B _ A |
| F2: Influential network of criteria within individual dimensions | D: (d1) _ (d3) _ (d2) _ (d4) _ (d5) (d3) _ (d2) _ (d4) _ (d5) (d2) _ (d4) _ (d5) (d4) _ (d5) C: (c3) _ (c1) _ (c2) (c1) _ (c2) B: (b2) _ (b1) _ (b3) (b1) _ (b3) A: (a1) _ (a2) _ (a4) _ (a3) (a2) _ (a4) _ (a3) (a4) _ (a3) |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hu, K.-H.; Chen, F.-H.; We, W.-J. Exploring the Key Risk Factors for Application of Cloud Computing in Auditing. Entropy 2016, 18, 401. https://doi.org/10.3390/e18080401
Hu K-H, Chen F-H, We W-J. Exploring the Key Risk Factors for Application of Cloud Computing in Auditing. Entropy. 2016; 18(8):401. https://doi.org/10.3390/e18080401
Chicago/Turabian StyleHu, Kuang-Hua, Fu-Hsiang Chen, and Wei-Jhou We. 2016. "Exploring the Key Risk Factors for Application of Cloud Computing in Auditing" Entropy 18, no. 8: 401. https://doi.org/10.3390/e18080401





