1. Introduction
Two-way quantum key distribution (QKD) schemes have evolved from a theoretic framework in the context of deterministic schemes to experimental realizations for QKD purposes [
1]. The protocol is described by a qubit being sent from one party, say, Bob, to another, Alice, for her encoding before being sent back to him for a measurement to ascertain Alice’s encoding. Standing in stark contrast to BB84 like prepare and measure schemes where information encoding is simply in the choice of states and bases of qubits to be sent from the encoding party to the receiver [
2], the case for two-way QKDs is really in the choice of unitary transformations by an encoding party that would act on the qubits traveling to and fro between the legitimate parties. This naturally makes use of the quantum channel twice. Another peculiarity of the above-mentioned two-way protocols would be how its security is to be ensured. The protocols’ runs are divided into two modes, namely the encoding mode (EM) where message encoded by Alice is followed by measurements by Bob for decoding purposes and the control mode (CM) where Alice would make projective measurements in randomly selected bases such that when the bases coincide with Bob’s then errors can be ascertained. The distribution of the EM and CM would be determined by a factor
c, with 0
< c < 1,
i.e., the probability of Alice randomly choosing an EM. While messages (bits of raw key) are transmitted via the EM, CM has the critical role of estimating the amount of errors in the channels to ascertain Eve’s information gain.
However, despite its early introduction in 2002 [
3], and varying versions that followed, it was only about a decade later that a proper proof for one specific two-way protocol was found for unconditional security in [
4] and a proof for a purified version was reported in [
5]. In [
4], the proof was done for the specific case of non-entangled qubits in one of four states coming from two mutually unbiased bases (this protocol has been referred to as LM05 [
6] and we shall refer to it as such hereafter). In [
5], a purification of two two-way QKD protocol, namely the Super Dense Coding scheme (SDC) and LM05 was done in order to provide a security proof.
Unconditional security proofs provide for an information theoretic security picture of QKD. However, a very important fact that sets constraints within the operational context would be the issue of how such proofs are based on asymptotic analysis that holds true only for infinitely long keys; the concern regarding the security nature of realistic keys, which are finitely long, becomes evident. This has spurred a number of studies including [
7–
9].
The central feature of this work is a review of the security analysis done based on protocol purifications in [
5] and a natural generalization to the the case for finite sized keys. We begin with a quick description of two most relevant two-way QKD protocols followed by their purifications. After a brief on smooth entropies and its application to deriving finite key rates, we provide finite secure key rates in terms of efficiency for both protocols. These will then be compared to an asymmetrical BB84; essentially a BB84 protocol with one basis preferred over another mainly for a more efficient scenario compared to a standard BB84 where choices of bases are equiprobable [
8,
10].
2. Two-Way Protocols
The SDC protocol in some sense is closer to the earlier instances of two-way protocols, namely the Ping-Pong [
3] and more specifically its improved version [
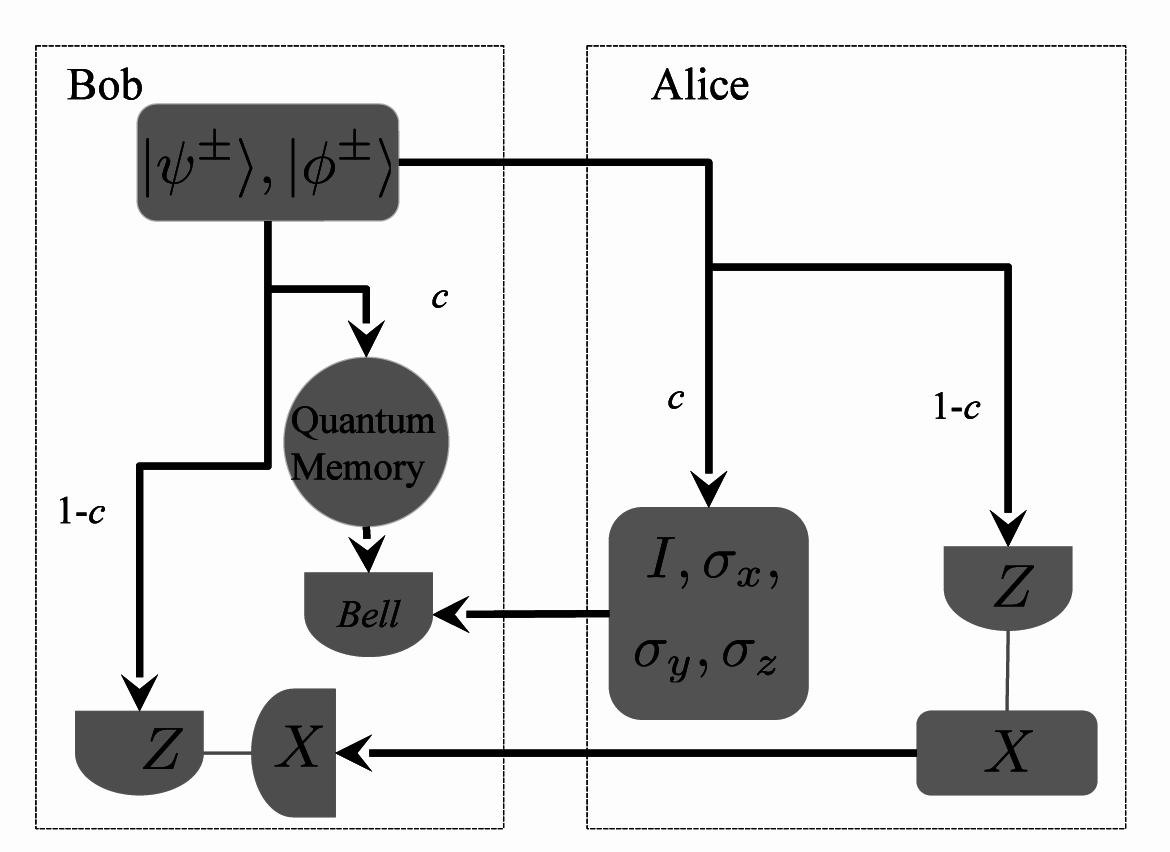
11] which provides for a higher protocol capacity in terms of the number of classical bits encoded in each EM run. It is however more resource demanding as it requires the use of a quantum memory on Bob’s side. Our description of SDC here follows closely that of [
5]. Very simply, the SDC protocol sees Bob sending half a Bell pair to Alice (while storing the other half in a quantum memory) for her to encode by virtue of a randomly chosen unitary transformation from the set containing the identity operator and the three Pauli operators, {
I, σx, σy, σz}. She would subsequently submit the qubit back to Bob for measurements. Alternatively, she could measure the received qubit in the
Z basis and prepare another in the
X basis to be sent to Bob. The former process, done with probability
c ≈ 1, corresponds to her actions in EM, while the latter, done with probability 1 −
c, corresponds to CM. Despite the use of 4 unitaries imply a larger alphabet used, particularly elements of ℤ
4 0, 1, 2, 3 mapped to
I, σx, σy, σz respectively as opposed to bits for encoding, Alice could in fact assign logical bits (in pairs) 00, 10, 11 and 01 to the unitaries. However the mapping
to bits should be done only at the end of the protocol to avoid any possibility of Eve capitalizing on the correlation of bits given any pair [
12].
Bob, on the other hand would, with a probability
c make a Bell measurement and with probability 1−
c measure his stored and received qubit in the
Z and
X basis respectively. A protocol run which sees Bell measurements by Bob coinciding with Alice’s unitary transformations would allow Bob to distinguish between Alice’s unitaries perfectly (given that the Pauli matrices would shift between orthogonal Bell states). Assigning logical symbols 0, 1, 2 and 3 to the Bell states |ψ
+〉, |ψ
−〉, |
ϕ+〉 and |
ϕ−〉 respectively, these instances referred to as EM provide for sharing of a raw key between Alice and Bob. Again, it is possible for Bob to use bits instead when Alice submits the mapping information to Bob at the end of the protocol runs. The instances when Alice’s and Bob’s measurements in the
Z and
X bases coincides would allow for a meaningful CM. Hence a successful EM happens only with probability
c2 and CM happens with probability (1 −
c)
2. A schematic diagram for SDC is illustrated in
Figure 1 below.
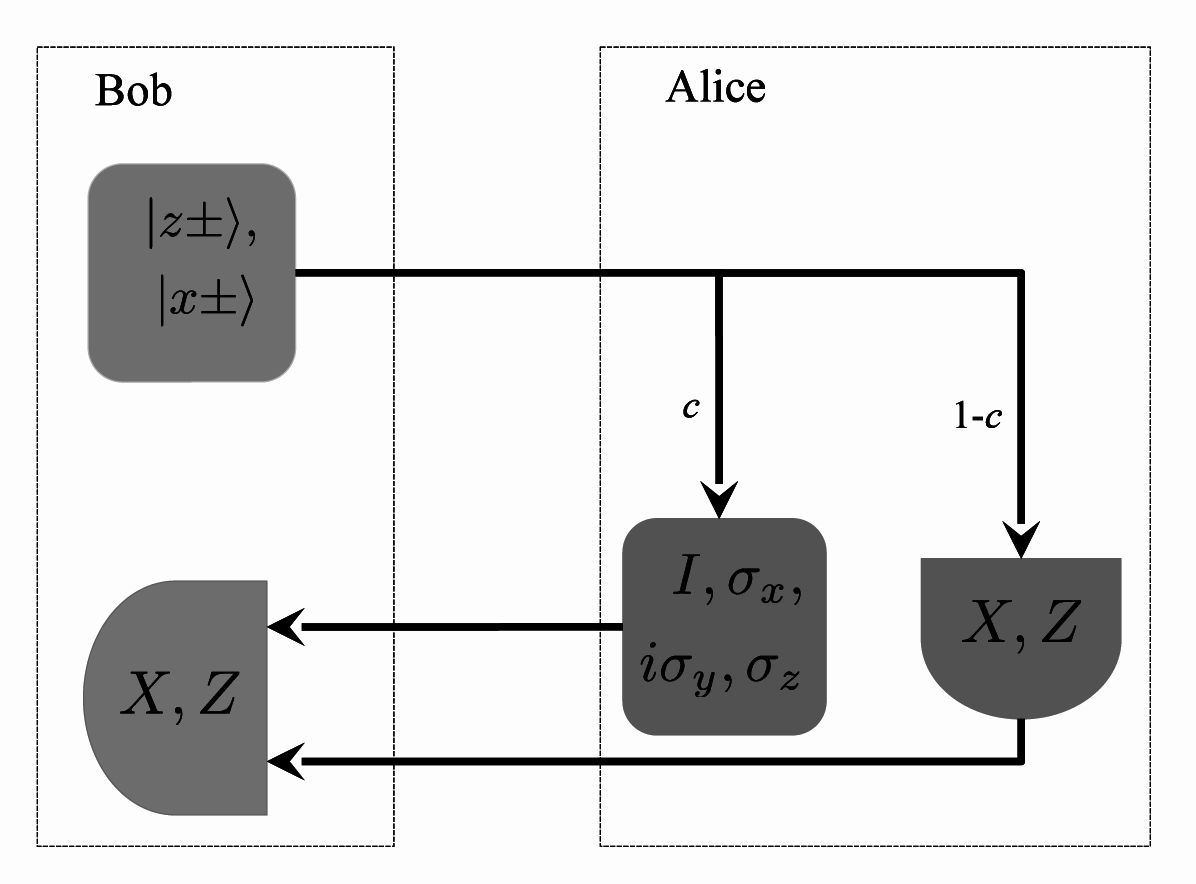
The case for a two-way QKD without using entanglement, namely the LM05, sees a qubit prepared by Bob in a particular bases randomly chosen from either the
X or
Z with probabilities
pX and
pZ respectively to be sent to Alice for her encoding. In the original LM05 protocol, apart from
pX =
pZ, only two unitary transformations were considered, namely the passive
I and
iσy. In [
5], a generalization was made to include another two unitary transformation, namely the
σx and
σz, and the possibility of having different probabilities
pX and
pZ. In this protocol, upon executing her unitary transformation, Alice would resubmit the qubit to Bob who would measure in the same basis he prepared in. Defining the eigenstates of
σz and
σx as |
z±〉 and |
x±〉 respectively, bit values 0 may be assigned to the states |
z+〉 or |
x+〉 and 1 to the states |
z−〉 or |
x−〉. Bob then adds (modulo 2) the bit value corresponding to his prepared state (prior sending to Alice) to the bit value corresponding to his measurement result of the state (after Alice’s encoding). We will mention shortly what Alice needs to do in order to share bit-wise information with Bob. This run of the protocol corresponds to an EM.
With the probability 1 −
c, Alice would make measurements of the qubit she receives instead in either the
Z or
X bases for CM purposes. A schematic diagram for LM05 is shown in
Figure 2 below.
Apart from the use of non entangled qubits by Bob, another obvious difference with the SDC is in the possible options in the post processing feature of the protocols. In SDC, post processing only includes Alice’s and Bob’s discussion to ascertain which signals were to be used for EM and CM purposes apart from error estimations, error corrections and privacy amplifications. In the LM05 on the other hand, Alice and Bob have the option to commit to either direct reconciliation (DR) or reverse reconciliation (RR) which would determine the type of information to be disclosed over an authenticated public channel. In the case of RR, Bob should disclose the bases he prepared and measured qubits in. Using the same assignment of logical bit pairs to unitary transformations as in SDC, Alice would keep only the first bit of the pair when Bob uses Z and the second when Bob uses X. On the other hand, if a RR is considered, then Alice would reveal from which of the two sets, S0 = {I, iσy} and S1 = {σx, σz} was the transformation she had used and only the first bit of the bit pair for each transformation is used. This revelation is necessary given Bob’s measurement in the X basis would give him an erroneous bit when Alice uses S1. In these cases, Bob would need to flip his bit.
2.1. Purifications of Two-Way Protocols
The approach to the security proof presented in [
5] is based on the notion of purification of protocols where the protocols can be described by the measurements made by Alice and Bob on a system provided to them by Eve [
13]. Writing the measurements of Alice and Bob as Probability Operator Value Measure (POVM) maps
and
respectively in EM (or
and
in CM), the state after the measurements is given by
with
i = EM or CM. In the purified version of both the SDC and the LM05 as reported in [
5],
ρABE is a state in the Hilbert space
A ⨂
B ⨂
E (Alice’s, Bob’s and Eve’s respectively) and
A and
B are Hilbert spaces for two qubit systems each. Alice’s measurement
, in EM which acts on a two qubit system must be in such a way that it is equivalent to her encoding operation in the protocols. If we recall how in both protocols, Alice receives a state from Bob and resends after a unitary encoding on the state,
can be understood as a (POVM) acting on the received state with half of some entangled state so as the other half of the entangled state (after the measurement
) is the same as the output from Alice’s encoding to be sent to Bob [
14]. Thus we can imagine
ρABE as that pure state which distributes a pair of qubits to Alice and Bob each. Alice’s measurement on the two received qubits, tr
BE(
ρABE) would ensure that Bob’s measurement,
on his received pair, tr
AE(
ρABE) is equivalent to Alice making a unitary transformation on Bob’s prepared qubit for his subsequent decoding measurement. With regards to Bob’s measurements,
, it is instructive to note that in SDC,
is really the Bell measurement for decoding purposes while in LM05, Bob’s measurement on the first half of tr
AE(
ρABE) effectively prepares the qubit state sent to Alice (in the forward path) while his other measurement is on the other half of tr
AE(
ρABE). The measurements
and
would then correspond to relevant local measurements of each qubit in the qubit pairs in CM (detailed in the ensuing section). Given these, the main ingredient in the security proof for the purified protocols is based on bounding Eve’s information gain given Bob-Alice’s using an uncertainty relation which measures the overlap of Bob’s (Alice’s) measurements,
i.e.,
,
(
,
) in a reverse (direct) reconciliation scenario.
2.2. Measurements and Entropic Uncertainty Relations
Entropic uncertainty relations are used in some security proofs of particular QKD protocols given its power to describe bounds of uncertainty parties may share of a certain quantum system, say
B. In its simplest description, it is simply Heisenberg’s uncertainty principle in an entropic form first proven by [
15]. It was later generalized [
16–
18] to include correlation of the system to be measured with disjoint (possibly quantum) systems
A and
E given by
where
X and
Z are results from POVMs
and ℤ respectively on
B. Writing the POVM elements of
and ℤ as
and
respectively, the term
is given by
Equation (2) together with the Devatak-Winter security bound [
19] is employed in [
5] to provide a security proof for the purified SDC and LM05 protocols. In order to make use of such an entropic relation, [
5] necessarily describes the term
as the (effective) overlap between Bob’s measurements in a RR picture. Given the assumptions in [
5], Bob’s measurements in the purified SDC protocol are either the Bell measurements or a measurement that can be described as
σz ⨂
σx where the overlap between the POVM elements as defined in
Equation (3) is 1/4. This maximal overlap is achieved when considering the overlap between the POVM elements in EM and that of in CM. If we let the measurements by Alice and Bob to result in the strings
and
respectively from EM and
and
respectively from CM, and Eve’s system as
E we can bound Eve’s information based on
Equation (2) as
The key rate of the SDC,
RSDC, is given by the Devetak-Winter rate [
19]
With
upper bounded by
,
by
where
h4 is the 4-ary Shannon entropy and
and
are errors in Alice’s and Bob’s strings in CM and EM respectively, applying the bound of
Equation (4) we arrive at
It is instructive to note that the errors
and
affects a two-bit message transmission resulting from a use of two noisy channels and thus comes as a triple; namely error exclusively in either one channel, say
and
as well as errors in both channels,
for
a = CM, EM. Hence,
It is certainly possible to consider the entropic bounds dictated by the overlap of Alice’s measurements instead of Bob’s as shown above. The key rate would remain the same nonetheless.
A similar line of argument can be applied to the LM05 protocol; though the measurements made for decoding purposes by Bob would be
or
followed by an XOR of the measurements’ results to reveal the encoding done by Alice in the EM. Another set of measurements, which would be useful for the CM would be
or
where the maximal overlap between the POVM elements for measurements made in EM and that in CM is 1/2. Using the relevant entropic bounds (similar to SDC though the overlap is now 1/2 instead of 1/4), the key rate for LM05,
RLM05 can be easily shown to be
where
h2 is the binary Shannon entropy and
qCM and
qEM are the errors in the CM and EM respectively.
The above key rates are derived from inequalities based on terms that are meaningful only within the infinitely long key limits and is thus unsatisfactory from an operational and practical perspective. In the following subsection, we shall review briefly the notion of smooth entropies and relevant entropic bounds that we shall use to derive a finite key rate for SDC and LM05.
2.3. Smooth Entropies and Finite Keys
The smooth entropy is defined based on the conditional entropy. More rigorously, following the definition given in [
20] for a bipartite state
ρBE on
B and
E, the entropy of
B given
E is defined as
where the maximum is taken overall states
σE in
E and
IB is the identity on
B. The
ϵ-smooth min-entropy for
ϵ ≥ 0 is then defined as
with maximization over all bipartite states
ρ on
B and
E with a purified distance [
21] to
ρBE not exceeding
ϵ. The smooth max-entropy is defined as the dual of the smooth min-entropy with regards to any purification of
ρBE.
For the tripartite state
ρABE and POVMs
and ℤ respectively on
B (resulting in bit strings
X and
Z), from [
20], the smooth min-entropy of
X conditioned on
E,
, gives the number of bits contained in
X that are
ϵ-close [
22] to a uniform distribution and independent of
E. The smooth max-entropy of
Z conditioned on
A,
, gives the number of bits needed to reconstruct
Z from
A up to a probability of failure
ϵ and the generalized uncertainty relation involving smooth entropies is given as [
20]
In identifying the measurements and results in both the SDC and LM05 with
Equation (11), similar to the above,
will be identified with Eve’s correlation with Bob’s string (in EM) while
is to be identified with Alice’s and Bob’s in CM. There are two points worth mentioning with regards to the measurements made in CM. The first is in particular reference to LM05’s measurements
and
where a passive operation is noted on the second qubit (received in the backward path). This does not necessarily require Bob to
not measure the qubit in the backward path; rather he could just ignore the measurement made and consider only the result of his first measurement [
23]. In other words, in the cases Alice note a particular round of the protocol is a CM, Bob would ignore the result of his measurement on the second qubit. If it was the EM, then both the measurement results would be XOR-ed for decoding purposes.
The second point is that as the
σz ⨂
σx in SDC and
and
in LM05 happens only in CM, one can see the protocol as analogous to the asymmetrical prepare and measure protocol of BB84 where the measurements in EM is seen as measurements in the preferred basis in the asymmetrical BB84. In the case for the latter, in [
9], where measurements are made in the
X and
Z, a
gedankenexperiment was considered where all measurements were done in the
Z basis to establish an uncertainty relation. Following [
9], in the case for the LM05, we can use the bits derived in the CM to provide for an estimation of the errors in the application of the uncertainty relation using a similar
gedankenexperiment where all rounds are CM; and since Bob can choose to measure for EM, security follows from the notion that the better Alice could estimate Bob’s bits in CM, the worse would Eve’s estimation of Bob’s bits in EM.
3. Efficiency and Secure Key Rates
In what follows, we shall assume implementations of the two-way protocols using depolarizing channels. The depolarizing channel,
is described by the parameter
q, such that 0
≤ q ≤ 1, which affects a quantum state,
ρ independent of the basis as such
For two-way protocols, the use of depolarizing channels can be categorized as either independent or correlated channels. Such a correlation can be understood in terms of the errors estimated in the forward and backward paths in CM against errors in EM. Given bit wise errors
e1 and
e2 in the forward and backward paths respectively, we say the channels are independent provided the errors in EM is given by
em =
e1(1 −
e2) +
e2(1 −
e1). Otherwise they are correlated [
24]. While the case for independent channels are unique by definition, the cases for correlated channels can be infinitely many. However, we shall only consider, as in [
5] correlated channels where
e1 =
e2 =
em.
To ascertain a finite key rate for the two-way protocols given such implementation, we need to determine the distribution of finite number of bits between the EM and the CM. Choices of the value of
c for both protocols would determine this and ultimately how much of a key rate one can have. Hence, in order to determine the optimal value for
c, assuming one has a value of
k for bits in CM and
n in EM (more precisely the cases where Alice’s encoding measurements coincide with Bob’s decoding measurements), the total number qubits,
M(
n, k) sent [
25] before
n bits are derived from EM and
k for CM estimation can be made is given by probability value
. This is immediately derived from modelling the protocol based on [
9].
Subsequently, the already mentioned
gedankenexperiment will provide for an uncertainty relation of
Equation (11) and the smooth-max entropy term for an
n-bit string,
Z given
C,
would be upper bounded by
nh2(
Q +
μ(
n, k)) where
with the strings
Z and
C derived from CM differing at
Q bits. The parameter
ϵS > 0 is a security parameter as defined in [
9].
Strings shared between Alice and Bob in the EM, which one party’s may be characterized as having errors
e relative to the other need be subjected to an error correction procedure. This can conventionally be understood as the amount of pre shared secret bits invested in the communications for error correction purposes [
26].
The Leftover Hashing Lemma [
27] then provides for the length of the secret key as
which is 2
ϵ close to a bit string which is uniform and independent of Eve’s knowledge.
The efficiency of the protocol,
ε can be defined based on the amount of resources in terms of number of qubits required,
It should be noted that for SDC, a factor of 2 should be further multiplied to the denominator reflecting the use of entangled pairs. As in [
9], we do not include any classical bits necessary in the protocol unlike [
28].
3.1. Finite Key Analysis for SDC
We let a total of 2
M(
n, k) pairs of qubits travel to and fro between Bob and Alice with the latter committing to encoding with probability
c. Thus one gets
n amount of quaternary digits from the EM. Following earlier notation, the
n quaternary strings of Alice and Bob are
and
respectively while the
k quaternary strings derived from the CM are
and
respectively. Considering a
gedankenexperiment where all runs are CM lets us bound Eve’s information on the
n quaternary string using
Equation (11) as
The term
is the smooth min-entropy of
conditioned on
E. It reflects Eve’s correlation with Bob’s string in the EM giving the number of bits contained in
that are
ϵ-close to a uniform distribution and independent of
E. In ascertaining the term
reflecting the correlation between Bob’s and Alice’s strings, the case for two way channels with depolarization
q each allows us to consider bit error rate in qubit measurements as
q/2 for each channel instead of a channel transmitting quaternary digits instead. Thus in this case,
for
, (
q/2)(1 −
q/2),
q2/4). The number of bits required to reconstruct
from
(as two
n bit length strings) up to a probability of failure
ϵ,
where
q/2 is the error rate for each independent depolarizing channel in the CM. If we write the smooth max-entropy of Alice’s string conditioned on Bob’s in EM as
with
as errors in the EM, then
Equations (14),
(16) and
(18) gives the key length after error correction and privacy amplification as
where from [
9], we have the term
as the amount of information leaked to Eve due to error correction [
30] of the string
and
results from the quantum Leftover Hashing Lemma [
27].
3.2. Finite Key Analysis for LM05
In this work, we will consider the LM05 protocol with Bob’s choice for qubit preparation and measurement in the
Z bases is preferred (
pZ > pX) and Alice either encodes with anyone of her transformations with probability
c/4 or make measurements in the
X bases only with probability 1
− c. Furthermore, the deliberations ensue would be focused on the RR scenario. Alice’s and Bob’s choice of measuring 2
M(
n;
k) qubit pairs in the basis
X with probability 1 −
c results in
number of bits derived from EM and k for CM. Hence
pairs would be wasted due to bases mismatch when Alice measures in
X while Bob chooses
Z (notice that
qubits are wasted in [
9] for similar reasons).
Let us write the string Bob has in the EM and CM as
and
respectively as well as Alice’s as
and
A respectively. As described above, let us consider a
gedankenexperiment where all qubits are measured using
X basis (for CM), we can therefore write an uncertainty relation from
Equation (11) to bound Eve’s information as
Similar to earlier discussions, the first term in the left hand side of the above equation is the smooth min-entropy reflecting the number of bits contained in Bob’s string,
that are
ϵ-close to a uniform distribution and independent of Eve. The second term
reflects the correlation between Bob’s and Alice’s strings and gives the number of bits needed to reconstruct
from
up to a probability of failure
ϵ,
With
Qf as the error rate in EM, noting
and following
Equations (14),
(20) and
(21), the key length after error correction and privacy amplification is given by
4. Numerical Results and Comparisons
In making use of the key rate formulae of
Equations (19) and
(22) above, we need to first assume a value for the security parameter
ϵS, for which we set as 10
−10. Then, for a given value for errors in the CM (errors in EM is then immediately defined), setting the number for
M(
n, k), we determine the value
k which achieves the maximal value for secure key length. As
M(
n, k) approaches infinite for
n → ∞, following [
9] we could let
for some fixed
, so that
and consider secure keys within the infinite key regime. In the infinite key regime, the efficiency for the protocols SDC becomes
and for LM05 we have
It is worth noting that the ‘additional’ term
for amount of bits that can be derived from EM in LM05 becomes negligible in the infinite key regime and
. Furthermore, for this condition, it would be only the final term (related to error correction) that would determine how one protocol outperforms another.
4.1. Independent Channels
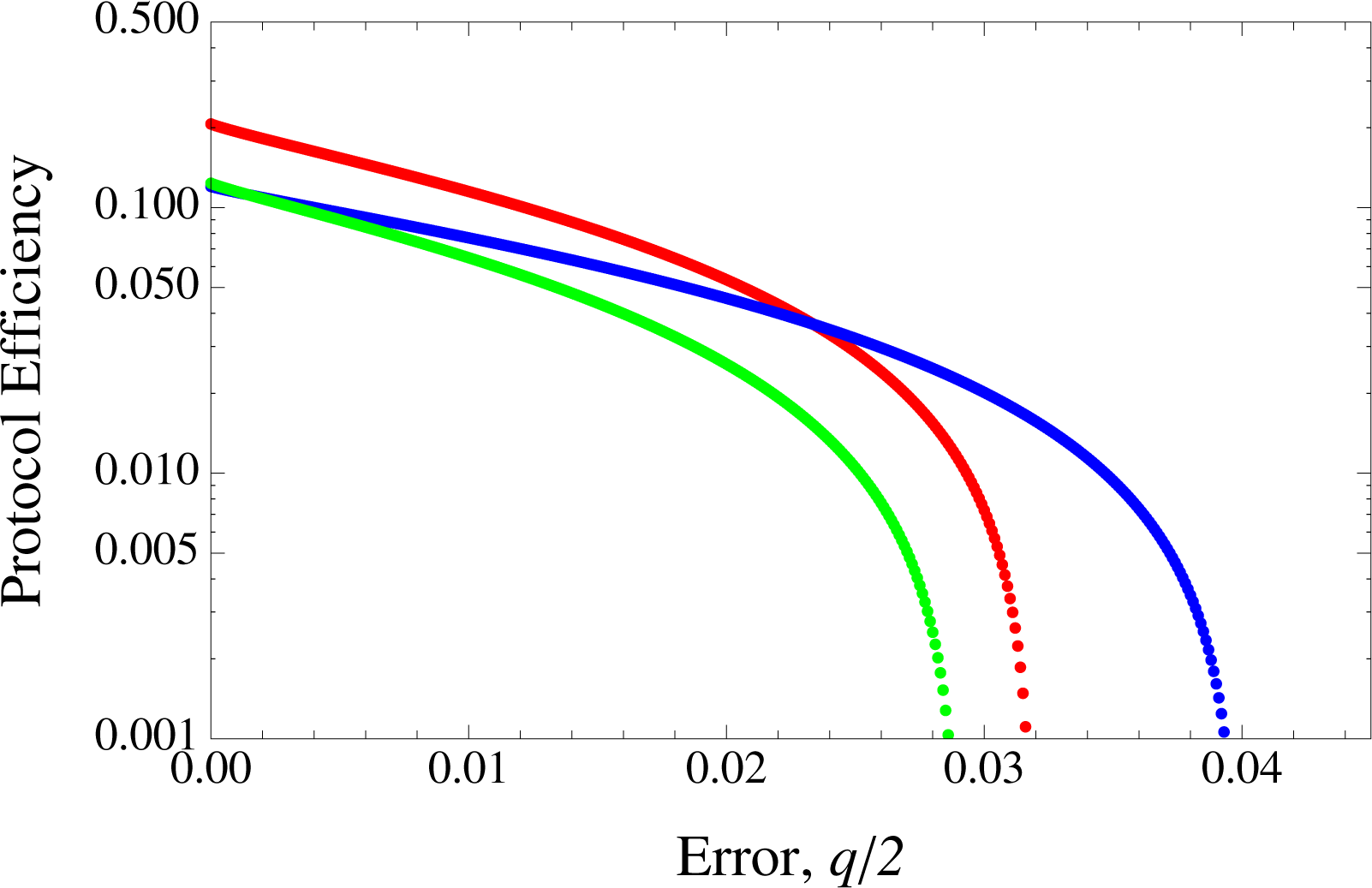
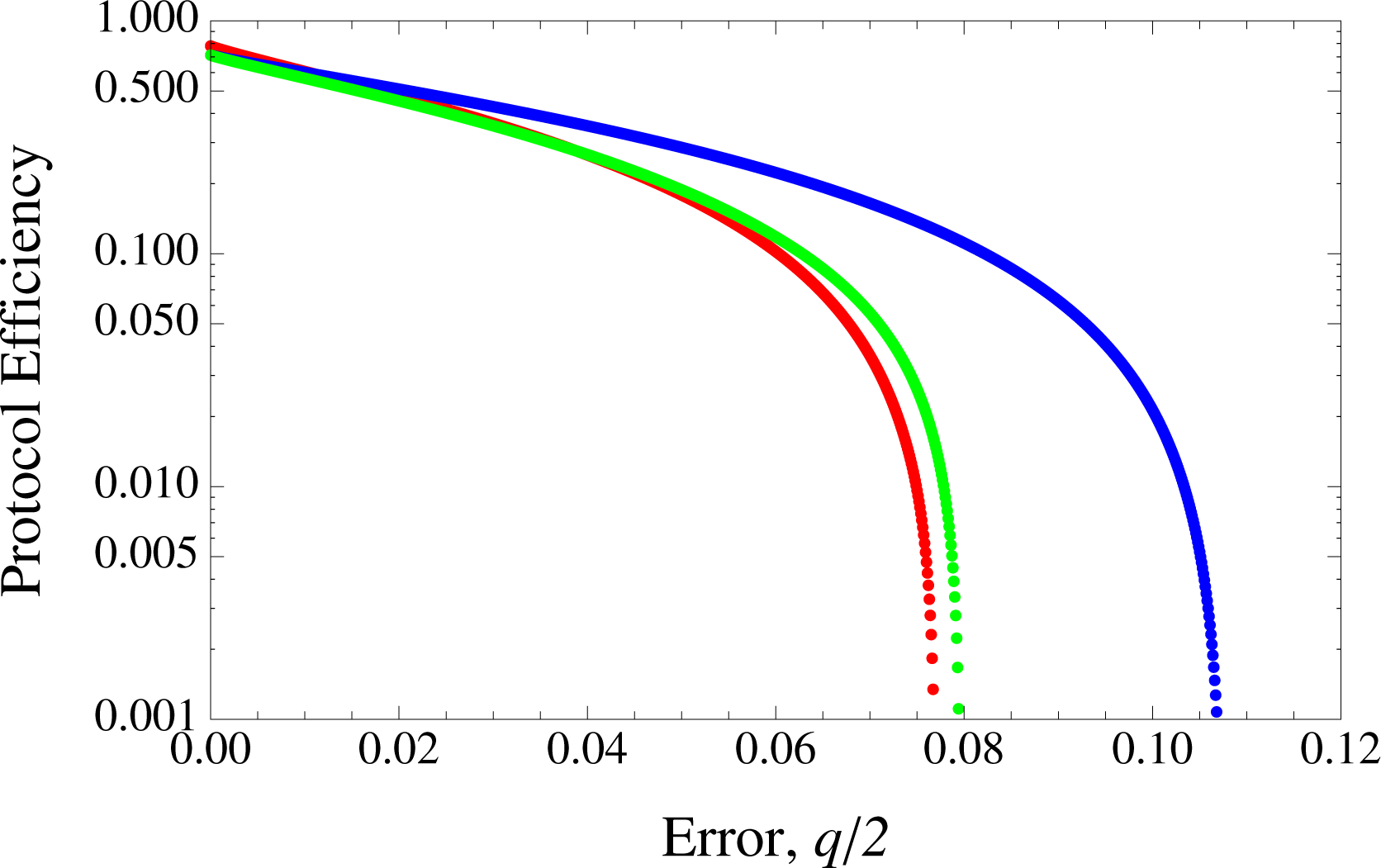
In
Figures 1 and
2, we present the results for implementations of the SDC and LM05 for independent channels compared to the asymmetrical BB84 in terms of protocol efficiency against errors. In this case, the error rates for SDC and LM05 in EM are given by 2
q/2(1 −
q/2) and (2
q −
q2)/4 respectively [
5].
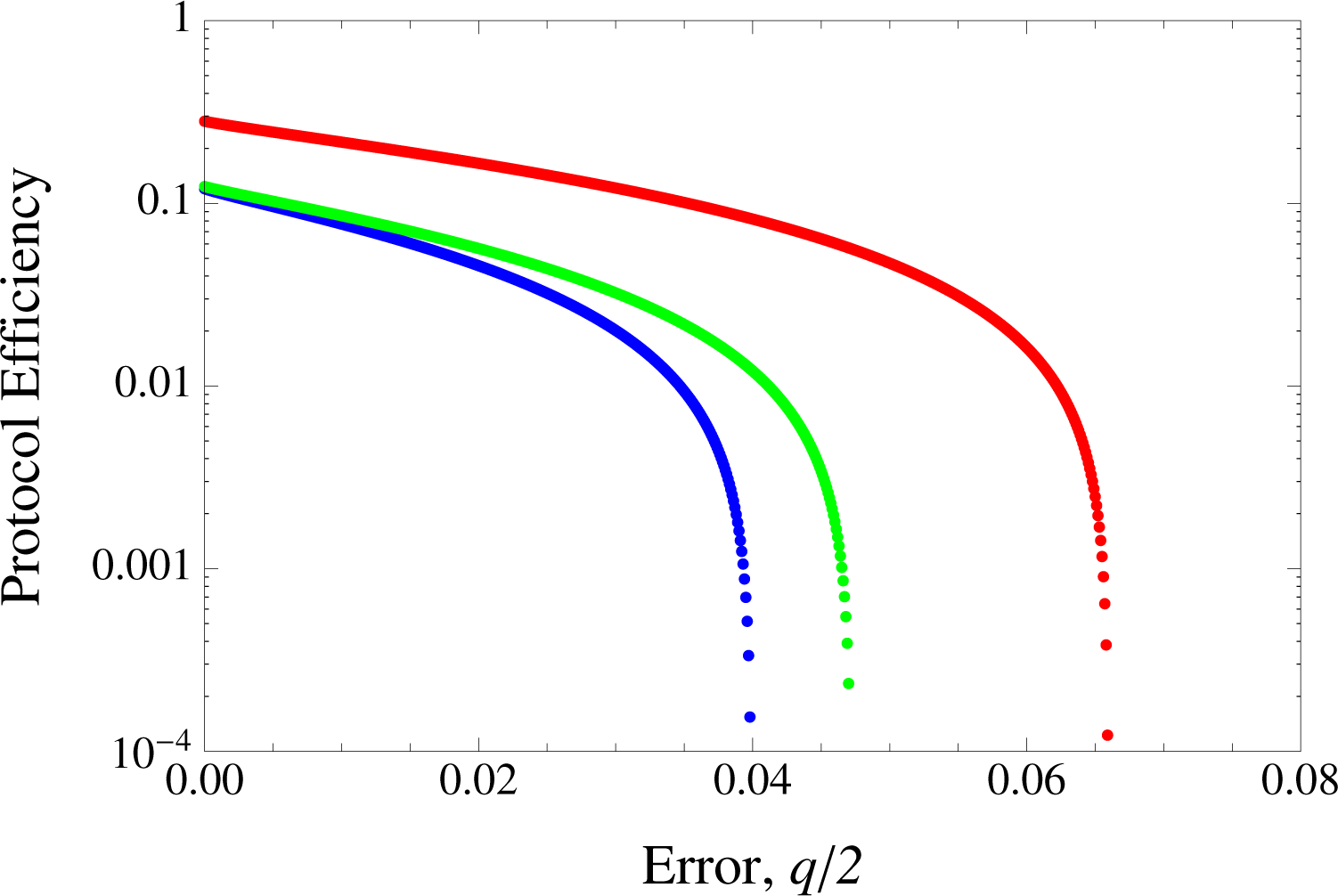
We can observe that there are particular regions where LM05 outperforms both SDC and BB84. Generally, this can be understood when considering the competing terms of the extra
contributing to LM05’s raw key versus the amount of bits to be discarded due to error correction. For LM05, this is given by
h2[2
q/2(1 −
q/2)], SDC’s
h4[(2
q −
q2)/4]/2 while for BB84, it is simply
h2(
q/2) where
with equality only at
q = 0 or
q = 1. The term
is most dominant for relatively small values of
n, hence LM05’s best performance of the three in
Figure 3 where
M(
n, k) = 10
4. In the same figure we see instances when the errors are big enough and outweighs the contribution from
, LM05 performs poorly compared to BB84. The error correction term for SDC is only very slightly better than that of LM05 in the infinite key regime, explaining why it still does not exceed LM05’s
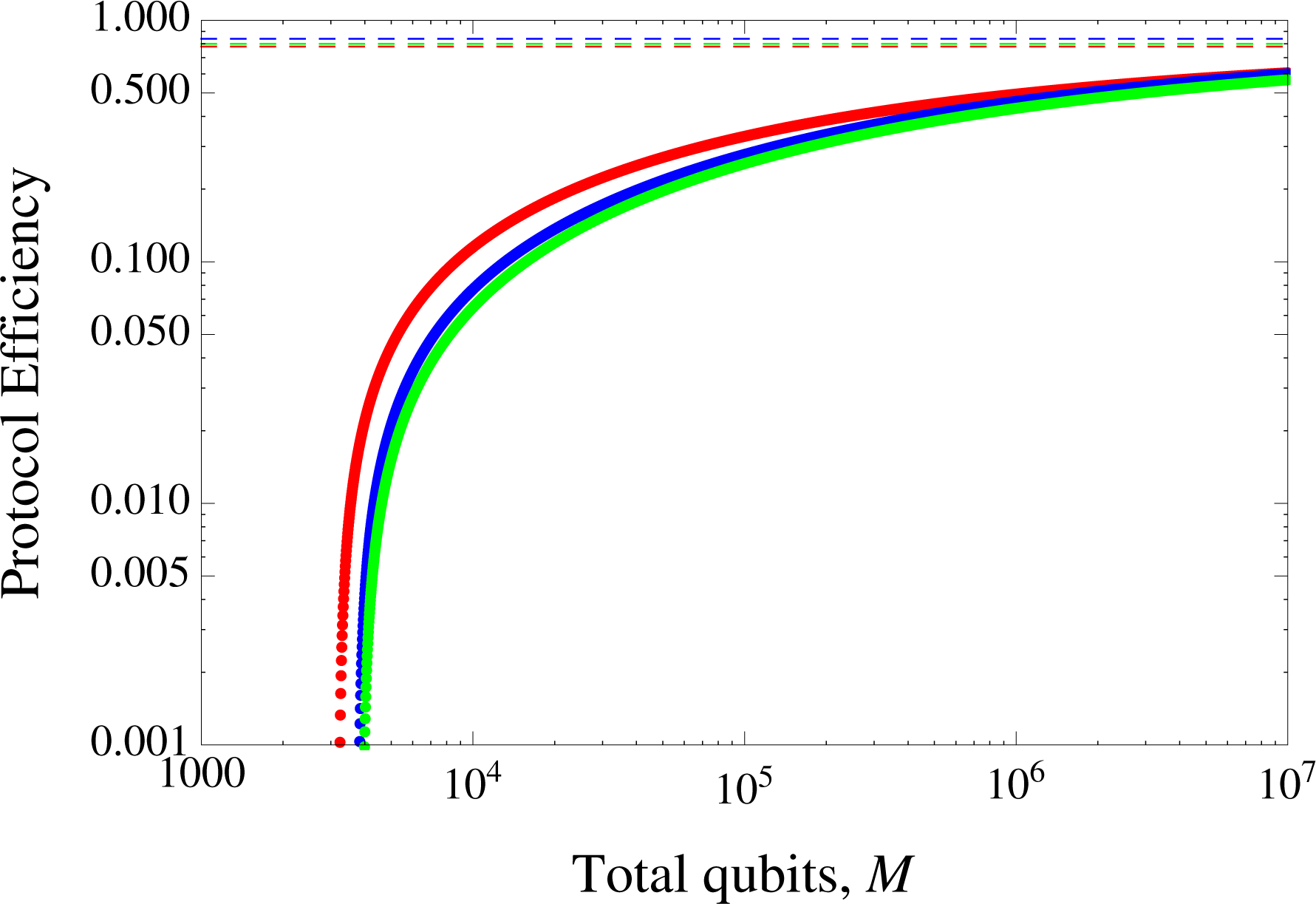
advantage in the finite key scenario here. Thus LM05 exceeds BB84 up to an error rate of about 2.7%. However, in
Figure 4 where the number of qubits used,
M(
n, k) = 10
7, LM05 exceeds BB84 only up to about 1% and SDC’s up to 3.8%. The plot of the protocols’ efficiency against
M(
n, k) for the error of 0.01 in
Figure 5 exhibits the convergence of the efficiencies as the number of qubits used increases up to 10
7. These results clearly emphasizes LM05’s determinism over the asymmetric BB84’s. It is worth recalling the fact that while LM05 claims deterministic status in terms of the absence for bases mismatch in EM, BB84 only approximates this (in the infinite key regime).
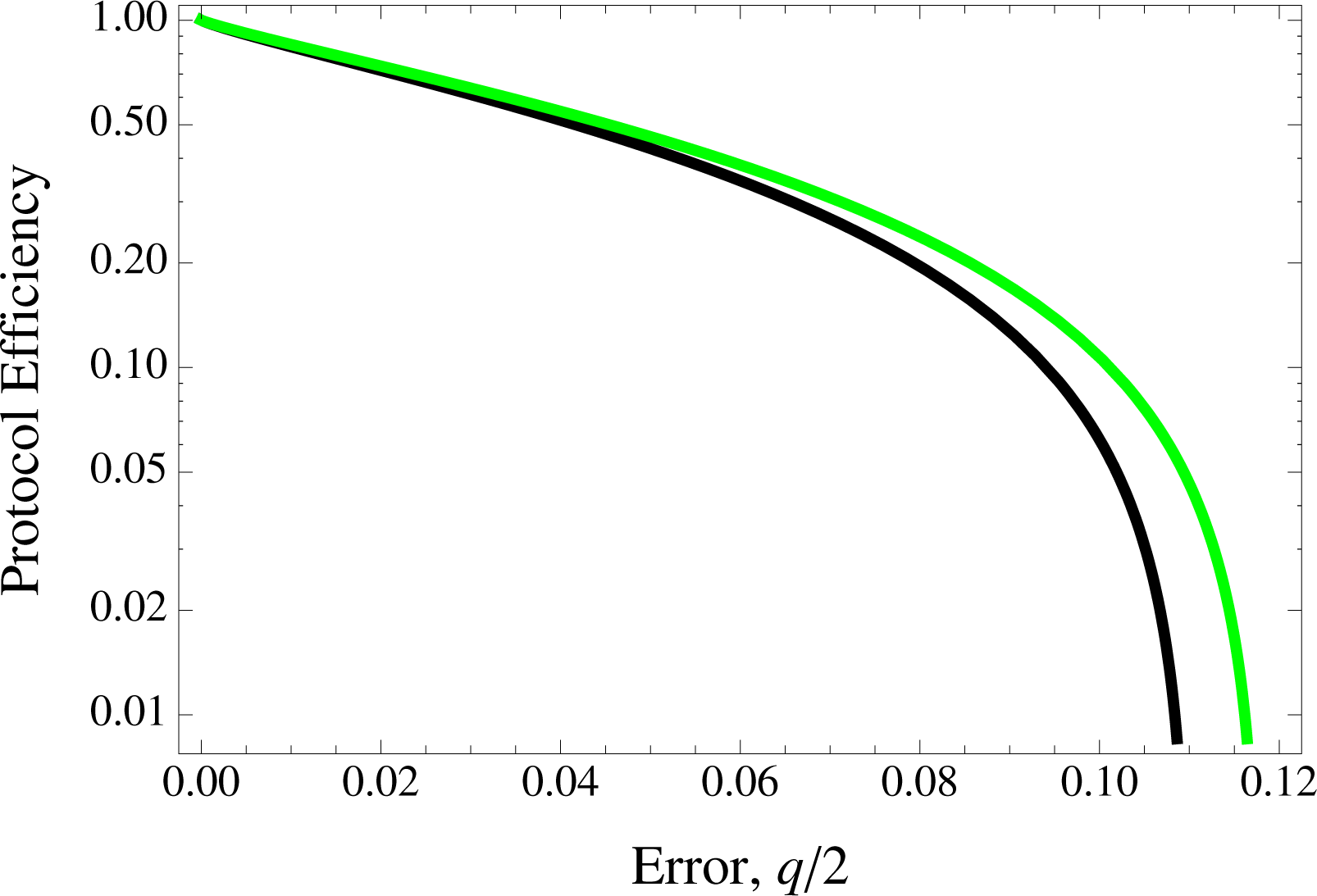
Figure 6 exhibits the case for the three protocols in the infinite key regime.
5. Conclusions
Protocols making use of bidirectional quantum channels like the ones described in this work have the interesting feature of encodings being embedded in a unitary transformation as opposed to the preparation of a quantum state as well as the added advantage of how a decoding procedure should not see wastage due to bases mismatch unlike the conventional BB84. By conventional we refer to the BB84 in its original form where the choice of bases is equiprobable, resulting in only half of qubits transmitted could be used as a raw key. While asymmetric BB84 is proposed as a remedy and is expected to not perform any less than the two “deterministic” protocols in the infinite key regime, the scenario for finite keys can be different; thus the motivation for this work.
Noting how the choice of relevant probability distribution for EM and CM is immediately analogous to the asymmetric BB84’s choice for the preferred basis and non preferred basis respectively in [
9], we extend the security proof based on purified versions of the SDC and LM05 in [
5] to the use of smooth entropies for a finite key analysis. We provide for secure key rates in terms of efficiency for the protocols.
In a relatively small number of qubits resources used (order of 104) as well as lower depolarization of channels, we observe an obvious advantage in LM05 due to having more bits for raw key purpose (derived from EM). This results from LM05’s encoding/decoding process which is independent of Bob’s choice of bases for measurement processes; which is in fact the ‘deterministic’ merit claim of the protocol. This advantage does however diminish in the region of asymptotically long keys when compared to BB84 (as well as the SDC).
The SDC is in some sense very similar to the asymmetric BB84 as bits for key purposes can only be salvaged when both Alice’s and Bob’s encoding and decoding processes respectively coincide (unlike LM05 where Bob’s measurements in CM would be equally meaningful as a decoding measurement in the EM). The only real advantage SDC has over BB84 would be in the correlated channels case due to the error correction procedure. However, one must bear in mind that while efficiency for LM05 and BB84 is measured as key bits per-qubits transmitted, SDC’s is measured as key bits per-entangled pairs used. Practically, this may not set to provide for a promising scenario as quantum memories become a necessity. Apart from our study of independent as well as a specific correlated channels, It is possible to consider variant cases of the latter beyond the one modeled here. Despite how any results thereof would depend strongly on the nature of the correlations, one may roughly deduce that having errors in EM lower than that provided by independent channels may very well result in a higher key rate for SDC and LM05 against BB84. Conversely, when the errors in EM is higher, it is likely the case that LM05 may not perform better than BB84 except for possible very small error rates. We conclude saying that a finite key analysis would be enlightening also for two-way QKD in the framework of continuous variable [
29].